The post Is Your Security Helping or Hurting Your Product Line Profitability? appeared first on RunSafe Security.
]]>Security can either be your biggest margin killer or your most powerful profit enabler. From the beginning, our goal at RunSafe has been to put control back into the hands of the defenders. And that means building solutions that meaningfully reduce risk across your product portfolio. As cyber defense champions, we can quantify economic benefits to security solutions that improve your product line profitability.
Listen to the audio overview below:
The Cost of Reactive Security
Security incidents now average $4.88 million per breach according to IBM’s 2024 Cost of a Data Breach Report, but that figure only scratches the surface. The real damage comes from the operational drag that reactive security creates long before any breach occurs.
Consider an example from a software manufacturer, one of RunSafe’s customers. Implementing RunSafe’s runtime code protection saved the company over $1 million per year, with reduced patching representing the largest cost saving.
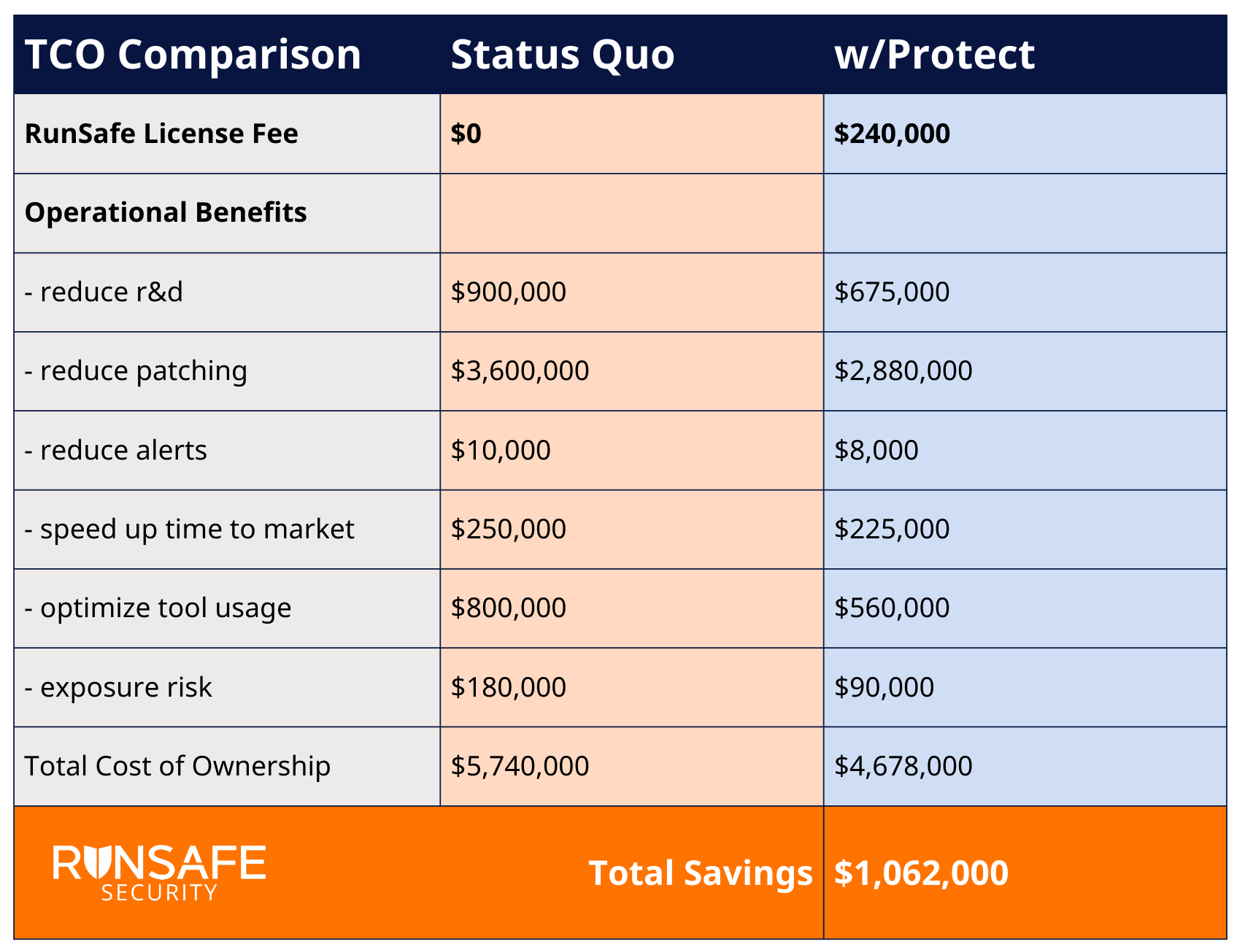
Calculate your potential Total Cost of Ownership here.
Being proactive about security (deploying RunSafe Protect) rather than reactive (relying on patching) saved this company a significant amount of money. And it’s not just money. It’s also about opportunity cost.
The hidden costs of reactive security include:
- R&D Resource Drain: Effort is put into code scanning/review, penetration testing, subsequent remediation, and then coordinated release of patches to customers. These issues spawn lengthy retesting cycles and gobble up R&D resources that would otherwise be able to work on new features and products.
- Market Access Barriers: Companies lose significant contracts when their security posture can’t meet customer requirements. Consider how Zoom was initially excluded from certain DoD environments due to its security posture not meeting baseline requirements.
- Developer Productivity Loss: Engineering teams spend 30-40% of their time on security remediation instead of innovation.
Competitive Disadvantage: Slower release cycles compared to competitors, who ship features faster with built-in security.
Are You Spending to Patch or Investing to Prevent?
The problem with scan-and-patch security is inefficiency and ineffectiveness. For example, in our work on embedded devices, we see on the daily that memory safety vulnerabilities account for 40-70% of identified vulnerabilities in embedded code.
A study by North Carolina State University shows that for Linux operating system software over a 10-year period, only 2.5% of memory vulnerabilities were identified in vulnerability scanning tools. This shows us that scanning, a widely adopted practice, leaves one vulnerable.
Similarly, multiple studies say companies and users generally aren’t patching on time due to a lack of knowledge, the effort to coordinate change, the process slowing progress, fear of breaking the current setup, and other barriers. At its best, patching is reactive. More often, costs and other barriers mean patching is delayed, if done at all.
Even when vulnerabilities are found, patching faces massive barriers:
- Coordination Costs: Cross-team alignment, testing cycles, and deployment logistics
- Customer Resistance: Nobody wants to patch, especially when it might break existing functionality
- Timing Mismatches: Critical vulnerabilities discovered right before major releases
- Risk Accumulation: Delayed patches create growing attack surfaces
The math is brutal. If you’re patching reactively, you’re not just paying for the patch—you’re paying for the disruption, the delays, the testing cycles, and the opportunity costs of having your best engineers chasing down someone else’s vulnerabilities instead of building your next breakthrough feature.
The Runtime Security Advantage
Here’s where the economics flip completely. Runtime security—integrating code protection directly into your development process—transforms security from a margin killer to a competitive advantage.
RunSafe’s approach demonstrates this transformation. RunSafe Protect eliminates an entire class of vulnerability common in embedded software to defend your software from the very beginning and dramatically reduce your attack surface. Protect safeguards your systems during runtime without compromising performance or requiring post-deployment modifications.
The results speak for themselves. RunSafe deployed code protection to dramatically reduce the attack surface by 70% for an industrial automation leader deploying HMI products. The company was able to measurably reduce risk and protect software in very difficult-to-update facilities within critical infrastructure.
Understand the total exposure of your embedded software and quantify your risk reductions with RunSafe Protect. Give your code a scan.
The broader business impact includes:
- Faster Time-to-Market: No more security-driven delays in release cycles
- Predictable Operations: Controlled patch timing instead of emergency responses
- Enhanced Customer Relationships: Fewer disruptions, more reliable products
- Engineering Focus: Teams building features instead of fixing vulnerabilities
- Market Differentiation: Security as a selling point, not a compliance checkbox
Security as a Revenue Driver
Beyond cost savings, the right security approach actually opens new revenue streams. Companies with robust security profiles win contracts that others can’t touch. In RunSafe Security’s 2025 Medical Device Cybersecurity Index, we saw that 83% of healthcare organizations now integrate cybersecurity standards directly into their RFPs and 46% have declined to purchase medical devices due to cybersecurity concerns. A lack of security quickly leads to lost revenue in this competitive market.
On the other hand, it opens the door to increased product line profitability. 79% of healthcare buyers are willing to pay a premium for devices with advanced runtime protection. Similarly in the automotive industry, RunSafe’s 2025 Connected Car Cyber Safety & Security Survey, 87% of survey participants said a car brand that offers strong cybersecurity and privacy would influence their purchase decision, with 35% willing to pay more.
Customers are saying security is worth the cost. That’s good news for product teams looking to make smart investments.
The Bottom Line
Security doesn’t have to be a necessary evil that drains profitability. When implemented early, systematically, and with business impact in mind, security becomes a competitive advantage that drives margin improvement and sustainable growth.
The companies that figure this out first will have operational advantages their competitors can’t match: faster development cycles, lower operational costs, stronger customer relationships, and access to markets that others can’t reach.
Can you afford to keep subsidizing reactive security approaches that are killing your margins and slowing your growth?
See how runtime security can transform your product line profitability. Calculate your potential ROI with RunSafe Protect or schedule a call with our team to discuss your specific business impact.
The post Is Your Security Helping or Hurting Your Product Line Profitability? appeared first on RunSafe Security.
]]>The post Securing the ICS/OT Software Supply Chain: What Schneider Electric’s Discovery Means for Industrial Systems appeared first on RunSafe Security.
]]>Recently, Andy joined us for a discussion on defending against software supply chain risks and how Schneider Electric is tackling a hidden crisis in ICS/OT security. What he shared confirmed what many in the industrial security space have suspected but lacked the data to prove. While organizations focus heavily on perimeter security, the most dangerous threats are often already embedded within their systems.
Memory Safety: The Root of Industrial Software Supply Chain Attacks
Memory safety is a topic Andy has been interested in for awhile, but it came time to prove just how significant—or not—the issue really was. Looking at all of the publicly disclosed vulnerabilities Schneider Electric had across project lines, Andy found that “memory safety was easily the largest percentage of recorded security issues that we had.”
94% of these weaknesses come from third-party components. Though that number is eye-opening, it’s not as surprising as you might think. Products today contain a significant amount of third-party or open source code.

Now, it’s important to note that this isn’t just an isolated case. We know that motivated threat actors, like Volt Typhoon and Salt Typhoon, are targeting critical infrastructure. We also know that they are using both known memory-based vulnerabilities and zero days to do so.
Consider the infamous Urgent 11 vulnerabilities that affected countless industrial control systems. Six of those eleven vulnerabilities were memory-based, and they provided attackers with significant leverage to compromise devices across multiple industries and vendors.
Memory safety vulnerabilities are widespread in software, and they are in your software supply chain too.
The Asymptotic Security Problem
Andy Kling brilliantly articulated what I consider the fundamental challenge in securing industrial systems: “We have to shift left and find out where we can improve in our own processes. But it’s also asymptotic, meaning more and more effort is going to go in to find fewer and fewer of these things.”
This asymptotic security curve means that traditional approaches yield diminishing returns. You can invest millions in better static analysis, more thorough testing, and improved development practices, yet still miss critical vulnerabilities. This isn’t to say these practices aren’t valuable—they absolutely are—but they’re insufficient on their own.
For example, some reports suggest that static analyzers for C/C++ miss 47%–80% of real vulnerabilities. Think about that: the tools we rely on for security validation are missing a significant scope of potential vulnerabilities.
This challenge is compounded by the staggering scale of industrial software. During our panel, Andy revealed that just one Schneider Electric system contained approximately 20 million lines of code—and that doesn’t even include the operating system underneath. Across their entire product portfolio, they estimate half a billion lines of code. In such vast codebases, vulnerabilities are inevitable.
The traditional approach to this problem—finding bugs and patching them—breaks down in industrial environments for several reasons. First, patches take time to develop, test, and deploy. Second, many asset owners can’t afford downtime for updates or are running critical systems that simply can’t be taken offline. Third, equipment can remain in operation for decades, far beyond standard support lifecycles.
The reality is we can’t rewrite all legacy code, and we can’t patch our way out of this problem.
A Strategic Framework for Embedded Security
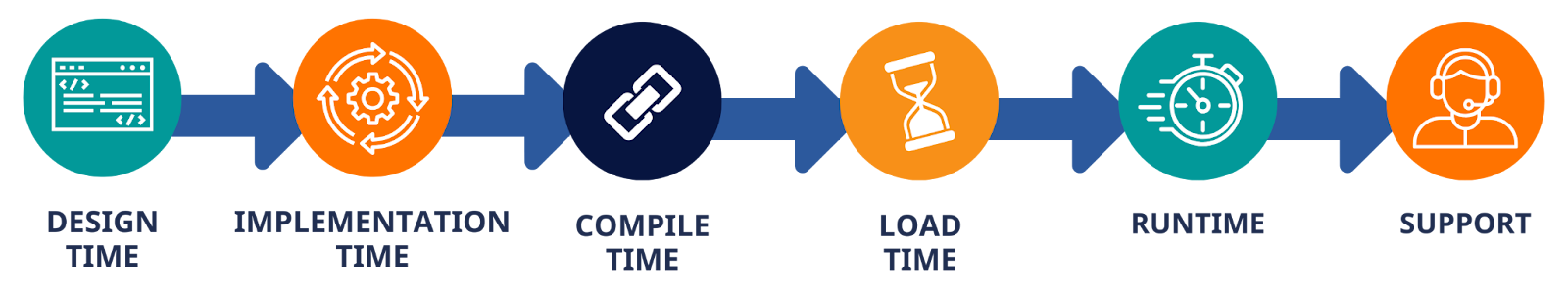
To address these challenges, we need a comprehensive approach that considers the entire lifecycle of embedded systems. Andy proposed a framework organized around “time windows” for security interventions:
- Design time: Making architectural decisions that prioritize security from the start
- Implementation time: Using secure coding practices and memory-safe languages where possible
- Compile time: Leveraging compiler tools and flags that enhance security
- Load time: Implementing protections as programs are loaded into memory
- Runtime: Detecting and preventing exploitation attempts in real-time
- Support time: Analyzing field data to identify and address potential security issues
This multi-layered approach acknowledges that no single intervention is sufficient. By considering security at each phase, organizations can build defense-in-depth strategies that significantly raise the cost and difficulty for attackers.
As Andy put it: “You have a strategy here today that allows you to achieve that vision that you have for 10 years from now. And that’s that’s the seat I’m sitting in right now, and that’s why I’m talking with RunSafe, and why I’m working on it on these other approaches.”
Innovation in Memory Protection
While addressing memory safety in the software supply chain is a challenge, we’re not without options. Several innovative approaches can help address memory safety issues without requiring complete code rewrites:
Memory-safe languages like Rust and Go offer significant security improvements, but adoption in embedded systems remains challenging due to legacy constraints, performance requirements, and the sheer volume of existing C/C++ code.
Hardware-based approaches such as ARM’s Memory Tagging Extension (MTE) and Intel’s Control-flow Enforcement Technology (CET) show promise, but implementation across diverse industrial hardware ecosystems will take time.
Load-time Function Randomization (the technology we’ve developed at RunSafe) moves code around in memory every time a program runs, preventing attackers from reliably exploiting memory vulnerabilities even when they exist in the code.
What’s particularly exciting about these newer approaches is that they change the fundamental economics of cyber warfare. Rather than playing an endless game of vulnerability whack-a-mole, these technologies make exploitation prohibitively difficult and expensive for attackers, even when vulnerabilities exist.
