The post AI Is Writing the Next Wave of Software Vulnerabilities — Are We “Vibe Coding” Our Way to a Cyber Crisis? appeared first on RunSafe Security.
]]>For decades, cybersecurity relied on shared visibility into common codebases. When a flaw was found in OpenSSL or Log4j, the community could respond: identify, share, patch, and protect.
AI-generated code breaks that model. Instead of re-using an open source component and having to comply with license restrictions, one can use AI to rewrite a near similar version but not use the exact open source version.
I recently attended SINET New York 2025, joining dozens of CISOs and security leaders to discuss how AI is reshaping our threat landscape. One key concern surfaced repeatedly: Are we vibe coding our way to a crisis?
Listen to the Audio Overview
Losing the Commons of Vulnerability Intelligence
At the SINET New York event, Tim Brown, VP Security & CISO at SolarWinds, pointed out that with AI coding, we could lose insights into common third-party libraries.
He’s right. If every team builds bespoke code through AI prompts, including similar to but different than open source components, there’s no longer a shared foundation. Vulnerabilities become one-offs. If we are not using the same components, we won’t have the ability to share vulnerabilities. And that could lead to a situation where you have a vulnerability in your product that somebody else won’t know they have.
The ripple effect is enormous. Without shared components, there’s no community-driven detection, no coordinated patching, and no visibility into risk exposure across the ecosystem. Every organization could be on its own island of unknown code.
AI Multiplies Vulnerabilities
Even more concerning, AI doesn’t “understand” secure coding the way experienced engineers do. It generates code based on probabilities and its training data. A known vulnerability could easily reappear in AI-generated code, alongside any new issues.
Veracode’s 2025 GenAI Code Security Report found that “across all models and all tasks, only 55% of generation tasks result in secure code.” That means that “in 45% of the tasks the model introduces a known security flaw into the code.”
For those of us at RunSafe, where we focus on eliminating memory safety vulnerabilities, that statistic is especially concerning. Memory-handling errors — buffer overflows, use-after-free bugs, and heap corruptions — are among the most dangerous software vulnerabilities in history, behind incidents like Heartbleed, URGENT/11, and the ongoing Volt Typhoon campaign.
Now, the same memory errors could appear in countless unseen ways. AI is multiplying risk one line of insecure code at a time.
Signature Detection Can’t Keep Up
Nick Kotakis, former SVP and Global Head of Third-Party Risk at Northern Trust Corporation, underscored another emerging problem: signature detection can’t keep up with AI’s ability to obfuscate its code.
Traditional signature-based defenses depend on pattern recognition — identifying threats by their known fingerprints. But AI-generated code mutates endlessly. Each new build can behave differently and conceal new attack vectors.
In this environment, reactive defenses like signature detection or rapid patching simply can’t scale. By the time a signature exists, the exploit may already have evolved.
Tackling the Memory Safety Challenge
So how do we protect against vulnerabilities that no one has seen — and may never report?
At RunSafe, we focus on one of the most persistent and damaging categories of software risk: memory safety vulnerabilities. Our goal is to address two of the core challenges introduced by AI-generated code:
- Lack of standardization, as every AI-written component can be unique
- No available patches, as many vulnerabilities may never be disclosed
By embedding runtime exploit prevention directly into applications and devices, RunSafe prevents the exploitation of memory-based vulnerabilities, including those that are unknown or zero days.
That means even before a patch exists, and even before a vulnerability is discovered, RunSafe Protect keeps code secure whether it’s written by humans, AI, or both.
Building AI Code Safely
AI-generated code is here to stay. It has the potential to speed up development, lower costs, and unlock new capabilities that would have taken teams months or years to build manually.
However, when every product’s codebase is unique, traditional defenses — shared vulnerability intelligence, signature detection, and patch cycles — can’t keep up. The diversity that makes AI powerful also makes it unpredictable.
That’s why building secure AI-driven systems requires a new mindset that assumes vulnerabilities will exist and designs in resilience from the start. Whether it’s runtime protection, secure coding practices, or proactive monitoring, security must evolve alongside AI.
