The post Why Securing Autonomous Vehicles Must Start Now appeared first on RunSafe Security.
]]>In a recent episode of Exploited: The Cyber Truth, RunSafe Security CEO Joe Saunders joined Gabriel Gonzalez of IOActive to discuss the real-world vulnerabilities threatening connected cars and, more importantly, how the industry can build resilience from the ground up. Their insights shed light on both the dangers and the opportunities shaping the future of mobility.
As Joe puts it: “Vehicles are loaded with software. If you think about it, they are software systems with wheels as opposed to cars with individual components.”
When Connectivity Becomes an Open Door
Consider the humble telematics unit, the “black box” that connects vehicles to cellular networks. Gabriel Gonzalez and his team discovered that insecure MQTT configurations in fleet vehicles could let attackers intercept messages, track cars, and even take remote control.
“They found that they could actually fully control the car. It could unlock the car and get all the messages from the car,” Gabriel explained about the vulnerability his team discovered.
It’s a chilling reminder thatan entire fleet could be compromised by one misconfigured server.
This is a technical flaw and a business risk. For logistics companies, mobility providers, or public safety fleets, a cyber incident could mean service disruption, financial loss, and reputational damage.
The Expanding Attack Surface of Modern Cars
Today’s vehicles contain dozens of applications, from ECUs to infotainment systems and advanced driver assistance modules. “There are hundreds of millions of lines of code now on automobiles and vehicles today. There is a lot of attack surface and therefore a lot of opportunity for things to go awry,” Joe noted.
- Infotainment systems are no longer isolated—they often link directly to safety-critical functions.
- Shared, autonomous taxis introduce the risk of physical tampering by passengers.
- Software supply chain complexity means vulnerabilities can lurk deep within third-party components.
As Gabriel points out: “In a taxi or similar autonomous vehicles, you don’t know what the previous passenger did to the vehicle.” Even simple actions like moving a seat could become dangerous if controlled by an attacker during driving.
Software supply chain complexity adds another layer of risk. “In automotive, there are different types of companies. Some of them are just integrators. They don’t even own the code for the ECUs,” Gabriel explained, highlighting how vulnerabilities can originate far from the final vehicle manufacturer.
It’s not enough to patch vulnerabilities after the fact. Security must be part of the design of modern vehicles, not an afterthought.
Building Resilience Through Security-by-Design
So what’s the path forward? Both Joe and Gabriel emphasized one guiding principle: security-by-design.
Key strategies include:
- Build-time protection: Hardening software before it ever hits the road reduces exploitability.
- Software supply chain visibility: OEMs must demand transparency from tiered suppliers and enforce security standards.
- Memory safety and runtime defense: Preventing buffer overflows and code execution attacks is non-negotiable.
“Building security into those components prior to shipping can certainly reduce the exposure and the problem that you would suffer from having to patch components,” Joe emphasized. “Build-in security that protects the device at runtime, I think, ultimately is a good approach.”
Collaboration Is the New Competitive Advantage
One of the most encouraging shifts in the industry is cultural. Fifteen years ago, researchers were often ignored—or worse, threatened—for disclosing vulnerabilities. Today, manufacturers increasingly partner with researchers and CERTs to responsibly patch flaws.
“Maybe 15 years ago when you submitted a vulnerability, companies didn’t even know what we were talking about. Some companies were thinking that we were trying to get money out of them,” Gabriel recalled. Today’s reality is starkly different: “Nowadays, all the other certs and all these entities, they help with the process, especially with companies that are not well known and they are not too large.”
From DEF CON’s Car Hacking Village to Pwn2Own competitions, automakers now recognize that transparency and collaboration lead to stronger defenses. In fact, inviting researchers to “break” cars in controlled environments is becoming a badge of maturity, not weakness.
Lessons for Auto Industry Leaders
The race toward autonomy isn’t just about AI, sensors, or customer experience—it’s about trust. Without cybersecurity, the risks could outweigh the rewards. RunSafe Security’s 2025 Connected Car Cyber Safety & Security Index supports this. Consumers are more aware of cybersecurity risks than ever before. 70% of drivers said they would consider buying an older, less connected car just to reduce cyber risk.
For industry leaders, that means:
- Fleet operators should audit telematics and enforce strong authentication.
- OEMs must bake security into the SDLC and scrutinize software supply chain components.
- Researchers and security firms should continue to act as partners, not adversaries.
If we get this right, autonomous vehicles could transform mobility in ways we’ve only begun to imagine. If we get it wrong, the consequences will be measured in more than just software bugs—they’ll affect safety, privacy, and public confidence.
Stay Ahead of the Threat
At RunSafe Security, we help OEMs and suppliers build resilience from the inside out by hardening software and reducing exploitability without impacting performance.