Action Plan for Industrial Organizations
So how should industrial organizations approach this challenge? Based on our work with clients across critical infrastructure sectors, here are key recommendations:
- Conduct a Risk Reduction Analysis to identify your most critical systems and components, focusing particularly on those with memory safety implications. Understand where your key vulnerabilities lie and prioritize protection efforts accordingly.
- Have frank conversations with vendors about their approach to memory safety and supply chain security. Ask specifically how they’re addressing vulnerabilities in third-party components and what runtime protections they provide.
- Implement a defense-in-depth strategy that includes both preventative measures (improved coding practices, memory safety) and runtime protections that can mitigate vulnerabilities even when they exist.
- Make the business case for memory safety investments by focusing on the consequences of compromise. As Andy explained: “You have to understand the likelihood is high, the potential is high. So let’s talk about consequences. And now you have an informed conversation where you can decide how to approach it.”
- Balance security with operational requirements. The best security solutions for industrial environments are those that provide protection without disrupting operations or requiring massive code rewrites.
ICS/OT Security That Gets Ahead of Supply Chain Risk
The security challenges facing industrial control systems and operational technology are significant, but they’re not insurmountable. By addressing memory safety as a root cause rather than just the symptoms, organizations can dramatically improve their security posture against both current and future threats.
As Andy showed, even organizations with massive legacy codebases can make meaningful progress by adopting a strategic, multi-layered approach to security. The key is understanding where your risks lie and implementing protections that work with, rather than against, the realities of industrial environments.
The attackers targeting our critical infrastructure are sophisticated, well-funded, and persistent. But by changing the economics of exploitation through innovations in memory protection, we can ensure that the cost of attacking these systems far exceeds any potential benefit.
That’s a future worth building—one where critical infrastructure is resilient by design, and where attackers seeking to disrupt essential services find themselves facing an insurmountable challenge. Securing embedded systems isn’t just about technology, it’s about protecting the systems that power our world.
The post Securing the ICS/OT Software Supply Chain: What Schneider Electric’s Discovery Means for Industrial Systems appeared first on RunSafe Security.
]]>The post What Is a SBOM? Binary vs Build-Time vs Source Code appeared first on RunSafe Security.
]]>
Software Bills of Materials (SBOMs) are a detailed inventory of all the components—open source, proprietary, and third-party—used within a software application. SBOMs play a key role in ensuring software integrity, managing security risks, and strengthening software supply chain security.
As SBOM requirements expand around the globe, organizations need to be able to generate SBOMs quickly and efficiently to minimize development lifecycle overhead. Depending on the type of software projects you develop and maintain, there are different types of SBOM generation techniques that will work best in different scenarios. Additionally, the way an SBOM is generated affects its accuracy and completeness and your visibility into software vulnerabilities.
Here, we break down the three main types of SBOMs, why SBOMs are important for vulnerability identification and management, and special considerations for C/C++ projects.
Binary-Based SBOMs: The Pre-Packaged View
Binary-based SBOMs are generated by analyzing compiled software, focusing on the final product rather than the source code or build process. The approach works by examining the binary to identify its components and dependencies.
Binary-based SBOMs are useful for legacy software and older systems where source code is either unavailable or inaccessible. They also enable the analysis of third-party software components without requiring access to their source code.
However, relying solely on binary analysis often results in SBOMs that lack critical details that can only be captured during the build process, the most notable example being the existence of statically linked libraries. Some auxiliary data is also lost during compilation, making it difficult to trace the origin and history of certain components due to limited provenance information.
The lack of visibility often leads to a high rate of false positives, as accurately determining the contents of a binary without insight into the actual build is inherently challenging. While valuable in specific scenarios, binary-based SBOMs are less precise compared to other SBOM generation methods.
Key takeaway: Binary-based SBOMs provide a practical solution for managing legacy systems or third-party components. However, they typically lack the depth and accuracy of SBOMs generated from source code or during the build process, often resulting in less detail and a higher likelihood of false positives.
Source Code SBOMs: A Static View with Broad Coverage
Source code-based SBOMs are generated by analyzing a software’s source tree for a specific target, offering a comprehensive view of the components involved in the development process. This method has several notable advantages.
First, it provides complete visibility into the source code, ensuring a thorough inventory of all potential components that could be included in the software. It also offers direct access to valuable metadata, such as licensing and copyright information, which is critical for compliance and legal requirements. Additionally, analyzing source code is less computationally intensive than its more involved build-time SBOM counterpart, as it involves simpler, less resource-demanding operations.
However, the source code-based approach comes with its own set of challenges. A key issue lies in the complexity of build configurations. Since this method examines the source tree rather than the final software build, it may fail to accurately reflect the configurations used to generate the actual binaries. This misalignment can result in discrepancies between the SBOM and the final product. Conditional compilation further complicates matters, as accounting for different compilation paths in large, complex codebases with multiple configurations can be particularly challenging.
Another limitation is its inability to capture runtime dependencies—external components that are dynamically fetched during the software’s operation. Consequently, source code-based SBOMs often over-report, including components that may not make it into the final binary and creating unnecessary noise. This can lead to false positives, where components that are in the source code are flagged even though they will not be in the final build and so do not present any business risk.
Key takeaway: Source code-based SBOMs provide greater visibility into all components of a codebase, making them valuable for compliance, licensing, and early development analysis. However, they still miss out on providing the complete picture of the final product and have a strong chance of false positives by not accounting for build configurations and runtime dependencies.
Build-Time SBOMs: The Complete Picture
Build-time SBOMs are considered the most accurate and efficient method for tracking software components because they are generated during the compilation process, providing a detailed and reliable view of all the components included in the final software build.
Build-time SBOMs execute against the precise components that will be in the build and only contain the relevant libraries and the specific sub-components used in said libraries during the building of the compiled output. Build-time SBOMs are also able to capture all external or linked resources that are only included at build time.
The precision of build-time SBOMs reduces alert fatigue and saves engineering teams time by minimizing false positives and eliminating the need to investigate reported vulnerabilities on components that will not be in the final build and that do not present a risk to production.
When implementing build-time SBOMs, look for solutions that easily integrate into your CI/CD pipeline and existing development workflows. For them to be useful, they must fit smoothly into automated workflows without adding extra complexity or causing delays. Also consider performance. Build-time SBOMs increase accuracy, but should not come at the cost of slowing down build times significantly.
Key takeaway: Build-time SBOMs offer the most precise and comprehensive tracking of software components, making them essential for strengthening software supply chain security and minimizing false positives. They can also be created for legacy software where the source code is readily available. To maximize their impact, choose solutions that seamlessly integrate into your CI/CD pipeline.
Choosing Your SBOM Generation Tool: Implications for Vulnerability Identification
The type of SBOM you choose can significantly impact your software security efforts. When selecting an SBOM generation tool, consider your specific needs, access to source code, and desired accuracy level. For most modern development environments, build-time SBOMs will provide the most value and the clearest picture of your software’s actual composition. A complete and accurate picture of your software’s composition enables more effective vulnerability identification and risk management, allowing you to:
- Maintain strong software supply chain security
- Efficiently identify and address vulnerabilities
- Deliver more secure products
- Meet SBOM regulatory compliance requirements
SBOM Generation for C/C++ Projects
Generating SBOMs for C/C++ projects is challenging because of the complexity and legacy nature of these ecosystems. It is not simple to gather the data and information needed to create comprehensive and accurate SBOMs.
The typical approach is to use package-based component mapping. However, unlike modern languages like Python or Rust, C/C++ doesn’t have a widely adopted package manager, making it difficult to automatically track dependencies.
Without the availability of package managers, each C/C++ SBOM generator has to take an unorthodox approach to SBOM generation, whether it’s by relying on the compiler’s use of files during the build process, the generation of symbols during compilation, or methods yet to be developed. However, each method provides absolute clarity into the build process as it is happening, resulting in high fidelity with no package manager required.
A build-time approach is ideal for real-time and embedded software, giving visibility into your software components with a full dependency tree.
Build-Time SBOMs Lead the Way in Modern Software Security and Compliance
Selecting the right SBOM generation method is vital for ensuring secure and compliant software products. The key to success is choosing an SBOM generation strategy that fits your specific needs, factoring in elements like source code accessibility, development processes, and desired accuracy.
No matter the approach, adopting strong SBOM practices is essential to meet regulatory standards, effectively manage vulnerabilities, and deliver secure, resilient software.
The post What Is a SBOM? Binary vs Build-Time vs Source Code appeared first on RunSafe Security.
]]>The post Building Trust with Software Bill of Materials (SBOMs) appeared first on RunSafe Security.
]]>The Importance of Transparency
SBOMs and Software Supply Chain Security
RunSafe’s Unique Approach to SBOMs
Building Trust with Software Bill of Materials (SBOMs)
The Importance of Transparency
In our digitally connected era, the software supply chain is the backbone of our modern technology. Software development, from its inception to its deployment, navigates a sophisticated network involving developers, vendors, and users. Lately, this supply chain has become a key concern for both security experts and policymakers. Its intricacy introduces numerous security threats that jeopardize the integrity, confidentiality, and availability of software systems.
Transparency within the software supply chain is crucial for identifying and mitigating these risks. High-profile incidents, such as the SolarWinds and Log4j exploits, have illuminated the severe consequences of opaque supply chains, where hidden vulnerabilities can lead to widespread compromise. By fostering transparency, organizations can gain visibility into their software components, dependencies, and the origins of their code. This visibility is essential for understanding the full scope of potential vulnerabilities and for implementing effective security measures.
At RunSafe, we are addressing these challenges by advocating for comprehensive transparency through the use of Software Bill of Materials (SBOMs). SBOMs provide a detailed inventory of software components, enabling organizations to run an accurate vulnerability assessment. Unlike traditional methods that rely on post-production heuristics, RunSafe generates SBOMs during the build process, offering a more complete and accurate representation of the software composition. This proactive approach not only enhances vulnerability management but also ensures compliance with industry standards and regulatory requirements.
SBOMs and Software Supply Chain Security
In the intricate landscape of software supply chain security, the SBOM plays a pivotal role in enhancing transparency and traceability. An SBOM is a detailed inventory that outlines all the components, including dependencies and associated vulnerabilities, within a software application. This comprehensive catalog is essential for organizations to gain deep insights into their software’s composition and the potential security risks it may harbor.
SBOMs are crucial for several reasons. First, they provide a transparent view of all the software components used, enabling organizations to identify and manage vulnerabilities effectively. This transparency is particularly vital in a landscape where third-party software components are prevalent, as it allows organizations to vet and monitor these components rigorously, thereby reducing the attack surface.
Moreover, SBOMs enhance traceability, allowing organizations to track the origins and updates of each software component. This capability is essential for maintaining software integrity. By knowing exactly what is in their software, organizations can swiftly address any vulnerabilities that arise, mitigating the risk of exploitation.
This approach also aids in compliance and regulatory adherence. Many regulatory frameworks and industry standards now mandate detailed documentation and tracking of software components to ensure security and integrity. By generating comprehensive SBOMs, organizations can readily meet these requirements, avoiding potential fines and sanctions. This not only ensures regulatory compliance but also enhances an organization’s reputation for robust security practices.
The detailed insights provided by SBOMs also enable organizations to implement more effective risk management strategies. By understanding the exact composition of their software, organizations can prioritize their security efforts, focusing resources on the most critical and vulnerable components. This targeted approach to risk management improves the overall security efficacy, reducing the likelihood of successful attacks and minimizing potential damage.
RunSafe’s Unique Approach to SBOMs
RunSafe differentiates itself by generating SBOMs directly at build time rather than relying on post-build heuristics. This method provides a complete and accurate representation of the software composition, capturing all dependencies, including second-order ones that conventional methods might miss. This approach ensures a more detailed and reliable SBOM, enhancing an organization’s ability to manage and mitigate security risks proactively.
By incorporating SBOMs into the software development lifecycle, organizations not only enhance their security posture but also demonstrate a commitment to transparency and accountability. This proactive stance not only helps in compliance and regulatory adherence but also builds trust with stakeholders and customers, reinforcing the organization’s dedication to robust cybersecurity practices.
RunSafe’s method of generating SBOMs at build time sets a new standard in software supply chain security. This approach ensures a more detailed and reliable SBOM, empowering organizations to manage and mitigate security risks proactively.
Building Trust with SBOMs
Integrating SBOMs into the software development lifecycle is a critical step in managing and mitigating security risks inherent in today’s complex software supply chains. SBOMs provide an invaluable tool for maintaining transparency and building trust, ensuring software integrity, and bolstering overall security posture. By generating SBOMs at build time, as RunSafe does, organizations can achieve a more detailed and accurate vulnerability assessment of their software composition, capturing all dependencies and reducing the risk of overlooking critical vulnerabilities.
This proactive approach offers several key benefits. It enhances the ability to identify and address vulnerabilities promptly, thus reducing the window of opportunity for malicious actors. It also fosters a culture of accountability and transparency, which is essential for building trust with customers, partners, and regulatory bodies. As regulatory requirements increasingly mandate detailed documentation of software components, having comprehensive SBOMs at hand ensures compliance and minimizes legal and operational risks.
Moreover, the insights provided by SBOMs enable organizations to implement more effective risk management strategies, prioritizing their security efforts on the most critical and vulnerable components. This targeted approach not only improves security efficacy but also optimizes resource allocation, ensuring that security investments yield the maximum possible benefit.
In an era where digital interconnectivity and dependency are at an all-time high, securing the software supply chain is not just an organizational imperative but a fundamental necessity for safeguarding critical infrastructure. By adopting SBOMs and leveraging innovative solutions like those offered by RunSafe, organizations can fortify their defenses, enhance their resilience against emerging threats, build trust, and pave the way for a safer, more secure digital future.
The post Building Trust with Software Bill of Materials (SBOMs) appeared first on RunSafe Security.
]]>The post Understanding and Addressing Third-Party Software Risks appeared first on RunSafe Security.
]]>An Overview of Third-Party Software Risks
RunSafe’s Mitigation Approach to Third-Party Software Security
The Importance of Third-Party Risk Management in Software Supply Chain Security
Understanding and Addressing Third-Party Software Risks
In today’s fast-paced digital landscape, the reliance on third-party software has become an integral part of modern software development. Organizations across industries integrate a myriad of external libraries, frameworks, and tools to expedite their software development cycles and enhance functionality. However, this growing dependence on third-party components introduces significant security challenges. As software supply chains become more intricate, the potential for vulnerabilities within these third-party elements increases, making it imperative for organizations to adopt robust security measures.
At RunSafe, we recognize the critical need to secure the software supply chain against emerging threats. Our innovative approach focuses on mitigating risks associated with third-party software without compromising performance or necessitating extensive code modifications. By embedding security features during the build process, we address memory-based vulnerabilities and other potential threats at their source, ensuring that the software remains resilient and secure throughout its lifecycle.
In this blog post, we’ll examine the complexities of third-party risk management, highlighting the associated risks and exploring effective strategies for enhancing supply chain security. As organizations navigate this evolving landscape, it becomes clear that proactive measures and cutting-edge solutions are essential for safeguarding digital ecosystems against the ever-present threat of cyberattacks.
An Overview of Third-Party Software Risks
Third-party software components are indispensable for accelerating development cycles and enriching software functionality. However, they also introduce significant vulnerabilities that can be exploited by malicious actors. As software systems increasingly rely on these components, the attack surface expands, posing challenges for maintaining security.
One of the primary vulnerabilities associated with third-party components is the lack of visibility and control over their security posture. Organizations often integrate these components without thoroughly vetting their origins, development practices, or update schedules. This can lead to the inclusion of outdated or insecure code, which may contain known vulnerabilities that can be easily exploited.