At RunSafe, we’re focused on one critical piece of that puzzle, protecting software from memory-based exploits before they can be weaponized. As AI continues to redefine how we write code, it’s our responsibility to redefine how we protect it.
Learn more about Protect, RunSafe’s code protection solution built to defend software at runtime against both known and unknown vulnerabilities long after the last patch is available.
The post AI Is Writing the Next Wave of Software Vulnerabilities — Are We “Vibe Coding” Our Way to a Cyber Crisis? appeared first on RunSafe Security.
]]>The post Is Your Security Helping or Hurting Your Product Line Profitability? appeared first on RunSafe Security.
]]>Security can either be your biggest margin killer or your most powerful profit enabler. From the beginning, our goal at RunSafe has been to put control back into the hands of the defenders. And that means building solutions that meaningfully reduce risk across your product portfolio. As cyber defense champions, we can quantify economic benefits to security solutions that improve your product line profitability.
Listen to the audio overview below:
The Cost of Reactive Security
Security incidents now average $4.88 million per breach according to IBM’s 2024 Cost of a Data Breach Report, but that figure only scratches the surface. The real damage comes from the operational drag that reactive security creates long before any breach occurs.
Consider an example from a software manufacturer, one of RunSafe’s customers. Implementing RunSafe’s runtime code protection saved the company over $1 million per year, with reduced patching representing the largest cost saving.
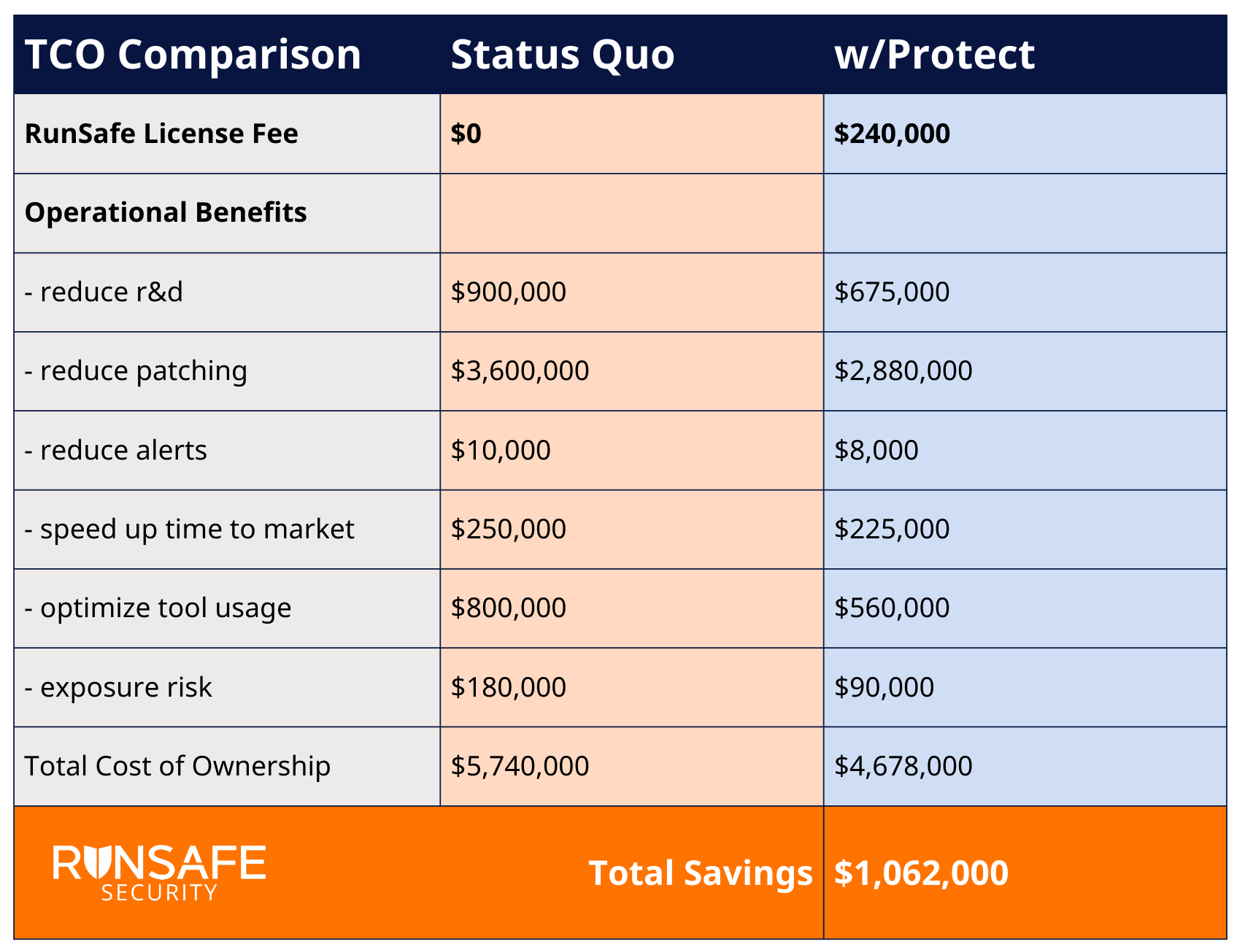
Calculate your potential Total Cost of Ownership here.
Being proactive about security (deploying RunSafe Protect) rather than reactive (relying on patching) saved this company a significant amount of money. And it’s not just money. It’s also about opportunity cost.
The hidden costs of reactive security include:
- R&D Resource Drain: Effort is put into code scanning/review, penetration testing, subsequent remediation, and then coordinated release of patches to customers. These issues spawn lengthy retesting cycles and gobble up R&D resources that would otherwise be able to work on new features and products.
- Market Access Barriers: Companies lose significant contracts when their security posture can’t meet customer requirements. Consider how Zoom was initially excluded from certain DoD environments due to its security posture not meeting baseline requirements.