Learn more in our white paper: Driving Security: Safeguarding the Future of Automotive Software.
The post Why Securing Autonomous Vehicles Must Start Now appeared first on RunSafe Security.
]]>The post Connected Cars, Connected Risks: Automotive Cybersecurity Is in High Demand appeared first on RunSafe Security.
]]>RunSafe Security’s new 2025 Connected Car Cyber Safety & Security Index reveals that consumers are more aware of cybersecurity risks than ever before and they’re ready to make buying decisions based on how automakers respond.
Listen to the Audio Overview
Consumer Awareness Has Outpaced Automaker Action
For years, automotive cybersecurity was treated as a technical issue best left to engineers. Today, it’s become a mainstream consumer concern. In our survey of 2,000 connected car owners across the U.S., the UK, and Germany, 65% of drivers believe remote hacking of a vehicle is possible, yet only 19% feel “very confident” that their car is protected.

That confidence gap is profound. Drivers perceive their vehicles as more vulnerable than other connected devices, such as smartphones, which receive regular security updates. And they’re right to be concerned. Recent years have seen everything from mass remote recalls to exploits that allowed researchers to take control of vehicles from miles away.
Safety, Not Privacy, Drives Concern
One of the most striking findings is that drivers now view connected car security as a matter of life and death. An overwhelming 79% say protecting their physical safety from cyberattacks is more important than safeguarding the personal data inside their cars.
Unlike traditional cybersecurity breaches that expose sensitive data, automotive hacks can directly compromise safety-critical systems like steering, braking, and acceleration. Consumers understand this risk and expect automakers to treat it with the seriousness it deserves.
Software Supply Chain Risks in the Spotlight
Modern vehicles aren’t built by a single company; they’re the product of a complex ecosystem of suppliers. Our survey found 77% of drivers recognize third-party components as cybersecurity risks, and 83% want transparency about software origins.
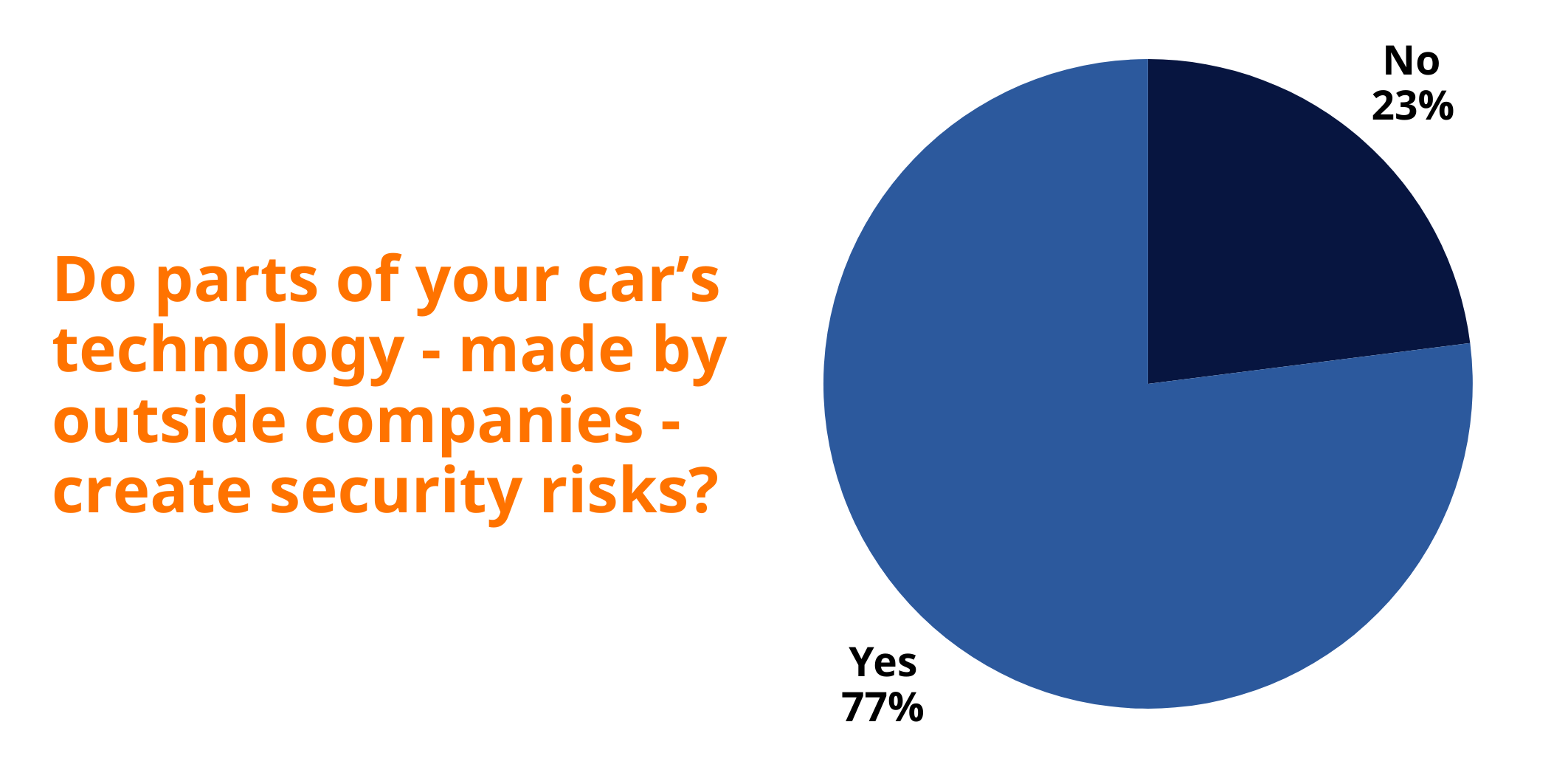
This demand for disclosure puts new pressure on automakers. Consumers don’t want vague assurances about safety and security. They want to know what’s inside their vehicles, where it came from, and how it’s being protected.