Moreover, third-party components can be a conduit for indirect attacks. Malicious actors can infiltrate less secure third-party systems to insert backdoors or malware, which then propagate into the primary system. This was notably demonstrated in the SolarWinds attack, where attackers compromised a widely-used third-party platform to gain unauthorized access to numerous high-profile targets.
Open-source software (OSS) poses additional risks despite its widespread use and collaborative benefits. The decentralized nature of OSS development can result in inconsistent security practices and delayed vulnerability management. Without rigorous scrutiny and timely updates, organizations risk integrating compromised OSS components that can jeopardize overall system integrity.
RunSafe’s Mitigation Approach to Third-Party Software Security
RunSafe addresses these risks beginning with a thorough vetting process during the build phase. By integrating seamlessly with existing build tools, such as Yocto and Buildroot Linux, RunSafe inspects and secures both proprietary and open-source software components. This integration allows our technology to apply its proprietary immunization techniques, which safeguard against memory-based vulnerabilities without altering source code or impacting performance.
By focusing on build-time integration, we ensure that all software components, including those sourced from third parties, are scrutinized for potential security risks. This proactive measure helps to identify and mitigate vulnerabilities before they can be exploited in a live environment.
RunSafe’s solution extends beyond initial vetting, offering continuous monitoring of third-party components throughout the software lifecycle. This ongoing vigilance is crucial, given the dynamic nature of software vulnerabilities and the evolving tactics of cyber threats. RunSafe plans to enhance third-party risk management by integrating risk indicators directly into the build process, allowing organizations to assess the security posture of third-party software in real-time.
Additionally, RunSafe’s capability to generate Software Bill of Materials (SBOMs) at build time provides organizations with a comprehensive inventory of all software components. Unlike traditional methods that rely on heuristic analysis of software binaries, RunSafe’s approach offers a detailed and accurate representation of the software composition, including second-order dependencies. This transparency is vital for identifying and addressing vulnerabilities promptly.
RunSafe’s robust approach to securing third-party software also supports regulatory compliance and industry standards. By ensuring that all components meet stringent security criteria and providing detailed SBOMs, RunSafe helps organizations demonstrate their commitment to maintaining robust software supply chain security. This not only mitigates risk but also enhances trust and accountability with customers and stakeholders.
The Importance of Third-Party Risk Management in Software Supply Chain Security
Risk management is essential in securing the software supply chain, a complex ecosystem that spans from development to deployment. As software development increasingly relies on diverse third-party components and open-source libraries, each integration point becomes a potential vulnerability. Effective risk management involves proactively identifying, assessing, and mitigating these risks to protect the integrity, confidentiality, and availability of software systems.
The consequences of supply chain breaches are profound, affecting everything from critical infrastructure to consumer trust. High-profile attacks, such as the SolarWinds breach and the Log4j vulnerability, underscore the urgency of securing every link in the software supply chain. These incidents demonstrate how vulnerabilities can be exploited to compromise sensitive data and disrupt operations on a massive scale.
RunSafe provides a robust solution to address the growing threats within the software supply chain. By embedding protective measures during the build process, RunSafe mitigates memory-based vulnerabilities without requiring significant code changes or impacting performance. This approach not only secures the software but also maintains operational efficiency, offering a practical alternative to traditional security measures.
In our current interconnected digital landscape, organizations must prioritize risk management to fortify their software supply chains. By leveraging comprehensive risk assessment frameworks and proactive mitigation strategies, companies can safeguard their operations, comply with regulatory requirements, and ensure the resilience of critical infrastructure.
The post Understanding and Addressing Third-Party Software Risks appeared first on RunSafe Security.
]]>The post Visualizing SBOMs for Embedded Systems: Key Components, Examples, and Takeaways for Cybersecurity appeared first on RunSafe Security.
]]>Understanding and managing software components is crucial for safeguarding against cybersecurity vulnerabilities. A Software Bill of Materials (SBOM) serves as a comprehensive inventory of all components, libraries, and modules used in software applications. SBOMs help organizations identify and address potential security risks efficiently and transparently.
SBOMs are particularly significant in embedded systems, which are integral to numerous critical applications, from medical devices to industrial control systems. Because embedded systems often incorporate a variety of third-party and open-source components, they are susceptible to hidden vulnerabilities. SBOMs give visibility into these components, allowing developers and software manufacturers to get ahead of risk.
What Is a SBOM?
A Software Bill of Materials is a detailed list of all components, libraries, and modules used in a software application. Think of it as an ingredient list for a recipe, but for software. Each entry in an SBOM provides crucial information about the components, including their origin, version, and any known vulnerabilities. This comprehensive inventory is essential for managing software supply chains and ensuring robust security. SBOMs play a pivotal role in providing transparency and accountability for risk assessment in software development.
Why SBOMs Matter in Embedded Systems
Embedded systems are specialized computing systems that perform dedicated functions within larger mechanical or electrical systems. Found in devices ranging from medical equipment and industrial controls to consumer electronics and automotive systems, embedded systems are integral to critical infrastructure. These systems are designed for specific tasks, often operating in real-time and requiring high reliability and stability.
Given their crucial roles in sectors such as healthcare, energy, transportation, and manufacturing, embedded systems are often targets for cyber threats. Their integration into critical infrastructure means that any vulnerability can have far-reaching and potentially catastrophic consequences.
SBOM Example: Key Components for Embedded Systems
For embedded systems, having a comprehensive and accurate SBOM is essential. Below are the key components:
- Component name: Each software component is listed by its name. This includes libraries, frameworks, and modules. Example: libssl.so.1.1.
- Version information: The specific version of each component is noted. Example: Version 1.1.1g.
- Supplier Information: Details about the vendor or author of the component. Example: OpenSSL Software Foundation.
- Licensing information: The type of license governing the use of the component. This ensures compliance with legal and regulatory requirements. Example: Apache License 2.0.
- Component hash: A cryptographic hash (e.g., SHA-256) that verifies the integrity of the component. Example: 3c1a84ab7f23cd8c1e8f4564a2e4f45b234a7d8e92b6ec34b8b9d5c6e8f01234.
- Dependency relationships: Information on how components depend on each other. Example: libssl.so.1.1 -> libcrypto.so.1.1.
- Security and vulnerability information: Known vulnerabilities associated with the components. Example: CVE-2020-1971.
An SBOM for an embedded system might include a line like the following example:
File Component Example from a Build-Time SBOM
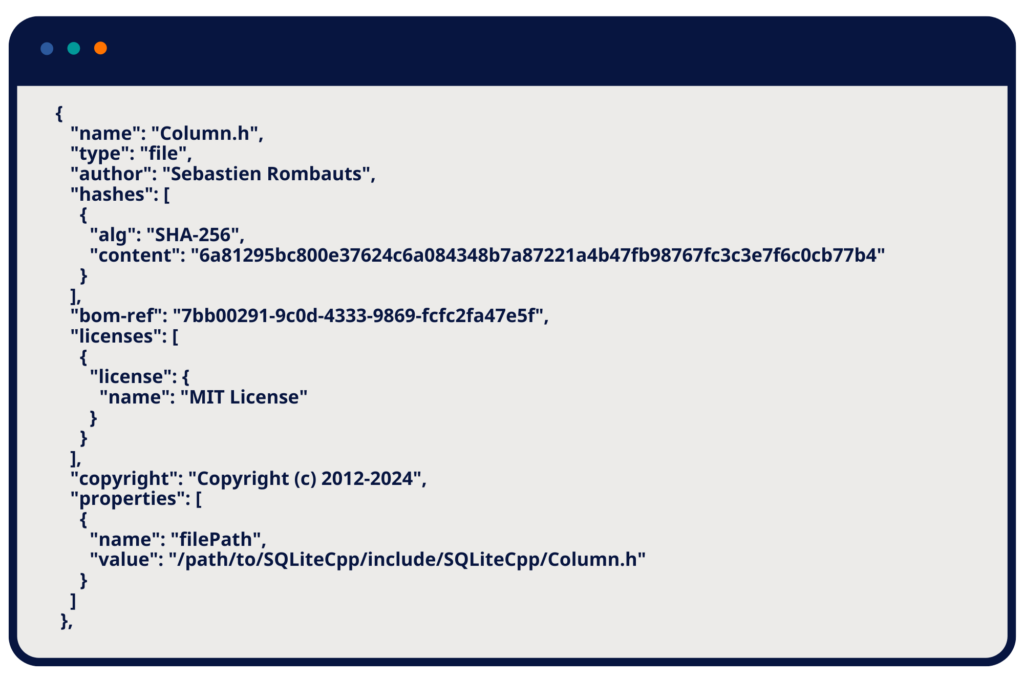
Library Component Example from a Build-Time SBOM
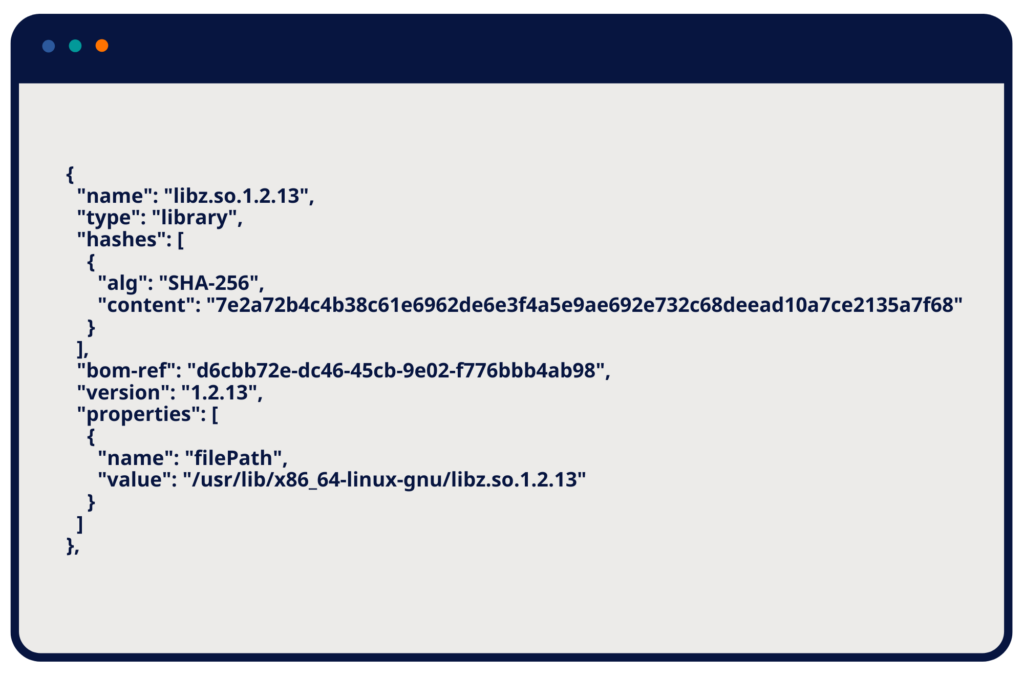
GET FULL VISIBILITY INTO THE COMPONENTS IN YOUR EMBEDDED SYSTEMS [START FREE TRIAL]
Creating an SBOM: Top Security Tools and Best Practices
Common tools for generating SBOMs in embedded systems include:
- Syft: A CLI tool for creating SBOMs from container images and filesystems.
- CycloneDX: A lightweight SBOM standard.
- SPDX: An open standard with tools like SPDX-Tools for SBOM creation and validation.
- Black Duck: A comprehensive open-source management tool with SBOM generation features.
- FOSSA: An automated tool for open-source compliance, security, and SBOM generation.
- Endor Labs: Goes beyond traditional SCA tools by not relying solely on package manifests, addressing transitive dependencies effectively.
- RunSafe Security: Generates SBOMs as part of the build process with unique capabilities for C/C++ languages
Best practices for creating effective and comprehensive SBOMs include the following:
- Integrate automated tools into the CI/CD pipeline for consistent SBOM updates.
- List all software components, including dependencies, versions, licenses, and suppliers.
- Regularly update SBOMs to reflect new components and patches.
- Use cryptographic hashes to verify component integrity.
- Include known vulnerabilities (e.g., CVEs) for proactive security management.
- Ensure license compliance for all components.
- Maintain clear documentation and transparency throughout the supply chain.
Using SBOMs to Enhance Embedded Systems Security
Using SBOMs is a proactive strategy for bolstering the security of embedded systems. SBOMs provide a detailed inventory of all software components, including versions and dependencies. This transparency allows security teams to track known vulnerabilities (e.g., CVEs) associated with each component.
By regularly updating SBOMs and cross-referencing them with vulnerability databases, organizations can quickly identify and address security weaknesses. Automated tools can alert teams to newly discovered vulnerabilities, facilitating prompt patching and mitigation efforts.
By analyzing the SBOM, organizations can prioritize security efforts based on the potential impact of each vulnerability.
Challenges and Solutions in SBOM Implementation
Integrating SBOMs into embedded systems faces challenges like managing numerous third-party components, limited processing power, and memory constraints. Tracking component versions and ensuring consistency across environments is difficult, and the lack of industry-wide standards can cause compatibility issues.
Practical solutions include using automated SBOM tools like SPDX and CycloneDX, incorporating SBOM generation into CI/CD workflows, adopting standardized SBOM formats, conducting regular audits, and training development teams on best practices for SBOM creation and maintenance. These strategies help streamline dependency tracking, maintain accuracy, and ensure compatibility in managing software component inventories.
The Future of SBOMs in Embedded Systems
The future of SBOMs in embedded systems is set to transform significantly, spurred by emerging trends, government directives, and technological advancements aiming to bolster security and operational efficiency.
Recent federal directives have underscored the importance of SBOMs in ensuring software security, aligning with NIST Guidance and emphasizing secure software development practices. Automation tools and AI are poised to play an increasingly vital role in SBOM generation, streamlining vulnerability identification and risk prediction.
Future SBOMs are likely to integrate real-time monitoring, machine learning, and big data analytics to enhance integrity and authenticity. Standardization efforts and regulatory recognition are expected to drive broader adoption and interoperability, integrating SBOMs into DevSecOps practices and facilitating early vulnerability detection.
How SBOMs Improve Software Security
SBOMs are essential for securing embedded systems, providing transparency, vulnerability tracking, and risk assessment. As embedded systems play critical roles in various industries, the adoption of SBOM practices becomes paramount for maintaining robust security postures. By integrating SBOMs into your cybersecurity strategy, you can proactively address potential threats and enhance the resilience of your systems.
The post Visualizing SBOMs for Embedded Systems: Key Components, Examples, and Takeaways for Cybersecurity appeared first on RunSafe Security.
]]>The post Ensuring Critical Embedded Systems Security: Overcoming Challenges in OT and ICS appeared first on RunSafe Security.
]]>Challenges and Solutions for OT and ICS to Secure Software Development
Challenges in Securing Critical Embedded Systems and Industrial Control Systems
The Importance of Secure by Design Principles
Strategies for Securing Critical Embedded Systems
Future Trends and Emerging Technologies Protecting CES
Tips to Implement Secure Software Development Measures
Ensuring Critical Embedded Systems Security: Overcoming Challenges in OT and ICS
Challenges and Solutions for OT and ICS to Secure Software Development
In today’s digital landscape, securing critical embedded systems (CES) and industrial control systems (ICS) is imperative, especially for organizations whose technology, if compromised, could have severe consequences. CES, like medical devices and nuclear infrastructure, demand 100% uptime and robust security due to their essential nature. ICS, a subset of CES, regulates industrial processes from manufacturing to power generation.
These systems face unique vulnerabilities, including legacy software and limited resources, making them targets for cyberattacks. Memory-based attacks pose significant threats, potentially causing system failures with catastrophic results.
Secure software development requires a proactive approach that addresses vulnerabilities at the root level. Traditional cybersecurity measures often fall short in this regard, necessitating innovative solutions tailored to the unique requirements of critical embedded systems and ICS.