- Developer Productivity Loss: Engineering teams spend 30-40% of their time on security remediation instead of innovation.
Competitive Disadvantage: Slower release cycles compared to competitors, who ship features faster with built-in security.
Are You Spending to Patch or Investing to Prevent?
The problem with scan-and-patch security is inefficiency and ineffectiveness. For example, in our work on embedded devices, we see on the daily that memory safety vulnerabilities account for 40-70% of identified vulnerabilities in embedded code.
A study by North Carolina State University shows that for Linux operating system software over a 10-year period, only 2.5% of memory vulnerabilities were identified in vulnerability scanning tools. This shows us that scanning, a widely adopted practice, leaves one vulnerable.
Similarly, multiple studies say companies and users generally aren’t patching on time due to a lack of knowledge, the effort to coordinate change, the process slowing progress, fear of breaking the current setup, and other barriers. At its best, patching is reactive. More often, costs and other barriers mean patching is delayed, if done at all.
Even when vulnerabilities are found, patching faces massive barriers:
- Coordination Costs: Cross-team alignment, testing cycles, and deployment logistics
- Customer Resistance: Nobody wants to patch, especially when it might break existing functionality
- Timing Mismatches: Critical vulnerabilities discovered right before major releases
- Risk Accumulation: Delayed patches create growing attack surfaces
The math is brutal. If you’re patching reactively, you’re not just paying for the patch—you’re paying for the disruption, the delays, the testing cycles, and the opportunity costs of having your best engineers chasing down someone else’s vulnerabilities instead of building your next breakthrough feature.
The Runtime Security Advantage
Here’s where the economics flip completely. Runtime security—integrating code protection directly into your development process—transforms security from a margin killer to a competitive advantage.
RunSafe’s approach demonstrates this transformation. RunSafe Protect eliminates an entire class of vulnerability common in embedded software to defend your software from the very beginning and dramatically reduce your attack surface. Protect safeguards your systems during runtime without compromising performance or requiring post-deployment modifications.