Automotive Cybersecurity as a Competitive Advantage
Perhaps the most important finding of all: cybersecurity now has the power to make—or break—a sale. Eighty-seven percent of consumers say strong protections influence their buying decisions, with 35% willing to pay premium prices for enhanced security.
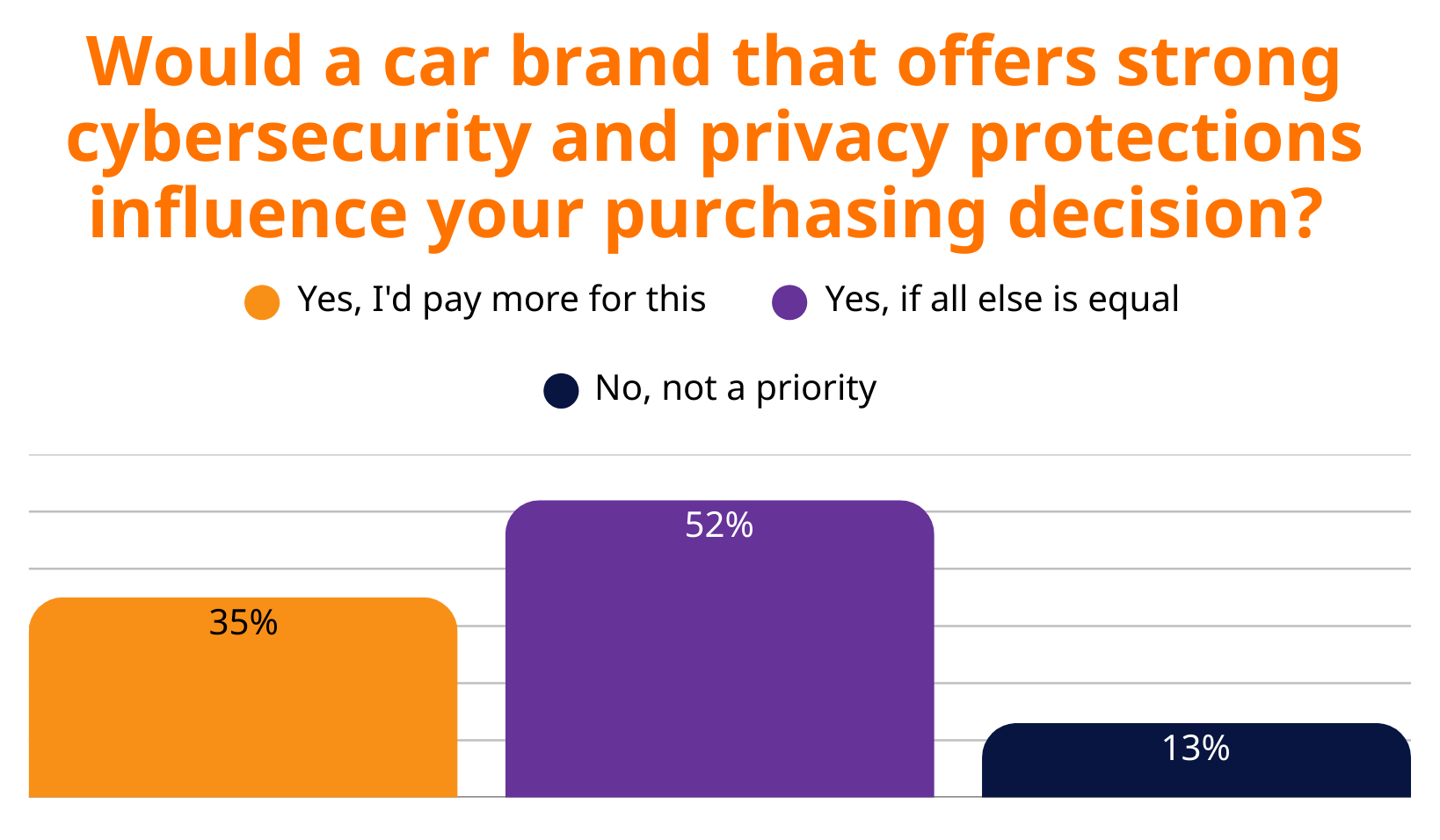
That’s a stunning shift in the way drivers view their cars. Security has moved from a behind-the-scenes technical feature to a frontline differentiator, on par with performance, comfort, and fuel economy.