RunSafe Security offers critical embedded systems security that enhances traditional software security without compromising system performance. Through code hardening and memory protection, RunSafe defends against known and unknown vulnerabilities, safeguarding critical infrastructure and providing robust software supply chain security.
Challenges in Securing Critical Embedded Systems and Industrial Control Systems
Ensuring the security of all technology is crucial, but CES and ICS face unique challenges. These systems embed software in physical devices, making updates complex and difficult due to the need for uninterrupted performance. Moreover, CES and ICS are deployed across diverse hardware platforms, requiring tailored security approaches.
CES confronts challenges in updating and patching vulnerabilities, often operating in environments where frequent updates are impractical. Performance constraints further limit traditional security measures. The diverse hardware architectures and operating systems add complexity to security efforts, demanding adaptable solutions.
Security breaches in CES and ICS can have dire consequences, affecting various sectors from medical devices to power plants. Breaches could result in data manipulation, operational disruptions, equipment damage, or threats to human safety. The interconnected nature of modern infrastructure amplifies the impact of vulnerabilities, affecting entire supply chains and critical services. Securing these systems demands a comprehensive approach tailored to their unique requirements, emphasizing innovation and adaptability.
The Importance of Secure by Design Principles
In the realm of software supply chain security, the Secure by Design paradigm ensures that the entire organization is aligned in building software that is impeccably planned, designed, tested, and maintained.
This approach entails proactive threat modeling, multi-layered defense mechanisms, vulnerability scanning, and various other strategies to prioritize security and mitigate threats. When developing software for CES or ICS, organizations must integrate security as a critical priority from the outset. This involves implementing best practices to establish safeguards against potential threats, conducting multiple rounds of security-focused testing during the quality assurance phase, and regularly performing threat modeling and vulnerability exercises on released products.
For developers, utilizing a Software Bill of Materials (SBOM) is a valuable practice. An SBOM generates a comprehensive list of all software components and their versions, aiding in the identification of dependencies that may introduce security vulnerabilities.
RunSafe offers an efficient solution by generating an SBOM and identifying any components that may increase the attack surface of a project. Integrating RunSafe into a developer’s workflow streamlines the process, facilitating proactive security measures and ensuring the resilience of critical systems against cyber threats.
Strategies for Securing Critical Embedded Systems
Critical embedded systems security demands a multifaceted approach to address unique challenges. While human error is inevitable, strategies like automated code hardening and memory corruption prevention mitigate risks. RunSafe’s solution offers memory protection and serves as a Moving Target Defense (MTD), adjusting code structure at runtime to thwart hackers.
Automated code hardening injects unique binary diversification into software builds, protecting against memory-based attacks without system performance impact. Memory corruption prevention disrupts exploitation techniques at runtime, neutralizing threats without impairing functionality.
Supporting diverse platforms streamlines maintenance and updates, while staying updated on evolving threats is crucial. RunSafe’s solutions, compatible with various platforms including LynxOS, VxWorks, and Linux, fortify CES against known and unknown vulnerabilities.
By integrating these strategies and RunSafe’s technologies, organizations enhance CES security, safeguarding critical systems against cyber threats and ensuring uninterrupted operations.
Future Trends and Emerging Technologies Protecting CES
In the realm of cybersecurity, upcoming trends and emerging technologies are poised to revolutionize the protection of CES. One significant trend is the integration of artificial intelligence (AI) into security solutions, enabling real-time threat detection and response through advanced data analysis.
Moreover, the proliferation of Internet of Things (IoT) devices in critical infrastructure introduces both challenges and opportunities. While expanding the attack surface, IoT integration also presents avenues for innovative security measures, including device-level encryption and authentication protocols.
Tips to Implement Secure Software Development Measures
For organizations aiming to bolster their software supply chain security, implementing secure software development measures is paramount. Below are some practical recommendations:
- Adopt a Secure by Design approach: Integrate security considerations into every stage of the software development lifecycle, prioritizing security from design to deployment.
- Implement automated code hardening: Leverage tools like RunSafe’s automated code hardening solution to fortify software against memory-based attacks without compromising performance.
- Conduct regular vulnerability assessments: Perform comprehensive vulnerability scans and audits to identify and address potential weaknesses in CES and ICS environments.
- Ensure diverse platform support: Support a variety of hardware platforms and operating systems to facilitate easier maintenance and updates across environments.
- Stay informed about emerging threats: Keep abreast of evolving cybersecurity threats and trends, and continuously update security measures to adapt to changing landscapes.
- Integrate RunSafe Protect: Utilize RunSafe Protect to streamline software security processes, automate cybersecurity measures, and seamlessly integrate security into developers’ workflows.
By implementing these practical recommendations, organizations can significantly improve the security posture of their critical systems, safeguarding mission-critical infrastructure against cyber threats.
The post Ensuring Critical Embedded Systems Security: Overcoming Challenges in OT and ICS appeared first on RunSafe Security.
]]>The post Mitigating the Software Supply Chain Risks with RunSafe appeared first on RunSafe Security.
]]>Enhancing The Security Posture in Modern Software Development with RunSafe
Understanding Software Supply Chain Security in the Digital Era
How RunSafe’s Solution Addresses Protects Against Memory Safety Vulnerabilities
How RunSafe Prioritizes Supply Chain Security
Mitigating the Software Supply Chain Risks with RunSafe
Enhancing The Security Posture in Modern Software Development with RunSafe
In the dynamic landscape of today’s interconnected digital world, where software serves as the backbone of modern technology, the security of the software supply chain stands out as a paramount concern.
The journey of software development, from its conceptualization to its deployment, navigates an intricate network comprising developers, vendors, and end-users. This complexity presents an array of security risks that can jeopardize the integrity, confidentiality, and availability of software systems.
While the risks facing the software supply chain are significant, organizations can take proactive steps to mitigate these threats and enhance their security posture. One of the key challenges is the complexity of modern software development, which involves numerous stakeholders and dependencies. Traditional security measures often fall short in addressing the unique challenges posed by the software supply chain.
Innovative solutions like RunSafe offer a pragmatic and economically feasible approach to mitigating supply chain risks.
Understanding Software Supply Chain Security in the Digital Era
In recent years, the software supply chain has emerged as a critical focal point for security professionals and policymakers alike. With cyber threats becoming increasingly sophisticated and pervasive, organizations face the daunting challenge of securing their software supply chains against a myriad of vulnerabilities and risks.
From third-party vulnerabilities to the challenges of maintaining software integrity and compliance, the threats facing the software supply chain are diverse and ever-evolving.
Before delving into specific solutions, it’s crucial to understand the risks inherent in the software supply chain ecosystem. At each stage of the software supply chain lifecycle, adversaries can exploit potential vulnerabilities to infiltrate systems, compromise data, or disrupt operations.
Some of the major security risks facing the software supply chain include:
Third-Party Software Vulnerabilities: Third-party software components serve as potential entry points for malicious actors seeking to exploit vulnerabilities. Securing an ever-expanding attack surface without robust mechanisms for vetting and monitoring third-party components poses a significant challenge to organizations.
Open-Source Software Risks: While open-source software (OSS) offers unparalleled flexibility and scalability, the decentralized nature of OSS communities poses inherent risks in terms of vulnerability management and code integrity. Organizations integrating OSS into their projects must navigate the complexities of patch management, license compliance, and code hygiene to mitigate the risk of exploitation.
Software Integrity and Compliance: Ensuring the integrity and compliance of software throughout its lifecycle is a multifaceted endeavor. From securing the build environment to validating software authenticity and enforcing regulatory requirements, organizations grapple with a myriad of challenges in maintaining trustworthiness and accountability.
How RunSafe’s Solution Addresses Protects Against Memory Safety Vulnerabilities
RunSafe Security, a leader in software supply chain security, offers a transformative solution to address the escalating threats within the software supply chain. By seamlessly embedding protective measures into the software during the build process, RunSafe effectively addresses memory safety vulnerabilities while preserving system performance.
Automated Protection: RunSafe’s integration with Continuous Integration (CI) tools facilitates the seamless incorporation of security measures into the build process. By enforcing security at build time for runtime protection in deployed software, organizations can fortify their software against potential threats without impeding development workflows.
Diverse Platform Support: RunSafe supports various compilers across different operating systems, including real-time operating systems like VxWorks and LynxOS, as well as embedded Linux and Android. This extensive platform support enables organizations to bolster the security of their software supply chain across diverse environments.
Streamlined Integration Process: Our solution easily integrates into existing build workflows with minimal time and effort required for implementation. Whether organizations manually conduct builds or use automated tools such as Yocto or Buildroot Linux, RunSafe seamlessly integrates into various build toolchains.
How RunSafe Prioritizes Supply Chain Security
By seamlessly embedding protective measures into the software during the build process, RunSafe addresses memory safety vulnerabilities without compromising system performance. This approach not only enhances the security of software applications but also streamlines the development process, enabling organizations to focus on innovation and customer satisfaction.
Furthermore, RunSafe’s support for diverse platforms and build toolchains ensures compatibility with existing workflows, minimizing disruption and facilitating seamless integration. By empowering organizations to fortify their software supply chains against potential threats, RunSafe plays a pivotal role in enhancing the resilience of digital ecosystems and safeguarding critical infrastructure.
Securing the software supply chain is not just a matter of organizational resilience; it is a fundamental imperative for safeguarding critical infrastructure and ensuring the integrity of digital ecosystems. By adopting proactive measures and leveraging innovative solutions like RunSafe, organizations can mitigate the risks posed by supply chain vulnerabilities and pave the way for a safer, more resilient digital future.
The post Mitigating the Software Supply Chain Risks with RunSafe appeared first on RunSafe Security.
]]>The post The Memory Safety Crisis: Understanding the Risks in Embedded Software appeared first on RunSafe Security.
]]>Risks of Memory Vulnerabilities in Embedded Software
Challenges of Addressing Memory Safety
RunSafe’s Innovative Approach to Memory Safety
Software Supply Chain Security with RunSafe
Ensuring Security in Embedded Systems, ICS, and OT
Practical and Cost-Effective Memory-Based
Vulnerability Protection
The Memory Safety Crisis: Understanding the Risks in Embedded Software
Introduction to Memory Safety
Memory safety is a foundational aspect of software development, ensuring that programs operate reliably and securely without accessing or manipulating memory incorrectly. In embedded systems, where software controls critical functions such as transportation systems or power grids, the importance of memory safety cannot be overstated.
The National Security Agency (NSA) has issued guidance emphasizing the severity of such vulnerabilities, prompting major tech companies like Google and Microsoft to underscore their prevalence. Likewise, the Cybersecurity and Infrastructure Security Agency (CISA) has issued an implementation plan to fortify and defend the digital landscape.
This blog post delves into the risks posed by memory vulnerabilities in embedded software, the challenges in addressing them, and how embedded software security solutions like RunSafe Security can enhance memory safety without extensive code rewrites or performance degradation.
Risks of Memory-Based Vulnerabilities in Embedded Software
Memory safety in embedded software is not just a concern, it’s a substantial and pressing threat to software deployed within critical infrastructure. This concern is further amplified by the NSA’s recent guidance in November 2022, which underlines the gravity of the risk posed by memory-based vulnerabilities. These vulnerabilities have the potential to compromise the integrity and security of essential systems, a risk that cannot be ignored.
A similar analysis from MITRE reveals a sobering reality: three of the top eight most dangerous software weaknesses are memory safety issues. Google and Microsoft echo these concerns, reporting that nearly 70% of their vulnerabilities in native code stem from memory-based flaws.
The NSA’s recommendation, a fast transition to memory-safe alternatives like Go, Java, Ruby, Rust, and Swift, highlights the situation’s urgency. However, the monumental task of rewriting code for memory safety means touching billions of lines of code across countless code bases and products. This presents significant challenges to any organization, both in terms of financial investment and opportunity cost.
Challenges of Addressing Memory Safety
Traditionally, the recommended approach to addressing memory safety in embedded software has been rewriting code in languages like Rust, which is known for its memory safety features. However, rewriting billions of lines of code across numerous code bases and products entails significant costs and time investments. Moreover, this may disrupt existing workflows and introduce unnecessary complexities into development processes.
RunSafe’s Innovative Approach to Memory Safety
RunSafe Security presents a pioneering solution in contrast to conventional methods, providing organizations with the capability to attain memory safety without requiring extensive code alterations or sacrificing performance. Utilizing its cutting-edge technology, RunSafe employs a method of hardening code by randomizing the placement of functions in memory, ensuring a unique memory layout for each binary during runtime.
By embedding protective measures directly into the software during the build process, RunSafe effectively addresses memory-based vulnerabilities while maintaining system performance. This approach offers a practical and economically viable alternative to traditional security measures, mitigating the risk of exploitation without imposing significant overhead on operations.
Moreover, RunSafe seamlessly integrates with continuous integration and continuous delivery (CI/CD) pipelines, streamlining the incorporation of enhanced security measures into the software supply chain. This integration ensures that developers can maintain their productivity while simultaneously fortifying the security of their applications, significantly improving the resilience of deployed software against potential threats.
Software Supply Chain Security with RunSafe
By implementing RunSafe technology within CI/CD pipelines, organizations gain the capability to reinforce proprietary software compiled internally or by suppliers, alongside deploying hardened iterations of incorporated open-source components. Leveraging RunSafe’s CI integrations with GitLab and GitHub, customers can automate SBOM generation, and integrate security measures at build time—all without compromising developer efficiency or system performance.
Ensuring Security in Embedded Systems, ICS, and OT
Securing operational technology (OT), industrial control systems (ICS), and other critical embedded systems poses distinctive challenges. Yet, RunSafe’s technology adeptly tackles these obstacles by thwarting memory-based attacks, and safeguarding embedded software during runtime without imposing undue administrative burdens.
Through our automated tool, protective measures are integrated at the software build stage, and activated during deployment to fortify embedded software during runtime. Our extensive deployment experience spans across a myriad of devices, ranging from firmware on servers to interoperability software facilitating communication between electric vehicle charging stations and the energy grid, as well as software employed in industrial automation facilities.
In addition to this, RunSafe’s technology can be integrated into DevSecOps workflows, ensuring that security measures are applied consistently throughout the development process and across development teams. By incorporating protections at the build stage, organizations can mitigate vulnerabilities early in the software development lifecycle, reducing the risk of exploitation in production environments.
RunSafe’s compatibility is not limited by operating system or instruction set. RunSafe products are compatible across various operating systems (such as LynxOS, VxWorks, Linux, Android, QNX and several other iterations) and most instruction sets (Intel, ARM (32 and 64), Power PC, and additional instruction sets). This versatility ensures that organizations across diverse sectors can confidently leverage RunSafe’s technology to enhance the security posture of their embedded systems, knowing that it can adapt to their specific needs.
Practical and Cost-Effective Memory-Based Vulnerability Protection
The imperative to address memory safety in embedded software is a critical issue that demands immediate attention. RunSafe Security offers a practical and cost-effective solution to this problem, allowing organizations to strengthen their software against memory-based vulnerabilities without the need for extensive code rewrites or performance sacrifices.
As the threat landscape evolves, embracing innovative approaches like RunSafe Security becomes essential for safeguarding critical infrastructure and ensuring the resilience of embedded systems.
Take charge of your organization’s memory safety today in your software deployments and mitigate the risks posed by memory-based vulnerabilities with RunSafe Security.
The post The Memory Safety Crisis: Understanding the Risks in Embedded Software appeared first on RunSafe Security.
]]>The post Securing Critical Infrastructure: The Role of SBOMs appeared first on RunSafe Security.