The results speak for themselves. RunSafe deployed code protection to dramatically reduce the attack surface by 70% for an industrial automation leader deploying HMI products. The company was able to measurably reduce risk and protect software in very difficult-to-update facilities within critical infrastructure.
Understand the total exposure of your embedded software and quantify your risk reductions with RunSafe Protect. Give your code a scan.
The broader business impact includes:
- Faster Time-to-Market: No more security-driven delays in release cycles
- Predictable Operations: Controlled patch timing instead of emergency responses
- Enhanced Customer Relationships: Fewer disruptions, more reliable products
- Engineering Focus: Teams building features instead of fixing vulnerabilities
- Market Differentiation: Security as a selling point, not a compliance checkbox
Security as a Revenue Driver
Beyond cost savings, the right security approach actually opens new revenue streams. Companies with robust security profiles win contracts that others can’t touch. In RunSafe Security’s 2025 Medical Device Cybersecurity Index, we saw that 83% of healthcare organizations now integrate cybersecurity standards directly into their RFPs and 46% have declined to purchase medical devices due to cybersecurity concerns. A lack of security quickly leads to lost revenue in this competitive market.
On the other hand, it opens the door to increased product line profitability. 79% of healthcare buyers are willing to pay a premium for devices with advanced runtime protection. Similarly in the automotive industry, RunSafe’s 2025 Connected Car Cyber Safety & Security Survey, 87% of survey participants said a car brand that offers strong cybersecurity and privacy would influence their purchase decision, with 35% willing to pay more.
Customers are saying security is worth the cost. That’s good news for product teams looking to make smart investments.
The Bottom Line
Security doesn’t have to be a necessary evil that drains profitability. When implemented early, systematically, and with business impact in mind, security becomes a competitive advantage that drives margin improvement and sustainable growth.
The companies that figure this out first will have operational advantages their competitors can’t match: faster development cycles, lower operational costs, stronger customer relationships, and access to markets that others can’t reach.
Can you afford to keep subsidizing reactive security approaches that are killing your margins and slowing your growth?
See how runtime security can transform your product line profitability. Calculate your potential ROI with RunSafe Protect or schedule a call with our team to discuss your specific business impact.
The post Is Your Security Helping or Hurting Your Product Line Profitability? appeared first on RunSafe Security.
]]>The post Reducing Your Exposure to the Next Zero Day: A New Path Forward appeared first on RunSafe Security.
]]>Our goal at RunSafe is to give defenders a leg up against attackers, so we wondered: What if we could quantify this seemingly unquantifiable risk? What if we could take meaningful action to implement zero-day protection for systems before vulnerabilities are even discovered?
To dig into these questions, we partnered with Ulf Kargén, Assistant Professor at Linköping University, who developed the CReASE (Code Reuse Attack Surface Estimation) tool, which underpins RunSafe’s Risk Reduction Analysis.
Quantifying the Unquantifiable: A New Approach to Zero-Day Risk
VulnCheck, in their “2024 Trends in Vulnerability Exploitation” report, found that 23.6% of all actively exploited vulnerabilities in 2024 were zero-day flaws. We’re seeing nation-state actors like Volt Typhoon and Salt Typhoon specifically target these unknown vulnerabilities to achieve their objectives, as noted in research from Google Threat Intelligence Group, which tracked 75 zero-day vulnerabilities exploited in the wild in 2024.
Most of the industry’s response to zero days has been trying to detect and prevent threats by looking for indicators of attack, suspicious behavior, and patterns that might tip us off. But attackers have gotten really good at hiding and masking their activity. What’s been left wide open is the underlying risks in software itself. Instead of securing the foundation, we’ve built bigger walls around our systems.
That might work in a data center where systems live behind firewalls and racks of gear. But in the world of IoT and embedded devices, there are no walls. These systems are deployed far from the protection of the network where they are alone, exposed, and vulnerable. They need to be self-reliant. They need to be like samurai—able to defend themselves without backup.
Because of this, we saw the need for a method to quantify the risk of zero days and a way to make devices intrinsically more robust against exploitation, regardless of what vulnerabilities might exist within them. If you can quantify risk with real technical rigor, you can make smart decisions to reduce your attack surface and make a compelling argument to leadership on where to focus resources.