Automakers that ignore this reality risk losing customers to more security-conscious competitors—or worse, driving them toward older, less profitable vehicles. In fact, 70% of drivers said they would consider buying an older, less connected car just to reduce cyber risk.
Automotive Cybersecurity Is a Defining Market Force
The 2025 Connected Car Cyber Safety & Security Index shows that automotive cybersecurity is a business imperative that directly impacts brand loyalty, market share, and revenue potential.
The message from consumers is clear: build security in, be transparent about software supply chains, and treat cybersecurity as seriously as safety. Those who act now will gain a durable competitive edge.
Download the full 2025 Connected Car Cyber Safety & Security Index to see the complete findings and insights for automakers and suppliers.
The post Connected Cars, Connected Risks: Automotive Cybersecurity Is in High Demand appeared first on RunSafe Security.
]]>The post Shifting Cybersecurity Left in Automotive: Why Secure by Design Is Critical for Modern Vehicles appeared first on RunSafe Security.
]]>With modern vehicles containing over 100 million lines of code and dozens of software components, attack surfaces are expanding. And as Joe points out early in the episode, today’s vehicles aren’t just “computers on wheels”—they’re entire software ecosystems in motion.
Listen the full episode:
Automotive Cybersecurity Risks in Software-Defined Vehicles
The convenience of real-time navigation, remote keyless entry, and seamless phone integration comes with a hidden cost: exposure. According to Joe, 92% of cyberattacks in the automotive space in 2024 were conducted remotely—many affecting millions of vehicles at once. Attackers are increasingly leveraging the very protocols that enhance user experience to manipulate vehicle systems, including brakes, steering, and door locks.
Complicating matters further is the long-standing reliance on the CAN bus protocol for in-vehicle messaging. While essential for transmitting signals between components like brake pedals and wheel systems, the CAN bus was never designed with security in mind, and its widespread use makes replacing it a monumental task.
“The traditional protocol and networking through the CAN bus does feel like a bit of a dinosaur in the automotive industry, and unfortunately, we can’t just get rid of it.” — Joe Saunders
Safety and Security: Two Sides of the Same Coin
When it comes to compliance, frameworks like ISO 26262 and its Automotive Safety Integrity Level (ASIL) classifications are essential. These standards guide manufacturers in assessing and minimizing the risks associated with both hardware and software failures, especially in systems where human safety is on the line.
From ASIL A (least critical) to ASIL D (most critical), these classifications help developers determine the necessary level of rigor required for different components. Joe uses the example of backup lights (ASIL A) versus fully autonomous driving controls (ASIL D) to illustrate how cybersecurity is increasingly being embedded into broader safety discussions.
Memory Safety and Real-Time Operating Systems
A key focus of the episode is the importance of memory safety in securing embedded systems like ECUs and infotainment units. Vulnerabilities in these systems can lead to catastrophic outcomes, especially when attackers exploit low-level memory bugs to gain control of vehicle operations.
RunSafe’s platform addresses this challenge head-on by hardening binaries against memory-based attacks without requiring changes to source code. This is especially relevant for real-time operating systems (RTOS) such as QNX and embedded Linux, which are commonly used across millions of vehicles.
Untangling the Automotive Supply Chain
One of the most pressing and complex challenges for automakers is managing their global, multi-tier supply chains. Software Bills of Materials (SBOMs) play a critical role here by offering visibility into the origin and composition of every software component.
“There are restrictions in the United States… you can’t get [automotive components] from China or Russia. How do you know that a software component is not built by an entity from one of those countries?” — Joe Saunders
The automotive supply chain doesn’t just involve hardware. It also includes firmware, embedded software, and third-party libraries. Without tools like SBOMs and strong vendor verification processes, organizations are vulnerable to both intentional backdoors and unintentional compliance violations.