]]>Securing Critical Infrastructure: The Role of SBOMs
Cybersecurity in Critical Infrastructure: An Overview
Introduction to Software Bill of Materials (SBOMs)
How SBOMs Contribute to Cybersecurity
Types of SBOMs and How They Are Different
Benefits of Build-time and Binary SBOMs
Use Cases for Critical Infrastructure
Taking SBOMs to the Next Level
Securing Critical Infrastructure: The Role of SBOMs
The protection of critical infrastructure is paramount. From power grids to transportation systems, the backbone of society relies heavily on interconnected software systems. However, with this increased reliance on technology comes a heightened risk of cyber threats that continue to increase in frequency and sophistication.
In this blog, we’ll explore the significance of Software Bill of Materials (SBOMs) in fortifying the cybersecurity of our critical infrastructure.
Cybersecurity in Critical Infrastructure: An Overview
Critical infrastructure encompasses various sectors essential to society’s normal functioning, including energy, water, transportation, and communication. As these systems become increasingly digitized, they also become susceptible to cyberattacks. Threat actors, ranging from nation-states to malicious hackers, target vulnerabilities in software systems to disrupt operations, compromise data, and cause widespread chaos.
Introduction to Software Bill of Materials (SBOMs)
A Software Bill of Materials (SBOM) is a comprehensive list of components and dependencies within a software system. Think of it as a detailed inventory that outlines all the ingredients used to build a particular software product, including libraries, frameworks, and third-party modules. SBOMs provide invaluable transparency into the software supply chain, offering insights into the origin and composition of every component.
How SBOMs Contribute to Cybersecurity
The significance of SBOMs in cybersecurity cannot be overstated. These documents serve multiple critical functions:
Enhancing Supply Chain Security: With the growing efficiency of software development outsourcing and third-party integrations, the software supply chain has become increasingly complex. SBOMs enable stakeholders to track every component’s origin and assess its security posture, mitigating the risk of supply chain attacks.
Facilitating Vulnerability Management: By providing a detailed inventory of software components, SBOMs streamline vulnerability management processes. Organizations can quickly identify and address vulnerabilities within their software stack, reducing the window of exposure to potential cyber threats.
Supporting Vulnerability Disclosure and Reporting: Effective communication with customers and stakeholders is essential in cybersecurity. SBOMs facilitate transparent vulnerability disclosure by providing recipients with a clear understanding of the software’s composition and any associated security risks.
Types of SBOMs and How They Are Different
According to the Cybersecurity & Infrastructure Security Agency (CISA), there are multiple types of SBOMs: Design, Source, Build, Analyzed, and Deployed. While each serves a specific and valuable purpose, two types impact the effectiveness of cybersecurity for critical infrastructure: build, Deployed, and Runtime (also called Binary).
Build-time SBOMs are generated during the software build process and offer insight into the components used in the software. Used mostly by product manufacturers and developers, Build SBOMs gather data from source files, dependencies, built components, build process ephemeral data, and other SBOMs to create a releasable artifact.
Binary-based SBOMs provide an inventory of software that is present in a running environment and/or has been executed. It offers infrastructure operators insights into components present in the system and external call-outs or dynamically loaded components.
Benefits of Build-time and Binary SBOMs
Integrating Buildtime and Runtime SBOMs into cybersecurity strategies helps to strengthen the resilience of critical infrastructure systems against cyber threats and ensure the uninterrupted operation of essential services.
While they don’t create security themselves, SBOMs provide the insight needed to secure embedded software, systems, and connected devices by identifying the areas of opportunity to improve security.
Both Build-time and Binary SBOMs offer unique benefits to stakeholders:
Build-time SBOMs: Product Manufacturers
- Improved accuracy of SBOM details because it uses information from the build and/or Continuous Integration/Continuous Deployment (CI/CD) processes.
- Improved risk assessment and mitigation strategies.
- Greater visibility into more components than just source code.
- Compliance with regulatory requirements such as NIST SP 800-161.
Binary SBOMs: Operators of Infrastructure
- Visibility into what’s currently in use when the system is running.
- Details about what components and parts are active or not in use.
- Streamlined vulnerability management processes.
- Compliance with regulatory mandates.
Use Cases for Critical Infrastructure
As part of its Secure by Design initiative, CISA advises the use of SBOMs for software supply chain security:
Publish Software Bills of Materials (SBOMs). Manufacturers should have command of their supply chains. Organizations should build and maintain SBOMs for each product, request data from their suppliers, and make SBOMs available for downstream customers and users. This will help demonstrate their diligence in understanding the components they use in creating their products, their ability to respond to newly identified risks, and can help customers understand how to respond if one of the modules in the supply chain has a newly found vulnerability.
Here are some use cases that demonstrate how SBOMs can be used to help protect different sectors of critical infrastructure:
Water and Utilities: SBOMs play a crucial role in enabling the security and resilience of water and utilities infrastructure. Because water utilities rely on interconnected IT and OT systems, often have legacy infrastructure, are part of an interconnected supply chain, and tend to employ limited cybersecurity resources, they are attractive targets for cyber adversaries.
SBOMs can mitigate some of these risks as part of an overall cybersecurity strategy by identifying and mitigating vulnerabilities in control systems and IoT devices. They can also recognize vulnerabilities across the software supply chain so the water or utility company can proactively protect itself against attack.
IOT/Embedded Systems: The Internet of Things (IOT) and embedded systems enable increased efficiency, productivity, and accuracy in operations. However, limited security measures, rapid increase in devices, insecure communication protocols, weak authentication, and lack of regular updates put IoT devices and embedded systems at higher risk of cyber attacks.
To mitigate these risks, organizations and manufacturers must prioritize cybersecurity throughout the entire lifecycle of IoT and embedded devices, including design, development, deployment, and maintenance. Leveraging SBOMs at each lifecycle stage provides deep visibility of potential vulnerabilities.
Weapons Systems: In the defense sector, weapons systems are interconnected global networks dependent on information technology to provide real-time information, communication, and reaction. The integration of commercial off-the-shelf (COTS) components, lack of secure-by-design practices, and the convergence of cyber and physical threats elevate weapons systems to top targets for nation-state threats.
Employing a strong cybersecurity strategy throughout the entire lifecycle of weapon systems enhances protections against cyber warfare. SBOMs shared among private and public entities across the software supply chain for weapons systems ensure awareness of all potential vulnerabilities and enable proactive actions to increase safety and defenses.
Taking SBOMs to the Next Level
Cyber threat actors are learning as quickly as cybersecurity professionals and are creating more sophisticated vulnerability threats faster and in greater volumes. This evolution requires cybersecurity defenses to evolve exponentially faster.
One way to do this is to integrate cybersecurity practices directly into existing DevOps pipelines to minimize performance impact and ensure complete visibility of components and parts at build time. Utilizing automated tools to extract component information during the build process streamlines the compilation of build-time SBOMs while still gathering vital build-time data.
Conclusion
SBOMs are indispensable tools for safeguarding critical infrastructure against cyber threats. While they may not create security themselves, they offer invaluable insights that arm critical infrastructure organizations with the information necessary to strengthen their cybersecurity posture.
By integrating SBOMs into security frameworks, product manufacturers, developers, and infrastructure operators can enhance visibility, streamline vulnerability management, and mitigate risks effectively.
As cyber threats continue to intensify and cross over to physical vulnerabilities, adopting SBOMs will be a crucial, proactive step in securing our critical infrastructure.
The post Securing Critical Infrastructure: The Role of SBOMs appeared first on RunSafe Security.
]]>The post Memory Safety Through Hardening System Code appeared first on RunSafe Security.
]]>Memory Safety Through Hardening System Code
Protecting vulnerable systems
A static target is a sitting duck. However, we all know that hitting a moving target can be far more challenging—as it involves accounting for the target’s speed, direction, and distance. Then there are other factors, such as the attacker’s skill, the type of weapon used, and environmental conditions, which also play a significant role in determining the difficulty of hitting a moving target. The embedded software world, the world in which our country’s critical infrastructure (government, business, military, utilities, and more) exists, and is utilized and repurposed, is a static target. That’s changing. It has to change. The embedded software of our most vital systems is vulnerable…and constantly under attack.
Weapons systems, in particular, are tempting targets. According to Schneier on Security, “Our military systems are vulnerable. We need to face that reality by halting the purchase of insecure weapons and support systems and by incorporating the realities of offensive cyberattacks into our military planning. Over the past decade, militaries have established cyber commands and developed cyberwar doctrine. However, much of the current discussion is about offense. Increasing our offensive capabilities without being able to secure them is like having all the best guns in the world, and then storing them in an unlocked, unguarded armory. They just won’t be stolen; they’ll be subverted.”
This blog is obviously speaking to the broader aspects of cybersecurity. But the point is valid. When it comes to cybersecurity, we need to turn our focus toward defense. Defending our weapons systems’ memory-based vulnerabilities. And defending the memory-based vulnerabilities in all of our critical infrastructure.
From Static to Moving
For more than a year now, the U.S. government has been communicating the severity of the risk that memory-based vulnerabilities pose in embedded software deployed across critical infrastructure. According to MITRE, 3 of the top 8 (and 8 of the top 25) most dangerous software weaknesses are memory safety related. Microsoft and Google have each stated that software memory safety issues are behind approximately 70% of their vulnerabilities. The NSA recommends that software producers using C and C++ languages should rewrite their products in memory-safe languages such as Rust (a modern version of C and C++ that ensures that programmers write stable and extendable, asynchronous code).
But therein lies the heart of the problem. Making the move to memory-safe languages is more than difficult. It’s both time- and cost-prohibitive to rewrite all your system code in another language. So how do you ensure memory safety, and thereby close the loopholes that adversaries are taking advantage of? The key is in how we think about it. We must shift our thinking away from merely patching problems toward a more strategic approach. Let’s not just fill in the holes in the road (again and again and again); let’s build a new road!
The first step in taking immediate action toward solving the problem is to research what other options are available. Existing scanning, patching, and monitoring tools do not solve the memory vulnerabilities inherent in C and C++ coded systems. Perhaps it’s time to consider a solution that would protect your current code, while you make the transition to memory-safe languages for future coding. It’s important to look for tools that will enable your software development team to achieve memory safety without rewriting code and without affecting system performance.
Specifically, this suite of tools should cover the three most common use cases: dropping security into the code at build time, downloading protected versions of open-source software packages, and flagging instabilities and vulnerabilities at runtime.
Risk Assessment
Currently, attackers have the advantage over defenders in cybersecurity. The right tool looks to shift the balance of power from the attacker to the defender while preventing data loss. To shift the balance of power, you first need to know how exposed your software is to memory-related exploits. That is, a risk assessment.
The right tool will utilize the National Vulnerability Database (NVD) to analyze software vulnerabilities in hundreds of thousands of software packages (open-source, commercial, and proprietary software) and use a fast and powerful methodology to examine the software bill of materials (SBOM), assess the risk to the system, and alert stakeholders.
Lastly, the tool you choose should automate the hardening of high-risk code with moving-target defense technologies, reducing the attack surface by eliminating the exploitation of entire classes of vulnerabilities and data theft.
You want insights within minutes, including a detailed list of recommendations.
Hardening the Code
As discussed, the toughest target to hit is a moving target. You want to turn your code into that moving target, hardening your code using load-time function randomization (LFR). This stops hackers from exploiting memory-related vulnerabilities. Rather than taking 5-10 years and millions (if not tens of millions) of dollars to rewrite every line of code to memory-safe languages, LFR can be applied in minutes without rewriting software.
This software diversity relocates where functions load into memory uniquely for every software load for each instance deployed, denying attackers the ability to exploit memory-based weaknesses.
With no new software and no change in the lines of code, there is no change in system performance and no change in functionality. It’s important to employ Moving Target Defense (MTD)-related techniques for this approach, so the hardening process does not incur performance overhead. That way, there is no way for hackers to know distances between functions or create exploits that take advantage of knowing how functions are laid out, let alone launch and scale attacks on your systems.
Hardening the code helps you achieve the transition from a static target to a moving target, reducing the software attack surface by eliminating the exploitation of software memory issues and protecting your data.
The post Memory Safety Through Hardening System Code appeared first on RunSafe Security.
]]>The post Securing Critical Infrastructure in the Digital Age appeared first on RunSafe Security.
]]>Securing Critical Infrastructure in the Digital Age
Understanding the NCSIP and its Pillars
RunSafe Security’s Commitment to NCSIP Execution
Promoting Software Development Practice Accountability
Securing Critical Infrastructure in the Digital Age
With digital connectivity and technological advancement dominating everything we do, protecting critical infrastructure has become a paramount concern for IT leaders across various sectors.
The Cybersecurity and Infrastructure Security Agency’s (CISA) National Cybersecurity Strategy Implementation Plan (NCSIP) stands as a comprehensive roadmap, comprising five key pillars to fortify digital defenses and secure the vital systems powering the nation. In this context, RunSafe Security emerges as a pivotal player, actively contributing to the execution of the NCSIP and addressing key challenges IT leaders face.
Understanding the NCSIP and its Pillars
The NCSIP, developed by CISA, delineates a strategic plan encompassing five pillars for safeguarding the digital landscape. These pillars are:
- Defending Critical Infrastructure: Recognizing the significance of sectors like energy, healthcare, and transportation, the NCSIP emphasizes the need to defend critical infrastructure from cyber threats. This includes fostering coordinated government action and collaboration with private sector partners.
- Disrupting and Dismantling Threat Actors: Acknowledging the dynamic nature of cyber threats, the NCSIP underscores the importance of disrupting and dismantling malicious actors. This involves concerted efforts to combat ransomware and cybercrime through initiatives such as the Joint Ransomware Task Force.
- Shaping Market Forces and Driving Security: The NCSIP highlights the role of market forces in driving security and resilience. Key to this is increasing software transparency, allowing market actors to understand their supply chain risk better. This includes addressing gaps in Software Bill of Materials (SBOM) and exploring the development of a globally accessible database for end-of-life software.
- Investing in a Resilient Future: Recognizing the evolving challenges in cybersecurity, the NCSIP strongly emphasizes investing in a resilient future. This involves driving essential cybersecurity standards, ensuring U.S. leadership in international cybersecurity standardization, and preparing for emerging threats like quantum-resistant cryptographic algorithms.
- Forging International Partnerships: In an interconnected world, collaboration is essential. The NCSIP underscores the importance of forging international partnerships to pursue shared cybersecurity goals. This involves developing an International Cyberspace and Digital Policy Strategy to facilitate collaboration with global partners.
RunSafe Security’s Commitment to NCSIP Execution
RunSafe Security has demonstrated a firm commitment to contributing significantly to the execution of the NCSIP. As a specialized entity in mitigating risks associated with software vulnerabilities in critical infrastructure, RunSafe focuses on addressing gaps in SBOM and enhancing software transparency across the software supply chain.
The company actively contributes to defending critical infrastructure by implementing advanced techniques to identify and eliminate vulnerabilities within software. This proactive approach significantly reduces the attack surface for potential cyber threats, aligning with the NCSIP’s goal of staying ahead of adversaries.
The NCSIP recognizes the importance of software transparency in shaping market forces for increased security and resilience. RunSafe addresses this by working with key stakeholders to identify and reduce SBOM scale and implementation gaps.
Investing in a resilient future, RunSafe actively participates in efforts to drive necessary cybersecurity standards and standardize quantum-resistant public key cryptographic algorithms, contributing to the ongoing evolution of cybersecurity measures.
With the global nature of cyber threats, RunSafe also actively advocates for collaboration among all players across the software supply chain, including international entities, to share threat intelligence, best practices, and innovative solutions. These efforts contribute to the NCSIP’s goal of creating a united front against cyber adversaries.
Promoting Software Development Practice Accountability
In addition to aligning with the NCSIP pillars, RunSafe Security strongly emphasizes advocating for improved software development practices and accountability. The company encourages adopting secure coding practices and integrating security measures throughout the software development lifecycle.