Return-Oriented Programming: Understanding the Threat
Modern cyberattacks frequently use a technique called Return-Oriented Programming (ROP). When traditional code injection attacks became difficult due to improved security measures, attackers evolved to use “code reuse” attacks instead.
Modern exploits repurpose a program’s own code, using existing code snippets (called “gadgets”) within a program and chaining them together to create malicious functionality. The program’s own code is weaponized against itself.
This insight gives us a way to measure memory-based zero-day risk specifically. While it’s impossible to predict all potential vulnerabilities in code, we can analyze whether useful ROP chains exist in a binary that could lead to the successful exploitation of a vulnerability.

Quantifying Zero-Day Risk with CReASE
We worked alongside researcher Ulf Kargén at Linköping University who developed the Code Reuse Attack Surface Estimation (CReASE) tool to quantify previously unmeasurable risk. You can listen to Ulf discuss the tool and how it works in this webinar.
CReASE scans binaries to identify potential ROP gadgets and determines whether they could be chained together to perform dangerous system calls. It doesn’t try to predict where specific vulnerabilities might exist but instead analyzes whether the code structure would allow successful exploitation if a vulnerability were discovered.
It answers the question: Are any useful ROP chains available to an attacker?
Unlike existing tools that focus on guaranteeing working exploit chains (often sacrificing scalability or completeness), CReASE uses novel data flow analysis to achieve both scalability and completeness comparable to a human attacker.
The result is a risk scoring system that quantifies the probability that the next memory-based zero-day vulnerability could be exploited to achieve specific dangerous outcomes like remote code execution, file system manipulation, or privilege escalation.
The CReASE tool underlies RunSafe’s Risk Reduction Analysis, which you can use to analyze your exposure to CVEs and memory-based zero days.
The Memory Safety Challenge
To understand why this approach is so powerful, we need to recognize two critical facts:
- 70% of vulnerabilities in compiled code are memory safety vulnerabilities
- 75% of vulnerabilities used in zero-day exploits are also memory safety vulnerabilities
These numbers tell us that memory safety vulnerabilities constitute a significant risk in our codebases. When a memory vulnerability is exploited, attackers can execute arbitrary code, take control of devices, crash systems, exfiltrate data, or deploy ransomware.
By focusing our risk quantification and mitigation efforts on memory-based vulnerabilities specifically, we’re addressing a common and dangerous attack vector for zero-day exploits.
Memory Randomization: Making Zero-Day Vulnerabilities Inert
Once we quantify the risk, what can be done about it? Traditional memory protection like Address Space Layout Randomization (ASLR) provides some security by randomizing where blocks of code are loaded in memory. However, ASLR still loads functions contiguously, making it vulnerable to information leak attacks.
RunSafe’s approach takes randomization to the function level. Instead of randomizing where the entire binary loads, we randomize each function independently. In a typical binary with 280 functions, this creates 280 factorial possible memory layouts — more than 10^400 combinations.
Even if a memory-based zero-day vulnerability exists, with RunSafe’s Load-time Function Randomization (LFR), attackers can’t reliably construct a working ROP chain because they can’t predict where the necessary gadgets will be located. We’ve effectively made the vulnerability inert.