Shift Security Left in Automotive Software Development
The episode concludes with a discussion around the concept of “shifting left”—embedding security early in the software development lifecycle instead of treating it as a post-production checkbox.
For automotive development teams, this includes:
- Incorporating security testing during the build and integration stages
- Using automated tools to validate compliance with ISO and ASIL standards
- Understanding the security posture of all platforms used (RTOS, embedded Linux, Android, etc.)
“It’s far easier to add in security as you’re building something than to find out you have a big exposure… and then go back and fix everything retroactively.” — Joe Saunders
This proactive approach reduces the likelihood of costly recalls and ensures that safety isn’t sacrificed for convenience or speed to market.
Final Thoughts: Future-Proofing Automotive Cybersecurity
Software-defined vehicles are reshaping transportation and with that innovation comes risk. As Joe highlights throughout the conversation, aligning cybersecurity with functional safety is essential for building trust, meeting regulatory demands, and ultimately protecting drivers and passengers.
If you’re building or securing vehicle systems, the time to shift left is now.
Related Articles:
- Driving Innovation Safely: 5 Ways to Secure Software-Defined Vehicles
- Buckle Up: Addressing Embedded Systems Security in the Automotive Software Supply Chain
- Secure by Design: Building a Safer Future Through Memory Safety
- Making Secure by Design Practical: How We’re Building Resilient Software
The post Shifting Cybersecurity Left in Automotive: Why Secure by Design Is Critical for Modern Vehicles appeared first on RunSafe Security.
]]>The post Driving Innovation Safely: 5 Ways to Secure Software-Defined Vehicles appeared first on RunSafe Security.
]]>“Automotive companies have become software companies, and their software practices are essential to drive innovation,” said Joe Saunders, Founder and CEO of RunSafe Security, in a recent webinar with Automotive IQ. “When safety and security are combined, it means we can build innovation going forward.”
For modern vehicles, that will mean addressing common vulnerabilities in software to not only minimize security risk, but to maximize innovation and ensure safety overall.
The Growing SDV Market and Its Security Implications
The growth of Software-Defined Vehicles (SDVs) is remarkable, with projections suggesting the SDV market will exceed $650 billion by 2030, representing 15-20% of the entire automotive ecosystem. This growth is driven by both consumer benefits and industry innovation.
For consumers, SDVs offer enhanced connectivity, personalized services, and improved safety features. From the industry perspective, autonomous driving capabilities, electric vehicle technologies, and over-the-air (OTA) update functionality are creating new service models and revenue streams for manufacturers.
However, this software revolution comes with significant security challenges. Modern vehicles now contain upwards of 100 million lines of code across 40-70 different software packages or applications. This dramatic increase in code creates an extensive attack surface that needs addressing.
The Current State of Automotive Cyber Attacks
Recent industry reports paint a concerning picture of the vulnerability landscape:
- 92% of automotive attacks in 2024 were remotely executed
- 70% of attacks could potentially affect thousands or millions of devices across different manufacturers due to common software and architectures
- 35% of attacks involved car system manipulation
These statistics highlight the growing risk of cyber threats to connected vehicles. “In the automotive industry, if you think about autonomous driving and attack vectors that could affect car system manipulation, I think everyone would agree that security is really about safety,” Joe said. “With more software, it means we have a chance to find ways to generate more security for these applications.”
3 Common Vulnerabilities in Software-Defined Vehicles
Vulnerabilities are commonly found in three areas of SDVs: electronic control units, Advanced Driver Assistance Systems (ADAS), and infotainment systems. Infotainment systems in particular are becoming a bigger risk, due to new connectivity features.
Infotainment Systems
Hacks against vehicle infotainment systems were in the news in early 2025. Over a dozen vulnerabilities were discovered in a Mercedes-Benz infotainment system. Security flaws in Subaru’s Starlink-connected infotainment system allowed hackers to remotely control the vehicle, including turning it on and off, unlocking it, and more.
Hackers can gain access to data and location information through these systems, but more concerningly, as recent examples show, infotainment systems are often used as an on-ramp to access other critical vehicle systems.
“Not all vehicles today are segmented from a security perspective and people can jump from one component to the other,” Joe said.
Electronics Control Units (ECUs) in Automobiles
Vulnerabilities in real-time operating systems (RTOS) can be exploited once attackers gain access to a vehicle’s systems. “ECUs are an easy target once an attacker is on board,” Joe said.