By promoting software development practice accountability, RunSafe empowers organizations to build resilient software from the ground up. This approach resonates with the NCSIP’s objective of fostering a secure and resilient digital ecosystem.
Through training, cybersecurity services, technical assessments, pre-attack planning, and incident response, RunSafe actively reduces the likelihood and impact of ransomware attacks on high-risk targets such as utility facilities and schools.
In conclusion, the National Cybersecurity Strategy Implementation Plan serves as a strategic guide to safeguarding our digital future, and RunSafe Security has emerged as a crucial ally in its execution, actively contributing to the pillars of defending critical infrastructure, disrupting threat actors, shaping market forces, investing in a resilient future, and forging international partnerships.
As cyber threats continue to evolve, the urgency to take action becomes increasingly evident. Organizations must recognize the importance of implementing robust cybersecurity measures, and RunSafe Security provides the necessary tools and expertise to navigate the complex cybersecurity landscape.
When digital resilience is paramount, RunSafe leads the way toward a secure and interconnected future. By investing in RunSafe’s cybersecurity solutions, businesses address current threats and contribute to the collective effort of building a resilient digital infrastructure in line with the NCSIP’s vision. Together, we can navigate the challenges of tomorrow and build a secure and interconnected future.
The post Securing Critical Infrastructure in the Digital Age appeared first on RunSafe Security.
]]>The post Secure by Design: Building a Safer Digital Future appeared first on RunSafe Security.
]]>Security Challenges and the Secure by Design Report:
The increasing frequency and sophistication of cyber threats have exposed vulnerabilities in digital systems, prompting the need for a proactive and holistic approach to cybersecurity. The Secure by Design initiative emerged in response to these challenges, aiming to transform the cybersecurity landscape by embedding security principles into the very fabric of digital systems.
The Secure by Design Report is a crucial document outlining the principles and strategies that form the foundation of this initiative. Released by CISA, the report delves into the importance of secure design practices and highlights their critical role in mitigating cyber risks.
What is Secure by Design?
Secure by Design, as defined by the CISA report, is an approach that integrates security considerations throughout the product development lifecycle. It emphasizes the proactive incorporation of security features and practices during the design phase, ensuring that cybersecurity is not an afterthought but an inherent aspect of the system.
The importance of Secure by Design cannot be overstated.
In an interconnected world where digital systems permeate every aspect of our lives, vulnerabilities in one area can have cascading effects. The Secure by Design approach seeks to address this by building resilient systems that can withstand cyber threats from the outset.
Manufacturers of digital products play a pivotal role in this paradigm shift. Failing to embrace Secure by Design principles can result in dire consequences, ranging from data breaches and financial losses to reputational damage. The urgency for product manufacturers to prioritize security in their design processes has never been greater.
What is Secure by Default?
Secure by Default is another critical aspect of CISA’s initiative. It entails configuring products and systems with the most secure settings as the default, minimizing the need for users to make manual adjustments to enhance security. This approach aims to reduce the risk of misconfigurations and ensure that security is not compromised due to user oversight.
Secure by Design and Secure by Default are interconnected concepts, but they address different product life cycle phases. Secure by Design is concerned with integrating security into the design and development stages, while Secure by Default focuses on ensuring that products are configured securely from the outset.
Together, these principles create a robust defense against a wide array of cyber threats.
How RunSafe Fulfills Secure by Design and Secure by Default:
RunSafe aligns closely with the principles of Secure by Design and Secure by Default, notably advocating for making products resilient against the most prevalent threats and vulnerabilities without requiring end-users to take additional actions.
RunSafe emphasizes proactive security measures in the early stages of product development with the manufacturers, integrating security into the design process. In doing this, RunSafe ensures that the products are inherently resistant to a wide range of cyber threats. This approach safeguards against known vulnerabilities and anticipates emerging risks, providing a dynamic defense mechanism.
RunSafe goes beyond conventional practices with code hardening to ensure the highest level of security protocols as the default. This minimizes the likelihood of recurring incidents after patches that could continue to compromise security.
RunSafe’s commitment to Secure by Default reflects a dedication to delivering solutions that prioritize critical infrastructure safety and security.
Recommendations for Software Manufacturers:
CISA’s Secure by Design initiative outlines three fundamental principles that software manufacturers should embrace to enhance the security posture of their products. Each principle serves as a roadmap for creating resilient and secure digital systems.
Principle 1: Own Security Outcomes
Take ownership of customer security outcomes and evolve products accordingly. The burden of security should not fall solely on the customer.
The report emphasizes that software manufacturers should integrate application hardening through processes and technologies that increase the difficulty for malicious actors attempting to compromise applications. Application hardening protocols and procedures are vital in enabling products to withstand attacks from intelligent malicious actors. Concepts such as hardening, product security, and resilience are closely intertwined with product quality, emphasizing the necessity for security to be seamlessly integrated rather than added as an afterthought.
Two ways that RunSafe demonstrates this principle are:
1. Responsibly using open source software: Beyond standard vetting, fostering code contributions back to dependencies, and helping sustain development and maintenance for critical components, RunSafe Code™ utilizes patented Moving Target Defense (MTD) techniques to fortify software during the design phase. This involves dynamically relocating where functions load into memory, creating a unique configuration for every software load and each deployed instance.
Since this is implemented in the design phase, no new software is introduced through patches, and no alteration of lines of code occurs. Consequently, there is no impact on system performance or functionality.
To provide additional transparency across the software supply chain, RunSafe offers an automated software bill of materials (SBOM) through its Gremlin product. Generated at compilation time, the comprehensive SBOM ensures developers have a clear snapshot of all software components at play.
2. Providing secure defaults for developers: Manufacturers should make the default route during software development secure by providing safe building blocks for developers. RunSafe solutions, applied to the build root like the way LYNX MOSA.ic is secured, become the default settings, ensuring protection against 70% of the most common vulnerabilities with no developer impact.
Principle 2: Transparency & Accountability
Embrace radical transparency and accountability. Software manufacturers ought to provide products that prioritize safety and security. This differentiation may involve the transparent sharing of insights gained from customer deployments, such as the widespread adoption of robust authentication mechanisms by default.
Additionally, manufacturers should exhibit a dedicated effort to maintain the completeness and accuracy of vulnerability advisories and associated Common Vulnerability and Exposure (CVE) records. However, caution is advised against viewing CVE counts solely as negative metrics, as these numbers can also signify a robust and active code analysis and testing community.
Runsafe’s solutions contribute to the recommended secure product development practices, particularly the advice to Embrace vulnerability transparency and Publish Software Bills of Materials (SBOMs). Due to RunSafe’s dedication to full compliance and proactive software immunization, it’s advantageous for manufacturers to publish vulnerabilities with the associated mitigations labeled as “protected by RunSafe.”
In addition, RunSafe’s automated SBOMs through Gremlin fulfill CISA’s recommendation to “build and maintain SBOMs for each product, request data from their suppliers, and make SBOMs available for downstream customers and users.” It’s important to consider varying types of SBOMs – build-time vs. binary-based – to determine which provides the most benefit to creating supply chain transparency.
One pro-security business practice that RunSafe supports is the publication of a memory-safety roadmap. Leveraging memory-safe languages enables manufacturers to make progress toward eliminating one of the largest classes of vulnerabilities.
Principle 3: Leadership
Build organizational structure and leadership to achieve these goals. While technical subject matter expertise is critical to product security, senior executives are the primary decision-makers for implementing organizational change. Executives need to prioritize security as a critical element of product development across the organization, and in partnership with customers.
RunSafe embodies the principles of Secure by Design and Secure by Default. Leading the charge and advocating for premium security measures, RunSafe stands as a reliable and trustworthy source of information for executives looking to better understand the best practices to implement Secure by Design practices.
After analyzing thousands of binaries and hundreds of thousands of functions using open-source software, RunSafe Security was able to show that there weren’t enough bits of code to misuse at a function-level, to create attacks that work on unprotected code.
Conclusion
CISA’s Secure by Design initiative presents a transformative approach to cybersecurity, emphasizing the integration of security into the very fabric of digital systems. Given the escalating cyber threats in today’s landscape, the urgency for product manufacturers to adopt these principles is evident.
The long-term benefits of embracing Secure by Design and Secure by Default are profound. As digital systems become increasingly integral to our critical infrastructure, a proactive and comprehensive security approach will not only safeguard against current threats but also future-proof products against emerging risks. The collaborative efforts of organizations like CISA and companies like RunSafe are instrumental in creating a resilient and secure digital ecosystem for generations to come.
The post Secure by Design: Building a Safer Digital Future appeared first on RunSafe Security.
]]>The post Safeguarding LYNX MOSA.ic: Lynx and RunSafe’s Security Partnership appeared first on RunSafe Security.
]]>Safeguarding LYNX MOSA.ic: Lynx and RunSafe’s Security Partnership
Why does memory safety matter to Lynx users?
No impact on Runtime performance? Development schedule?
Easier compliance with security requirements
What about the Software Bill of Materials?
How to immunize LYNX MOSA.ic against 70% of code vulnerabilities?
Safeguarding LYNX MOSA.ic: Lynx and RunSafe’s Security Partnership
RunSafe Security is excited to announce a strategic partnership with Lynx Software Technologies (Lynx). The partnership between Lynx and RunSafe protects LYNX MOSA.ic against 70% of the most common vulnerabilities with no developer impact.
At the launch of the partnership with Lynx Software Technologies, the RunSafe protection applies to the build root Linux operating system, applications, and customer software. In early 2024, the team intends to release the LynxOS-178 version of the protections.
The segments, including aircraft manufacturers, industrial controls, defense systems, and IOT devices, are really challenged with meeting desired delivery schedules at a time when system complexity is increasing at a fast rate. Our effort here with Lynx is beyond “marketecture” and PowerPoint. The purpose of this engagement is to deliver RunSafe technology as a proven component in LYNX MOSA.ic. The “ic” stands for Integration Center and we fully believe that one critical piece in enabling reductions in program risk and development schedule comes from integrating cybersecurity protections during the product development process. Lynx will deliver RunSafe’s technology as part of its LYNX MOSA.ic product.
Why does memory safety matter to Lynx users?
Prevalence of Memory Safety Bugs
In compiled code, memory safety bugs are the single largest class of bugs. In the embedded and real-time operating system spaces, compiled code represents the vast majority of code. A few statistics, based on research at North Carolina State University:
- Typically 70% of the bugs in compiled code are memory safety issues.
- Memory safety bugs have a much more severe impact on systems, according to their average severity scores (NVSS).
- 59% of memory-related code vulnerabilities have been weaponized, with exploits readily available.
- Memory safety bugs tend to take much longer for developers to fix, relative to non-memory safety bugs (180 days for memory safety vs 90 days for non-memory safety).
Patching Deployed Systems is Difficult
Time is on the side of the attackers. Deployment cycles of systems in military, aerospace, and federal markets are long. In the case of planes, they can be measured in decades. Patches are hard to deploy to these complex, fielded systems. Meanwhile, highly resourced and skilled attackers develop cyber kill chains, finding (or buying on the dark web) zero days. With RunSafe, systems running Lynx RTOS are protected and future-proofed against the majority of these zero-day attacks without patching.
Regulatory Drivers
For those Lynx customers selling to US government programs, there is an increased focus on the memory safety of acquired systems and software. Figure 1 below shows actions undertaken by the US government to tighten up memory safety.
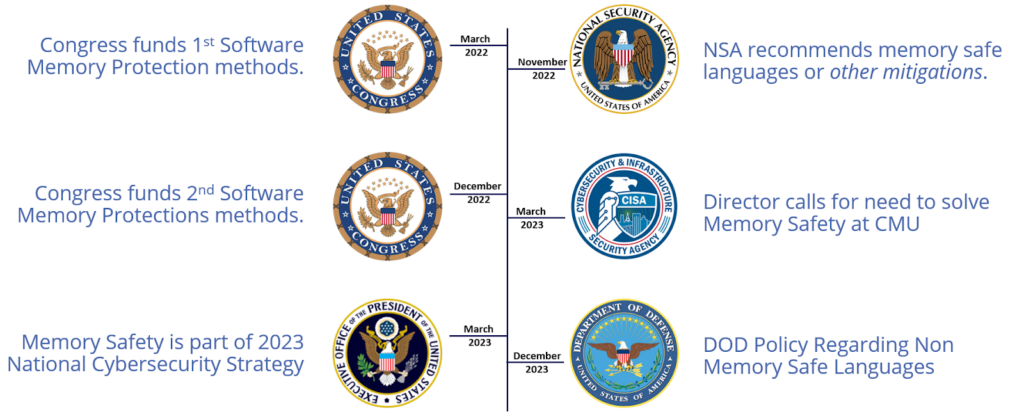
Figure 1
No impact on Runtime performance? Development schedule?
The process of reordering the functions happens when the process is set up in memory. Instead of jumping right to the normal entry point for the function, the binary reorders its functions first. Then it begins normal operations. This reordering of memory typically adds only 1%-3% to process setup time. If a function took 1 second to load before, it will now load in 1.01 to 1.03 seconds.
From that point forward, the RunSafe protection is passive. There is no change in the sheer instruction count, control flow, etc. There are no additional memory reads, writes, lookups, etc. Our customers, even on the most stringent real-time systems, have never found a measurable impact on runtime performance.
Easier compliance with security requirements
Lynx customers are better able to document their compliance with RMF (DoDI 8510.01), which incorporates NIST 800-53. Consequently, programs accelerate time to ATO at a lower cost. For high-impact systems, RunSafe enhances compliance with more than 20% of the controls. For many RunSafe-impacted controls, the only alternative is thousands of hours of testing.
RunSafe provides “last-mile integrity” into the running memory, increasing confidence that the code operates in memory the way the developer intended. By mitigating an entire class of vulnerabilities, RunSafe makes possible incident handling responses that were previously impossible. This protection can be applied to every layer of the system’s software. Table 1 shows the breakout of impacted controls across the various levels of system integrity. A whitepaper with more details about the NIST 800-53 controls can be found here.
Table 1
What about the Software Bill of Materials?
Machine-readable SBOMs are being required by EO14028 and making their way into FAR clauses. RunSafe’s tools make it possible to build a complete and perfect SBOM for each Lynx project, regardless of whether a package manager is used for the compiled code, or not. By working into the build process, RunSafe is able to identify every file coming into the build, every dependency, library, include file, etc., and build a perfect tree of dependencies between the components. For Lynx Software Technologies customers, this is a zero-effort activity.
How to immunize LYNX MOSA.ic against 70% of code vulnerabilities?
A future webinar and configuration document will describe the configuration steps, but this would involve a slight change to a build script, instructions on where to include the license key, and which configuration files to edit. No other changes are necessary (see figure 2).
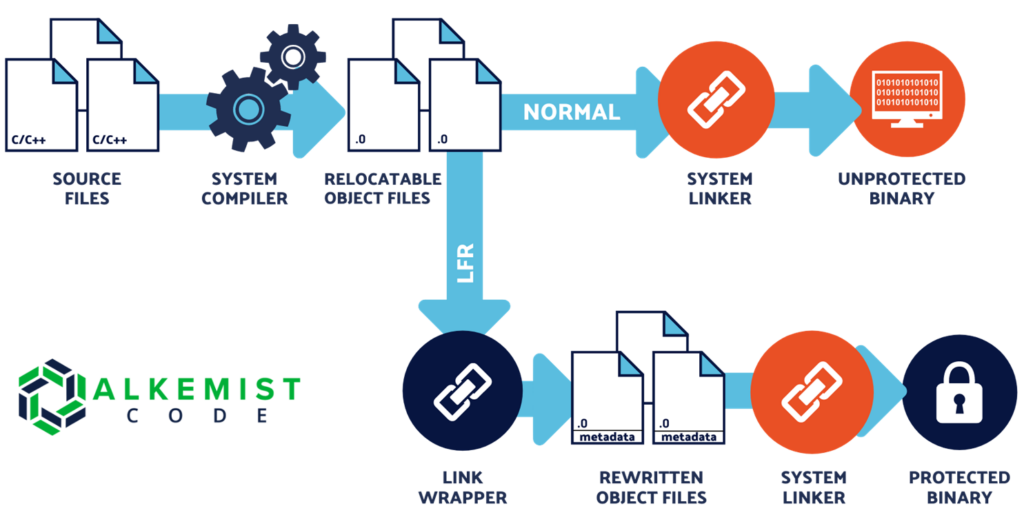
Figure 2
How does RunSafe Security Code protect the OS and applications?