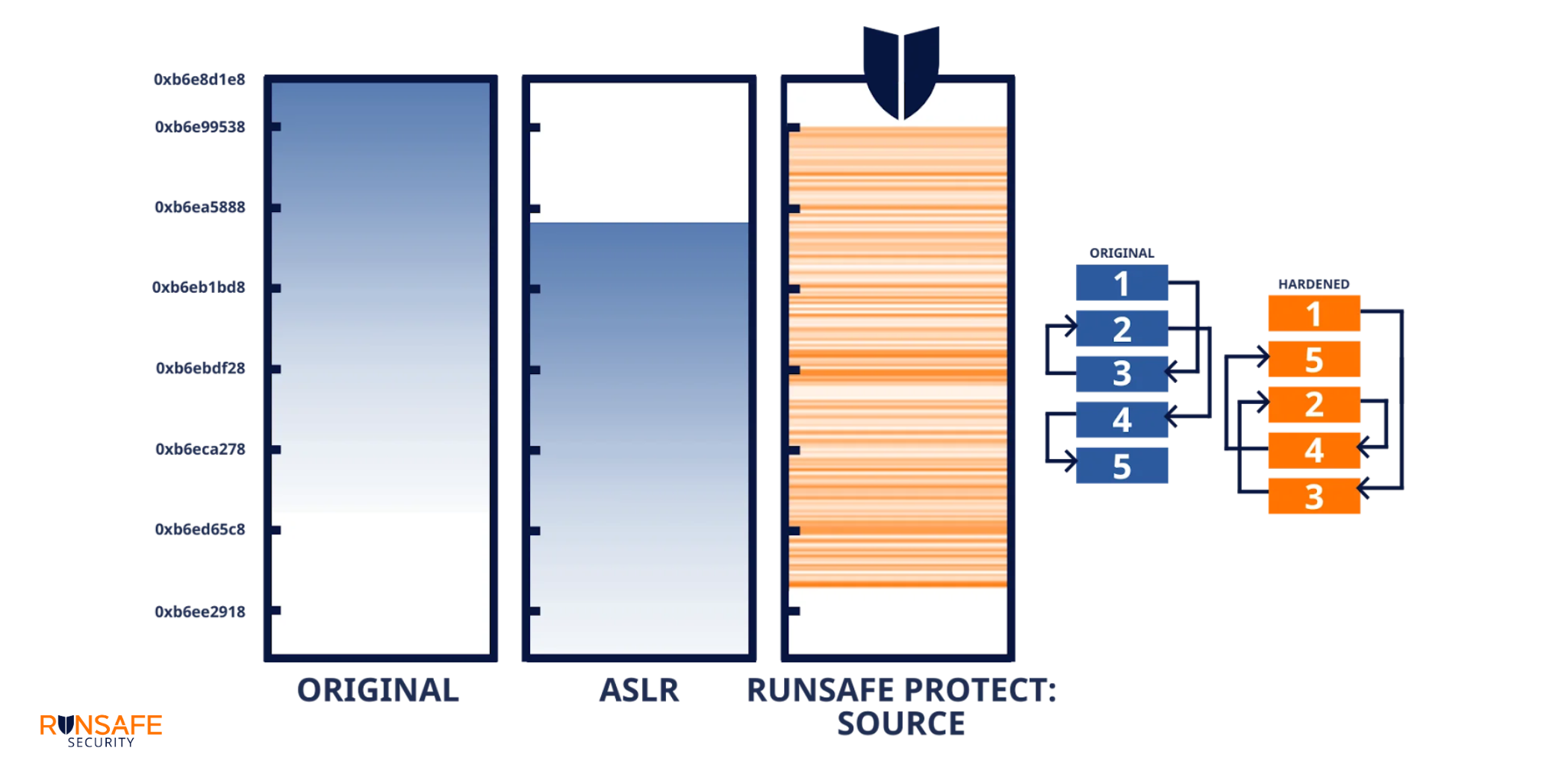
Taking Action: Zero-Day Vulnerability Protection
The most effective approach to memory-based zero-day risk combines analysis and protection:
- Analyze your binaries to understand your current risk profile
- Apply function-level randomization to neutralize potential exploits
- Measure the risk reduction to quantify your improved security posture
Our customers typically see a risk reduction that changes the odds from “the next zero-day can compromise the system” to “maybe one in the next 10,000 zero-days might succeed.” That’s a dramatic improvement in security posture.
While no solution can eliminate all types of zero-day vulnerabilities, addressing memory-based vulnerabilities targets the most common and dangerous attack vector. In a world where zero-days will always exist, making them ineffective is the next best thing to eliminating them entirely.
Want to try out the Risk Reduction Analysis tool for yourself? All you’ll need to do is create an account and upload a binary to get your results.