Because ECUs are most commonly programmed in languages like C and C++, they are susceptible to memory safety vulnerabilities. An attacker who exploits a memory safety vulnerability in the ECU firmware could take runtime control and cause erratic vehicle behavior.
Advanced Driver-Assistance Systems (ADAS)
Advanced Driver-Assistance Systems (ADAS) are similarly susceptible to memory safety vulnerabilities. “In many cases, in the underlying software, like ADAS, we have seen that the vulnerabilities are related to memory safety vulnerabilities.”
ADAS enhances safety using sensors, cameras, radar, and complex software. A successful attack could alter sensor data or decision-making algorithms, endangering the vehicle’s safety. For example, memory corruption in sensors could result in incorrect object detection, leading to collisions or other dangerous situations.
Case Study: Tesla Vulnerabilities

An example of a memory-based vulnerability in automotive software is CVE-2022-42431, a critical buffer overflow vulnerability discovered in Tesla Model 3 vehicles. A buffer overflow is a classic memory safety vulnerability that ultimately allows an attacker either to escalate privileges or even gain the ability to execute arbitrary code.
The implications are severe: “What that means is they can ultimately leverage the existing code and do something that wasn’t originally intended by the original developer for that feature,” Joe said. “These kinds of vulnerabilities are very critical and ultimately get rated through the services as the highest severity scores.”
These examples illustrate how memory safety vulnerabilities—classic issues in software developed using “memory unsafe” languages like C and C++—pose significant risks to vehicle security and, by extension, passenger safety.
Best Practices for Securing Software-Defined Vehicles
1. Implement Software Development Lifecycle Practices
Over the past decade, the industry has seen dramatic improvements in the software development lifecycle. Automotive manufacturers should continue to enhance these practices by:
- Implementing secure coding standards
- Conducting thorough threat modeling
- Utilizing automated vulnerability detection tools
- Integrating security protections into the development process
2. Adhere to Automotive Safety and Security Standards
Standards like Automotive Safety Integrity Levels (ASIL), which define four levels of safety classification based on risk to passengers, play a crucial role in ensuring vehicle security. These standards, along with industry frameworks like ISO 26262 and AUTOSAR, provide essential guidelines for secure development.
3. Deploy Runtime Protection Systems
One of the most effective security strategies is implementing runtime memory protection at the software build stage. This approach eliminates the entire class of memory-based vulnerabilities, which account for 40-70% of all vulnerabilities in these systems, without requiring code rewrites or adding system overhead.
4. Leverage Over-the-Air Updates
OTA update capabilities provide a mechanism for addressing vulnerabilities and deploying security patches throughout a vehicle’s lifecycle, allowing manufacturers to continuously improve security posture even after vehicles have been deployed to customers.
5. Manage Software Supply Chain Risk
With the complexity of automotive software supply chains, addressing and mitigating third-party software risks and risks from open source software is crucial. Steps include:
- Requiring suppliers to provide Software Bills of Materials (SBOMs)
- Conducting security assessments of third-party components
- Establishing transparent communication channels with suppliers
- Proactively identifying and addressing vulnerabilities in the supply chain
The Road Ahead for Automotive Software Security
As the automotive industry continues its transformation toward software-defined vehicles, security must be a foundational consideration rather than an afterthought. By implementing secure development practices, adhering to industry standards, deploying runtime protections, and managing supply chain risks, manufacturers can create vehicles that are both innovative and secure.
The key takeaways for automotive manufacturers and OEMs:
- ECUs, ADAS, and infotainment systems are particularly vulnerable to memory safety vulnerabilities
- Software security is now an undeniable component of vehicle safety
- Focusing on safety and security today will enable innovation and resilience against future risks
By addressing these challenges head-on, the automotive industry can continue to drive innovation while ensuring the safety and security of the vehicles that consumers depend on every day.
The post Driving Innovation Safely: 5 Ways to Secure Software-Defined Vehicles appeared first on RunSafe Security.
]]>The post Buckle Up: Addressing Embedded Systems Security in the Automotive Software Supply Chain appeared first on RunSafe Security.
]]>
If you’ve made a recent trip to San Francisco, it can feel like you’ve stepped into the future when you spot an autonomous vehicle navigating the streets, picking up passengers, and cruising the city’s famous hills. But as autonomous vehicles move from concept to reality and vehicle connectivity becomes the norm, embedded systems, the technology that makes it all possible, are an often overlooked but critical piece of automotive security.
Citing national security concerns, the Biden Administration proposed two bans in September 2024 that draw attention to the software supply chain within the automotive industry and the potential risks of autonomous and connected vehicles. Because modern cars include microphones, cameras, GPS tracking, and more, there is a very real threat that nation-state actors could exploit software to conduct surveillance, collecting data on vehicle movements, for example. Further, it’s possible that a bad actor could gain access through a software backdoor and disable an entire fleet of vehicles at one time, posing an immediate risk to drivers and disrupting society.