Memory safety bugs (stack overflows, heap overflows, etc.) wreak havoc on their targets by using code already in memory in unintended ways. For example, by moving the instruction pointer one byte past an add instruction, the processor may execute a branch instruction. For these attacks to work, the attacker must have highly predictable insight into the layout of memory on the victim process.
Figure 3 below shows a few different memory scenarios. The first column is the memory layout if no protection is applied. This gives the attacker a perfectly deterministic layout across all devices. The second column shows the protection of a technique called Address-Space Layout Randomization (ASLR). This randomizes the base address of binaries or libraries, but t威而鋼
he body of the binary will still have a deterministic organization, relative to this base address. Given the prevalence of memory leaks, ASLR hasn’t done much to slow down attackers in the last 15 years. RunSafe’s protection randomizes the individual functions that comprise a binary, as shown in the Fine-grained randomization graphic.
On average, binaries tend to have around 280 functions. That gives our attacker roughly 280(!) permutations to consider. To understand that scale, if an attacker were able to attempt 100 trillion possible randomizations every nanosecond, the attacker would spend 3*10524 universes before they hit every possible permutation.
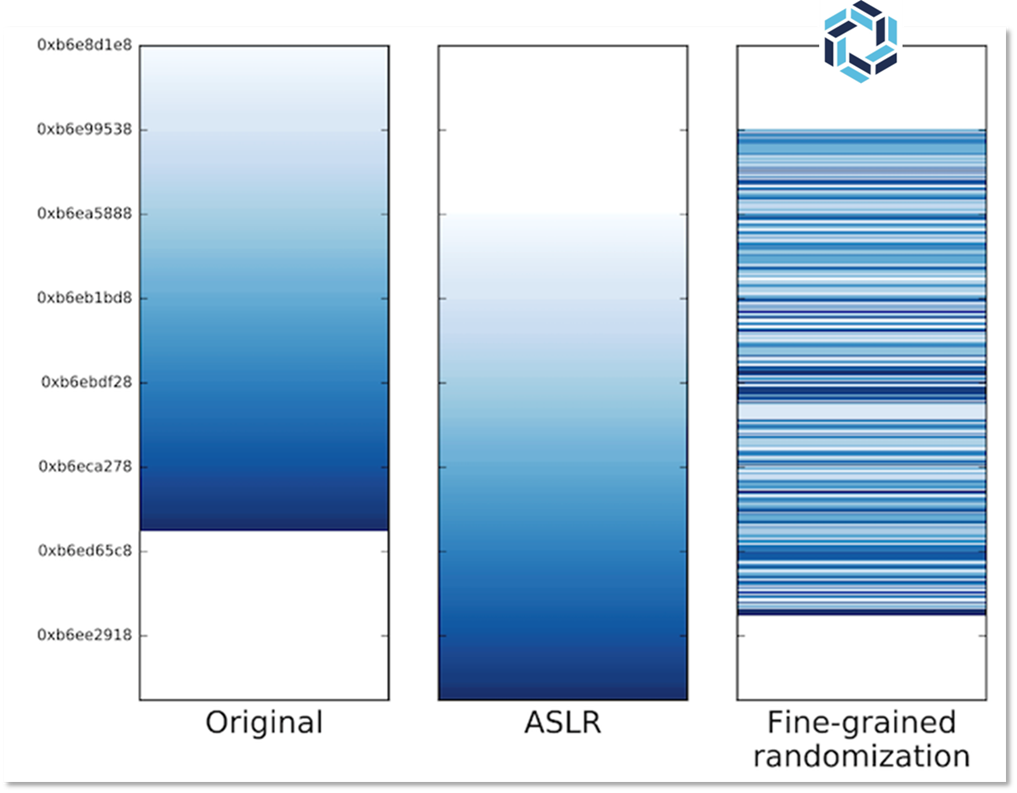
Figure 3
After analyzing thousands of binaries and hundreds of thousands of functions using open-source software, RunSafe Security was able to show that there weren’t enough bits of code to misuse at a function-level, to create attacks that work on unprotected code.
The post Safeguarding LYNX MOSA.ic: Lynx and RunSafe’s Security Partnership appeared first on RunSafe Security.
]]>The post Securing Critical Infrastructure with Memory Safety in Software appeared first on RunSafe Security.
]]>Securing Critical Infrastructure with Memory Safety in Software
The issue at hand: memory vulnerabilities
The challenge of transitioning to memory-safe languages
Current efforts and the role of memory protections
The urgency of the matter: threats on the horizon
Improving critical infrastructure: memory safety now
How secure is the code underpinning our most vital systems? In our increasingly digitized world, memory safety in software has transitioned from a technical detail to a cornerstone of critical infrastructure protection.
As the NSA and other prominent bodies underscore its importance, it becomes evident that software vulnerabilities, especially in C or C++ applications, are not just code flaws but potential gateways for malicious actors. These gateways are particularly concerning when considering infrastructures like energy grids and manufacturing plants powered by industrial control systems (ICS) and SCADA systems. The stakes are high, and the challenges manifold.
Let’s take a deep dive into the memory-based vulnerabilities landscape, the daunting task of transitioning to memory-safe languages, and the innovative solutions, such as RunSafe, that aim to immunize your software today and for the future.
The issue at hand: memory vulnerabilities
Foundational software, especially those running our critical infrastructures, are built on the backbones of C and C++. These languages, while powerful, have an Achilles heel: vulnerabilities arising from their handling of memory.
At its core, the software governing crucial sectors like our energy grids and manufacturing hubs must be flawless. But, in the reality of C and C++-coded systems, memory mismanagement isn’t rare. Such missteps can serve as exploitable vulnerabilities for those with ill intent.
A key concern here is the inherent predictability within these languages. Historically, if a bad actor could decipher vulnerabilities in one software instance, they could design a universally effective exploit. This isn’t a bug but a golden ticket for those with malicious objectives.
To tackle this, it’s not enough to just patch these memory-based vulnerabilities. Instead, the approach needs to be more strategic. We can boost unpredictability by changing how software interacts with memory and introducing elements of randomness in function loads. This makes each software instance unique, diminishing the chances of a single exploit affecting all.
The challenge of transitioning to memory-safe languages
Critical infrastructure sectors often boast an expansive product portfolio, developed and refined over many years. Consider a company with over 1,000 diverse products, each a snapshot of technological innovation at its time of conception. The challenge arises when a sizable fraction of these products, entrenched in our critical infrastructures, are susceptible to memory vulnerabilities.
Transitioning to memory-safe languages for newer software products seems a plausible solution, but what about the legacy? Software products with life spans bridging decades are already deeply embedded in vital sectors. Their transition concerns technical adaptation and logistical, strategic, and continuity considerations.
Amidst these complex shifts, vulnerabilities can subtly emerge. It’s comparable to a structure being most at risk when undergoing renovation. Software can also inadvertently expose itself to unforeseen threats during these transformative phases.
Thus, as industries evolve, striking a balance between embracing the future and ensuring robust memory safety in software becomes an intricate dance; one that demands proactive strategies, innovative solutions, and unwavering vigilance against potential exploits.
Current efforts and the role of memory protections
The cybersecurity landscape is constantly evolving, and as threats grow more sophisticated, so must our defense approaches. At the heart of this evolution is the principle: “secure by design, secure by default.” This philosophy underscores the idea that software must be developed from its inception with robustness and resilience in mind rather than relying on patches and retroactive fixes.
Why does this matter?
For one, we’re talking about more than just individual pieces of software. It’s about the digital backbone of critical infrastructure — the systems that power our factories, manage our utilities, and keep our society running smoothly.
In this sphere, we advocate for preemptive memory protections. Not as an optional add-on but as a foundational layer of defense. While the industry ponders over a holistic shift to memory-safe languages, a gap remains.
What do we do about the here and now?
The answer lies in identifying memory-based vulnerabilities and actively safeguarding against them. By diversifying the memory layout in each software instance, the predictability, a significant advantage for adversaries, is negated. Every attempt to exploit becomes a unique challenge, deterring large-scale attacks.
The RunSafe suite of tools reflects this philosophy, emphasizing code hardening to ensure resilient applications. Instead of merely providing a bandaid, we focus on true resilience.
From integrating security at the code’s build phase to offering protected versions of open-source software and real-time vulnerability alerts, our approach is comprehensive. By leveraging RunSafe code hardening techniques, software becomes more resilient and more unpredictable to potential attackers.
The urgency of the matter: threats on the horizon
In the ever-turbulent realm of geopolitics, the ripples of conflict don’t just reverberate on the battlefield; they cascade into the cyber arena. Take, for instance, the escalating tensions between China and Taiwan. Beyond the immediate geopolitical ramifications, such conflicts have profound implications for cybersecurity, particularly concerning critical infrastructure.
With its vast interconnected digital networks, U.S. infrastructure presents a tempting target in these tense situations. And as history has shown, where there’s political tension, cyber-espionage and cyber-attacks are seldom far behind. State-sponsored digital incursions can often disrupt systems, cause considerable financial losses, and even endanger lives.
An exploitable critical weak point in these scenarios is memory vulnerabilities. Every unsecured code line, every unprotected function, becomes a potential entry point. And in a large-scale conflict, these weak spots can be exploited for espionage and sabotage. Imagine the chaos if a nation’s energy grid, transportation systems, or communication networks were compromised during a crisis.
The message is clear: the need for comprehensive memory protection is not a distant future requirement – it’s an immediate necessity. As geopolitical tensions loom, the urgency to immunize our software from potential exploitation has never been more pressing.
Improving critical infrastructure: memory safety now
In today’s rapidly advancing cyber landscape, the need for robust memory protections is more evident than ever. RunSafe champions this philosophy of applying memory protections today as a pragmatic bridge to the memory-safe languages of tomorrow. While the allure of these new languages is undeniable, the transition will require time — time that critical infrastructures might not have, especially in the face of rising cyber threats.
Every moment we wait, we leave our critical infrastructure — the backbone of our nation’s economy, safety, and well-being — vulnerable to debilitating attacks. With every delay, we edge closer to the precipice of cyber catastrophe. RunSafe’s approach serves as a sentinel in these challenging times, offering an immediate solution that doesn’t demand the upheaval of current systems or delay essential protections.
While the future lies in memory-safe languages, the present calls for immediate action. To ensure the security and integrity of our critical systems, don’t wait for tomorrow. Connect with RunSafe today and fortify your defenses against the threats of the digital age.

The post Securing Critical Infrastructure with Memory Safety in Software appeared first on RunSafe Security.
]]>The post Securing the Future: Understanding the Unique Challenges of Industrial Control Systems (ICS) Security appeared first on RunSafe Security.
]]>Securing the Future: Understanding the Unique Challenges of Industrial Control Systems (ICS) Security
Why ICS is vulnerable to cyber attacks
The role of cyber hardening in ICS security
Answering the call to secure our future
Picture this: you wake up in the morning, the coffee machine is already brewing your daily cup, the traffic lights are coordinating to ensure you get to work on time, and the power grid is working flawlessly to keep the lights on. These little conveniences are powered by something called Industrial Control Systems (ICS).
But, here’s the catch–these systems are kind of like the behind-the-scenes crew in a play; not always visible, but absolutely crucial.
We’re deeply invested in protecting these hidden heroes. Why? Because we know that ICS is not just about convenience; it’s about safety, productivity, and the very fabric of our day-to-day lives. We’re passionate about shielding these systems.
We’ll take you on a journey to understand why ICS security is critical, what threats lurk in the shadows, and how RunSafe’s code-hardening magic acts like an impenetrable shield for ICS.
The threats to ICS security
In the complex landscape of the cyber domain, ICS serves as the linchpin of modern society’s infrastructure, silently ensuring the seamless operation of critical processes. However, these critical infrastructures, despite their significance, are not unbreakable fortresses. Their susceptibility to intrusion and compromise makes vigilance and a strong line of defense necessary, even in military systems.
Let’s delve into real-world examples that underline the importance of fortifying these vital systems.
- U.S. Natural Gas Ransomware Attack:
-
- In early 2020, a U.S. natural gas compression facility faced a ransomware attack that had a domino effect, halting operations for two full days. The crafty attackers used spear-phishing to infiltrate the facility’s IT network and didn’t stop until they got to the operational technology (OT) network. Although the facility didn’t lose control over operations, they decided to hit the brakes for safety. The cyber incident revealed that while they had an emergency plan for physical threats, cyber-attacks were like uncharted waters.
- Northern Israel Irrigation Sytems
- In April 2023, hackers hit Northern Israel’s irrigation systems and Galil Sewage Corporation’s controls. Despite warnings from the National Cyber Directorate to disable remote connections, some folks didn’t act fast enough. Michael Langer of Radiflow disclosed that the hackers meddled with Unitronics’ programmable logic controllers. This wasn’t random – it was part of OpIsrael, a campaign with a knack for targeting human-machine interfaces. It’s a classic tale of what happens when the essentials, like changing default passwords, take a back seat.
- Stuxnet:
- Consider Stuxnet, discovered in 2010; it was an exploit that targeted Iran’s nuclear program – and more precisely its industrial control systems (ICS).
Once inside the ICS, Stuxnet manipulated the code running on the programmable logic controllers, specifically the ones responsible for controlling the centrifuges used in the uranium enrichment process. By subtly altering the speed and operation of the centrifuges, Stuxnet ultimately crashed the systems in Iran’s facility without prior detection.
Why ICS is vulnerable to cyber attacks
Why is ICS especially vulnerable?
Many of the systems have been around for a while; they’re the grizzled veterans of the industry. While they’re superb at what they do, they weren’t designed with modern cybersecurity in mind. Moreover, the rise of the Industrial Internet of Things (IIoT) means more connectivity and, by extension, more vulnerabilities.
These aren’t just isolated incidents; they’re part of an ongoing cyber onslaught that needs sophisticated defenses. We recognize the value that ICS brings to our day-to-day life, and we’ve committed ourselves to protecting these systems with our technology.
What if a similar type of cyber attack to Stuxnet were to target critical infrastructure systems within the United States? Water systems, gas pipelines, oil rigs, power grids, transportation infrastructure, financial systems, and weapons programs could all be at risk. The disruption caused by such attacks would jeopardize the essential services and mission-critical systems upon which we depend everyday to support a well-functioning society.
The role of cyber hardening in ICS security
Our mission is to harden the code that runs the ICS, turning them into fortresses. But what does code hardening mean? Imagine you could constantly shuffle the inner workings of a system so that attackers can never get a read on how it’s structured. It’s like trying to hit a moving target while blindfolded–nearly impossible!
Besides, there’s a treasure chest of open-source software out there that’s gold for ICS functionality. But guess what? They too, can be exploited. RunSafe has that covered as well.
By hardening code, we’re ensuring that if an attacker somehow makes it through the outer defenses, the castle keep is a maze that changes every time they turn a corner. RunSafe is turning ICS security into a fortress that is not just strong, but also smart.