The bans, if approved, seek to address this, first by prohibiting new vehicle software originating within China or Russia by 2027 and second banning the imports and sales of vehicles with automated driving hardware created in the countries to go into effect by 2030.
While the implications of the bans and others like it will shake out in the years ahead, the reality for today is that we need solutions that will keep autonomous and connected vehicle software resilient and secure against known threats and those yet to come.
Why Embedded Systems Matter for Automotive Security
Embedded systems are integral to modern vehicles, processing sensor data and controlling everything from engine performance to collision avoidance. However, as vehicles become more connected and automated, embedded systems face mounting security challenges and are vulnerable to a range of threats, including unauthorized access, data breaches, and potential manipulation of vehicle controls.
“The automobile is becoming more and more of a computer on wheels and, in addition, it’s connected to a lot of different things,” explained Dave Salwen, VP of Embedded Systems at RunSafe. “While its use is great for the consumer with new features and new capabilities, it’s becoming more and more software-centric. More software vulnerabilities are coming into the system and more vulnerabilities can be exploited by bad actors.”

One of the biggest threats to embedded systems is memory-based vulnerabilities. Memory safety is a foundational aspect of software development, ensuring that programs operate reliably and securely without accessing or manipulating memory incorrectly.
Vehicle software is vulnerable to memory safety threats in four key systems:
-
- Electronic Control Units (ECUs) in Autonomous Vehicles: Responsible for critical driving functions (e.g., braking, acceleration, steering). A buffer overflow attack could lead to unauthorized access and control and erratic vehicle behavior.
- In-Vehicle Infotainment Systems (IVI): Infotainment systems need to be safeguarded from heap-based overflow vulnerabilities, which could be exploited to execute arbitrary code and gain access to other vehicle systems.
- Advanced Driver Assistance Systems (ADAS): ADAS software needs to be protected from stack-based buffer overflows that could alter sensor data or decision-making algorithms, endangering the vehicle’s safety.
- Connectivity Systems: Connectivity through 4G/5G cellular, bluetooth, wireless CarPlay/Android Auto open the door for memory corruption attacks that can lead to remote access to vehicles.
How to Secure Automotive Embedded Systems and the Software Supply Chain
The need for automotive software supply chain integrity, data security, and automotive safety standards like ISO 26262 and the emerging ISO/SAE 21434 are driving the industry to seek solutions for security and compliance. Here’s where to start.
1. Prioritize Software Bill of Materials (SBOMs) to Evaluate the Software Supply Chain
Software Bill of Materials (SBOMs) are essential tools for demonstrating regulatory compliance, tracking all components, libraries, and modules used in software applications, and enabling quick responses to security concerns. With the proposed bans from the Biden Administration on the horizon, SBOMs will be invaluable for vehicle manufacturers needing to evaluate their software supply chain to ensure they are not incorporating prohibited software. SBOMs provide detailed inventories of software components within a software binary, enabling quick compliance assessments.
2. Secure Embedded Systems from the Ground Up
Secure by Design principles are no longer optional in automotive software development. As vehicles become more complex and interconnected, retrofitting security measures after development is both costly and ineffective. Following Secure by Design principles will include threat modeling during design phases, implementing secure coding practices, conducting regular security testing, and building in mechanisms for secure updates throughout the software lifecycle.
3. Adopt Automated Vulnerability Identification and Advanced Code-Hardening Techniques
Fortifying critical systems against cyber attacks, like braking and steering in an autonomous vehicle, means protecting the millions of lines of code that allow them to function. Automated vulnerability identification and code-hardening protects software against attacks that could compromise vehicle operations and safety while reducing the attack surface.
Specifically, memory relocation techniques prevent memory-based vulnerabilities from being exploited in embedded systems. Known as load-time function randomization, the technique ensures that each instance of the software has a unique memory layout, making it extremely difficult for attackers to predict the location of specific functions, proactively neutralizing common exploit techniques like Return-Oriented Programming (ROP) and buffer overflow attacks.
The Road Ahead: Building Secure and Resilient Vehicles
The increased focus on embedded systems and the automotive software supply chain is a positive one. Ultimately, adopting stronger cybersecurity practices now is an enabler of new vehicle technology, greenlighting innovation and allowing vehicle manufacturers and suppliers to protect their products and customers from the growing landscape of cyber threats.
Learn more about techniques for using SBOM data to track and mitigate security risks in our guide to creating and utilizing SBOMs.
The post Buckle Up: Addressing Embedded Systems Security in the Automotive Software Supply Chain appeared first on RunSafe Security.
]]>The post The State of Auto Cybersecurity: Connected Vehicles Have Hackers Accelerating Attacks appeared first on RunSafe Security.
]]>The following five paragraphs are excerpted from chapter 15 of SAE’s Cybersecurity for Commercial Vehicles, titled “Law, Policy, Cybersecurity, and Data Privacy Issues.” The content was written by Simon Hartley. The entire book, edited by Gloria D’Anna, is available here.
A Quick Glance in the Rearview Mirror
In 2015, the first widely-viewed public demonstration of remote vehicle exploitation (via the infotainment system) was made by cybersecurity researchers Chris Valasek and Charlie Miller. The two men astonished onlookers by taking control of a Jeep’s dashboard functions, steering, transmission, and brakes from 10-miles away, as the Jeep continued to drive down the highway. Needless to say – this event led to front page coverage around the world.
The potential for that exploit to be repeated on any of the 1.4 million Fiat Chrysler Automobile (FCA) vehicles on the road led to the world’s first cybersecurity safety recall. A year later, the research duo followed up with a local vehicle exploit (via the USB and CAN Bus) showing non-connected vehicles to have vulnerabilities at highway speeds. This revelation answered many naysayers that had sought to downplay the breadth of attack surfaces in legacy vehicles (and narrow industry focus only to the protection of future model years).
The researchers described the work as “extremely difficult, time-consuming, and expensive,” but they had achieved their breakthroughs alone and mostly with self-funding, likely inferring that skilled and full-time adversaries could pull off similar attacks with ease.
Hackers Discover Vulnerabilities in Many Vehicle Makes and Models
Since that first public vehicle hacking demonstration, numerous new vulnerabilities in different manufacturers have been found. For example, Tesla and General Motors (GM); in commercial vehicles, by car thieves using laptops; and most recently in smartphone apps used for keyless entry…hackers do not need to build up their own expertise or experience, instead they rely on tools created by a much smaller group of experts, to download exploits or run them as software as a service (SaaS) from the dark web.
Risks to commercial fleets have also become apparent in recent years. That’s because commercial fleets aggregate large groups of similar vehicle models, making them relatively homogenous targets. The asymmetry of hacking economics means that defenders must defend all attack vectors, but an attacker needs to find just one vulnerability and can use it directly or share with others.
Are Connected Cars Worth the Security Risks?
So here we are in 2018, facing more and more autonomous vehicles in test mode and connected cars in use. With such features as enhanced GPS, location and maintenance live recording, reminders, driving assistance, and Wi-Fi, Mordor Intelligence estimates that 75 percent of the 92 million cars shipped globally in 2020 will be connected.
By definition, a connected car has more control units, computing power, lines of code and wireless connections than a “non-connected” car – all of which make it more susceptible to attacks. By exploiting a weakness, a hacker could take control of the brake or steering systems, show incorrect information on the dashboard dials, or grab driver data.
Frost & Sullivan estimates that cars will require 200-300 million lines of code in the near future. It’s difficult to create bug-free software in the best of circumstances, let alone when dealing with the amount of code required to power autonomous vehicles. More code means more opportunity for bugs and mistakes, such as buffer overflows, which can be exploited. It’s also worth noting that there is no single controlling entity that has cognisance over the source code for all components. Code is written by different developers, tested by a number of entities, and installed by different suppliers. Malware can be included in any step on this supply chain.
Additionally, the increased use of smartphone apps to run certain functions by interfacing with connected cars introduces vulnerabilities, and researchers have already demonstrated a number of weaknesses that can enable scaling of attacks. Then there’s the need for constant updates to the software that runs the various components and systems. Such updates can be overlooked, leaving known glitches unpatched. But even when all software is up to date, hackers are skilled enough to can also infect routine updates.
Go Beyond Traditional Intrusion Detection Auto Cybersecurity with RunSafe
Yes, connected vehicles can enable safety, mobility, and environmental efficiencies – along with entertainment options never once thought possible in a car. But this growing trend of adding components and the software that enables them introduces vulnerabilities that even manufacturers do not understand the breadth of. intrusion detection solutions.
RunSafe Security uses a patented transformation process to cyberharden vehicle components, reducing opportunities for attackers to inject malware into software modules that control ECUs, CAN BUS, telematics, infotainment, and other systems. It stops attacks that bypass traditional encryption, network, and endpoint solutions – without requiring access to source code or adding software, services, or hardware.
Request our whitepaper here to learn how we transform embedded software and devices: https://runsafesecurity.com/request-whitepaper/
The post The State of Auto Cybersecurity: Connected Vehicles Have Hackers Accelerating Attacks appeared first on RunSafe Security.
]]>