Answering the call to secure our future
We’ve taken you on quite a journey today, from malicious cyber threats to strong defenses in code hardening. Industrial Control Systems are fundamental to modern civilization, and safeguarding them is not just an option; it’s an imperative.
At RunSafe, we believe in equipping ICS with the best armor technology can offer. With our innovative cyber hardening techniques, we are not just defending; we are outsmarting the enemy.
We ask you, the stakeholders and caretakers of critical infrastructure, to recognize the value and urgency of this mission. Stand with us as guardians at the gate. Together, we can ensure the conveniences we so often take for granted are preserved and protected for generations.
Let’s build a future that’s not just secure, but unassailable. Team up with RunSafe and be the champions of a modern-day fortress. Secure your ICS, and with it, secure the future.
The post Securing the Future: Understanding the Unique Challenges of Industrial Control Systems (ICS) Security appeared first on RunSafe Security.
]]>The post From Software Bill of Materials to Automated Remediation Across your Software Supply Chain appeared first on RunSafe Security.
]]>From Software Bill of Materials to Automated Remediation Across your Software Supply Chain
The World’s Most Complete SBOM
Addressing Open Source Software Vulnerabilities
The Future of Software Supply Chain Security
Today we released our expanded product offering, complete with the ability to generate a software bill of materials while also automating the remediation of vulnerabilities across your software supply chain – all within your CI build tools, such as GitLab or GitHub.
The World’s Most Complete SBOM
Based on customer feedback, we learned that even though a software bill of materials is a foundational step to understand the risk in your software products – and necessary for sharing with customers what is contained in deliveries to them – not all SBOMs are created equal.
Take compiled code written in C/C++. Whereas most companies derive an SBOM from the software binary, resulting in missing information, RunSafe generates the SBOM during the build process where we have perfect information about what goes into your product.
As a result, whether you need to generate an SBOM, search it for underlying components that may contain vulnerabilities, or need to store and retrieve data for future use, Gremlin creates the most complete SBOM while saving your developers time.
Addressing Open Source Software Vulnerabilities
But that’s not all. Because as much as 60-80% of code in your products come from open source repositories, we learned reducing the attack surface given a complex software supply chain is consuming scarce resources and preventing developers from building new features.
With Gremlin, we incorporated the world’s most efficient and effective automated remediation so developers can ship software with radically reduced attack surface – and no additional work. With RunSafe protections built in, our customers can not only share the most complete SBOM but also highlight how they protected individual components from exploitation.
The Future of Software Supply Chain Security
And we are not done. In the near future, we will roll out additional features for you. We plan to help you gain insights on all the vulnerabilities associated with components in your SBOM, demonstrate how much attack surface you can eliminate with a click of a button, calculate your exposure to any further zero days yet to be discovered, and even alert you when new vulnerabilities are discovered or remediated.
We also believe you will have more ideas on how to enhance the automated management of software supply chain risk without slowing down your developers. Please reach out if you have questions and feel free to start a free trial here. We welcome your feedback.
The post From Software Bill of Materials to Automated Remediation Across your Software Supply Chain appeared first on RunSafe Security.
]]>The post Cyber Hardening in the Modern Age: Why Military Systems Need to Keep Up appeared first on RunSafe Security.
]]>Cyber Hardening in the Modern Age: Why Military Systems Need to Keep Up
Cyberattacks on Military Systems Are Nothing New
How Can We Effectively Cyber Harden Our Military Systems?
Every person worldwide, from the girl next door to top-secret military personnel and diplomats, is deeply rooted online. From how we work and play to how we learn and worship, cyberspace has consumed every facet of our daily lives. Our reliance on cyberspace extends to the ways we govern and protect our countries.
As such, cyberattacks have become among the world’s gravest dangers. Not only can they impact our bank accounts, but exploits can also disrupt power grids and threaten national security.
Currently, the United States Department of Defense (DoD) is “hardening” its systems, which involves eliminating cyberattacks by patching vulnerabilities and switching off nonessential services, sensors, and networks against such attacks. Across the pond, the UK’s Defense and Security Accelerator (DASA) is taking the same precautions in the form of a new Innovation Focus Area (IFA) to identify and implement technologies that will improve the Ministry of Defense’s resilience against cyberattacks.
Cyber hardening, or eliminating cyberattacks by patching vulnerabilities and switching off nonessential services, is paramount in the digital age. But how secure are our military systems, and what can we do to protect them?
Cyberattacks on Military Systems Are Nothing New
The threat of cyberattacks on military network security systems isn’t a new problem. In fact, it’s been an issue since computers were first introduced to US Navy war rooms during World War II. However, as our dependency on technology grew, so did our risks.
Cyber warfare, or cyberattacks that target critical infrastructure, including military weapons, can be deadly to both the military and civilians. Some of the most common types of cyber warfare include exploits leading to espionage, sabotage, and denial-of-service (DoS) attack. These attacks can cause mass power outages, economic disruption, and even death.
A few significant examples of cyber warfare in modern times include:
- Stuxnet Virus: This worm attacked Iran’s nuclear program and was spread through infected Universal Serial Bus devices.
- Sony Pictures Hack: In 2014, a hacker group called Guardians of Peace released confidential data from Sony Pictures, including personal information about Sony employees and their families. The hackers demanded that Sony withdraw its movie The Interview, which depicted North Korean leader Kim Jong-un in a negative light.
- Fancy Bear: A Russian-organized group of cybercriminals targeted Ukrainian artillery and rocket forces between 2014 and 2016. The malware was spread through infected Android apps used by the artillery unit to manage data.
- NASA Hack: In 1999, a 15-year-old boy named Jonathan James hacked into the US Department of Defense and NASA, stealing valuable software used to support the International Space Station.
Seeing that even bored teenagers can hack into government systems, it’s vital that the military efficiently protects itself and takes the necessary precautions to pinpoint software vulnerabilities.
Deadly Consequences
The consequences of a cyberattack on military systems can be far-reaching. Not only can it jeopardize critical infrastructure, but it can put both military personnel and civilians at risk. Sensitive information can be sold on the dark web to hack bank accounts and steal identities. In addition to impacting people, cyberattacks can jeopardize a company’s compliance, reputation, and profits.
Cyber terrorists can also disable crucial operations and systems, disrupt infrastructures, target the supply chain, render communications—like texting—unusable, spread propaganda, and weaken a country’s defenses against a massive physical attack.
How Can We Effectively Cyber Harden Our Military Systems?
So, how can the military reduce surface attacks and efficiently harden its embedded systems?
In an official statement, the White House urged all organizations to do the following:
- Mandate the use of multi-factor authentication for all systems
- Ensure all systems are patched and protected against vulnerabilities
- Implement modern security tools on all devices and computers
- Encrypt and back up all data
- Educate employees on common cyberattack strategies
Military systems can take additional steps to improve their protection and risk management strategies by educating employees and investing in advanced cybersecurity equipment and technology, like RunSafe Security.
RunSafe can drastically reduce military systems’ risk of cyberattacks without disrupting software developers and maintainers. Our technology inoculates systems to mitigate memory corruption vulnerabilities, which are prevalent in compiled codes and often targeted by attackers.
Discover what software in your system is at risk for attack. Protect your systems with products already used by the US Air Force, the US, Navy, and major primes.
The post Cyber Hardening in the Modern Age: Why Military Systems Need to Keep Up appeared first on RunSafe Security.
]]>The post David Weston Talks Enterprise Software Security appeared first on RunSafe Security.
]]>David Weston Talks Enterprise Software Security
Protecting Against Enterprise Security Attacks
Identify Software Supply Chain Vulnerabilities with RunSafe
Enterprise software security requires an understanding of a full set of security disciplines from cloud security to DevSecOps to software composition analysis and software supply chain.
One person with the best vantage to understand the key trends and topics around enterprise security is David Weston, Vice President of Enterprise Security at Microsoft. David is also a member of the Technical Advisory Committee. TAC’s mission is to provide suggestions based on multidimensional expertise and advise CISA on how to best focus its resources.
Protecting Against Enterprise Security Attacks
In a recent podcast episode hosted by RunSafe Security’s CEO, Joe Saunders, David provides insights into the issues of the day facing enterprises.
During the interview, David discussed some of the greatest security threats that enterprise customers currently face. First of all, there is a significant increase in ransomware, from human-operated to malware to phishing and more. Attackers are also targeting more than one platform, from servers to clients to mobile to infrastructure and beyond. He advised customers to get a holistic view and baseline of security across all attack vectors.
David discussed Microsoft’s focus on upstreaming protection and prevention. In terms of the builder side, Microsoft is working on changing the false security posture of operating system products, which poses a security and engineering challenge because performance and compatibility must remain. On the breaker side, Microsoft is investing in scale and experimenting with safe languages, like RUST and safer constructs of C. He discussed Microsoft’s ‘defense in depth’ mindset, which is pervasive throughout all of their products. This involves validating third-party hardware, designing custom hardware, specialized security in cloud attack surfaces, and bug bounties directed towards Azure.
When discussing the industry changes that have occurred over the course of his career, David shared that earlier on, there was little knowledge on how to convert the intelligence from red or PEN testing into sustained product improvement; and that the current green team is much more developed and mature.
Identify Software Supply Chain Vulnerabilities with RunSafe
At RunSafe Security, we help organizations understand and remediate the risk across their software supply chain, including:
– Generating a software bill of materials (SBOM) so you know exactly what is going into your deployed software
– Identifying vulnerabilities across all the components in your SBOM
– Delivering to developers merge requests in their CI tools so that they can approve security protections just as they would any other software update
– Updating open source packages with protections from the most common and devastating forms of attacks targeting software memory vulnerabilities
Please visit our product page for more details.
The post David Weston Talks Enterprise Software Security appeared first on RunSafe Security.
]]>The post 2023 Cybersecurity Predictions By Sector: Could Your Organization Be Next? appeared first on RunSafe Security.
]]>2023 Cybersecurity Predictions By Sector: Could Your Organization Be Next?
New Year, New Vulnerabilities, Same Common Cyber Attacks
A Growing Need for Pan-Industry Education
Attack Surface Reduction is Possible with RunSafe Security
As 2022 recedes from view, gaps in the cybersecurity industry as a whole have become increasingly apparent. Many organizations weathered attacks from all sides last year, from the Meta employees who internally hacked Facebook user accounts to Google’s blocking of its biggest DDoS attack ever.
Moreover, remote working is here to stay in light of the COVID-19 pandemic. Distributed workforces call for more robust firewalls, routers, access management across remote IT teams and a clearer delineation between personal and professional devices—the former of which are often used in two-step authentication for the latter.
Remote working also points to the industry-level adoption of cloud computing, which has already revolutionized the manufacturing industry. Thanks to smart appliances and the emergence of the Internet of Things (IoT), collecting user data and uploading it to cloud-based systems for analysis has never been easier for manufacturers. However, most smart appliances tout lower-grade processing and storage capabilities, making it harder to implement security measures protecting sensitive user data. Cloud computing also poses security issues on a broader level in the form of supply chain attacks.
However, the challenge of cybersecurity doesn’t stop there. Attackers are getting more creative. Global cyber attacks increased by 38% in 2022, and cost US companies 9.44 million dollars alone.
With the expansion of remote work, new attack formats, and the IoT—in tandem with progressively systematic cyber attackers—a few key sectors demand increased enterprise application security. Staying abreast of these trends—on both the offensive and defensive sides—is paramount for cybersecurity innovation and success in 2023.
New Year, New Vulnerabilities, Same Common Cyber Attacks
Despite the advancements in cybersecurity over the past couple of years, a handful of common cyber attacks pose threats to the IT industry at scale: phishing, DDoS attacks, malware, SQL injection, DNS tunneling, zero-day exploits, and man-in-the-middle (MIM) attacks. As the attack surface expands along with the IoT, new vulnerabilities will likely reveal themselves sooner than later.
Manufacturing Supply Chains Require Extra Attention from DevSecOps
The manufacturing industry, which continually analyzes and implements user data harvested from the IoT, faces a few specific issues of note. Furthermore, an expanding IoT and an increase in cloud computing heighten the risk of system intrusion attacks and the like for manufacturers.
System intrusion attacks aren’t the only cyber attacks manufacturers are especially susceptible to—ransomware, faulty web application code, and good old-fashioned social engineering attacks still pose the most significant cyber threats to the industry.
What makes this all so noteworthy is the ramifications of not taking counteraction, the most glaring one being the mass disruption of operational processes that directly impact supply chains.
Between money extorted by bad actors and decreased revenue resulting from compromised supply chains, the cost of not implementing more robust security measures adds up fast—literally. A real-life illustration of this is the 2021 Kaseya ransomware attack, in which Kaseya’s hijacked VSA remote maintenance tool compromised more than 200 of its companies.
Given these statistics, attack surface reduction and increased ransomware protection will be crucial for manufacturers in the coming year.
Increased Awareness and Reduced Response Time Are Critical for the Financial Sector
Manufacturing isn’t the only industry vulnerable to specific cyber attacks, though. The financial sphere, which is home to some of the most sensitive user data available, is just as vulnerable as manufacturing. Even though specific cyber attacks plague these industries—like phishing, ransomware, and DDoS attacks—the implications for the financial sector are much more significant.
Phishing alone accounted for nearly a quarter of cyber attacks in the financial sector last year, making the case for routine cybersecurity awareness training more vital than ever. From a code standpoint, financial agencies would particularly benefit from robust and timely patch support—more so if crucial points of the process can be automated. Given the number of Internet-facing servers used to scan for threats and ensure network components are all updated in the financial industry, implementing prompt patch support at the DevSecOps level is vital.
Data Breaches Still a Looming Threat in Healthcare
Data breaches remain the biggest concern for IT security decision-makers in the healthcare sector. A BakerHostetler survey discovered that a quarter of data breaches happen in the healthcare sector, where fixing a breach costs organizations $7.13 million on average. Data breaches in healthcare often target patients, too, and specific cyber attacks may prevent them from receiving the timely care they need. This makes the consequences of such attacks much more significant compared to those in other fields.
However, the COVID-19 pandemic presented a new dilemma for IT security decision-makers in healthcare—many of whom decided to temporarily relax company firewall rules in early 2020 to implement expanded telehealth services and a work-from-home (WFH) model for employees. Unsurprisingly, this relaxation has raised a slew of liability and security concerns, putting increased user data protection at the top of the healthcare sector’s list of security priorities.
A Growing Need for Pan-Industry Education
What is most disquieting about all of this, though, is that leaders and decision-makers in cybersecurity remain relatively unprepared to tackle these issues in the manner they require. This is demonstrated in the lack of knowledge and confidence these decision-makers have in successfully combating organization-level cyber threats.
An Eclypsium survey gathered responses from 350 financial IT security decision-makers across the globe, in which a startling 76% responded that they only have a vague understanding of their organizational firmware’s blind spots. Following this, 92% of respondents admitted that cybercriminals are more adept at attacking their firmware’s weak spots than the organizations are at protecting them. This correlates heavily with the 88% who reported an organization-level firmware attack within the past two years.
Clearly, educational gaps in the cybersecurity industry prevent decision-makers from acting shrewdly and decisively. Increased education and awareness, in both scale and frequency, are necessary to maintain best industry practices.
Attack Surface Reduction is Possible with RunSafe Security
As one of the leading software security companies, RunSafe’s product suite offers a host of tools for IT security decision-makers that enable efficient cybersecurity efforts. The lineup of unique, patented products include features that assess your attack surface risk, harden your code, and protect firmware. All software is vulnerable. RunSafe reduces your attack surface and alerts you to existing and future vulnerabilities. See what software your organization uses is at risk for attack today.
The post 2023 Cybersecurity Predictions By Sector: Could Your Organization Be Next? appeared first on RunSafe Security.
]]>

