Run an analysis here.
The post Reducing Your Exposure to the Next Zero Day: A New Path Forward appeared first on RunSafe Security.
]]>The post Zero-Day Vulnerabilities: Exploitation Trends and Lessons Learned appeared first on RunSafe Security.
]]>In 2024 alone, security researchers at Google tracked 75 zero-day vulnerabilities exploited in the wild. Particularly alarming is that 44% of these targeted enterprise products, highlighting how attractive zero-day vulnerabilities are to cybercriminals and nation-state threat actors. For example, we’ve seen how Volt Typhoon and Salt Typhoon have specifically targeted operational technology (OT) systems through unpatched vulnerabilities.
Whether we’re considering weapons systems, critical service providers, security vendors, or others, nation-states and other malicious actors have their eyes on zero-day flaws as a means to cause widespread damage and disruption.
What Are Zero-Day Vulnerabilities and Why Are They Exploited?
A zero-day vulnerability is a flaw in software that is unknown to the software’s developers or vendors. Because no patch exists to correct the flaw, attackers can exploit it to gain unauthorized access to systems, disrupt operations, or steal sensitive data. Zero-day attacks are especially dangerous because they target unsuspecting systems, leaving defenders without sufficient time to react until after the vulnerability is discovered and addressed.
Attackers exploit zero-day vulnerabilities for several reasons:
- Access to critical systems: Whether targeting enterprise networks or OT environments, attackers can exploit zero-day vulnerabilities to bypass security controls and gain unauthorized entry.
- Widespread impact: Exploiting a zero day in commonly used software or widely deployed systems can lead to mass compromise.
- Advantage in intelligence gathering: Nation-state threat actors frequently use zero days to extract sensitive intelligence, setting the stage for future attacks.
- Disruption: Threat actors utilize zero-day exploits as a weapon to disrupt operations, with the potential for significant financial and operational repercussions.
Recent Trends in Zero-Day Exploitation
The growing risk of zero-day vulnerabilities stems from several key factors, like the rise in interconnected devices and the wider use of open-source software. Here are some important trends to keep in mind.
1. Enterprise Software in the Crosshairs
Of the 75 zero days exploited in 2024, 44% targeted enterprise systems. Specific cases include:
- Ivanti VPN Zero Days: Ivanti’s Connect Secure VPN devices became a notable target for attackers, with seven zero days discovered, including CVE-2025-0282, which allowed remote code execution. Attackers used these vulnerabilities to inject malware into corporate networks.
- Palo Alto Networks PAN-OS: A command-injection exploit allowed attackers to bypass security controls in enterprise firewalls, exposing sensitive environments to intrusions.
Such examples underscore the need for enterprises, as high-value targets, to proactively address vulnerabilities across their technology stacks.
2. Supply Chain Attacks: The Multiplier Effect
Attackers increasingly target software supply chains, exploiting vulnerabilities at the development stage. For instance:
- MOVEit Transfer and Jenkins Vulnerabilities: A critical path traversal flaw (CVE-2024-23897) within Jenkins could result in arbitrary code execution. If exploited, attackers gain opportunities to insert malware into countless downstream applications.
Supply chains present an ideal target because a single vulnerability in shared components can impact thousands of users across industries.
3. Embedded Software Under Fire
Embedded systems used in everything from medical devices to automotive software share a unique risk in terms of zero-day vulnerabilities due to their reliance on C/C++ code. Research shows that 70% of vulnerabilities in compiled code are memory safety issues, such as buffer overflows and use-after-free errors. Attackers favor these flaws because they are difficult to detect and can cause major disruptions.
Key embedded-system sectors targeted include:
-
- Industrial Control Systems (ICS) and Operational Technology: Attackers compromise OT environments in critical infrastructure, potentially causing large-scale service disruptions.
- Automotive Software: Vulnerabilities found in connected vehicles could allow attackers to take control of core functions or extract user data.
- Medical Devices: Unauthorized access to medical device software can compromise patient treatment and safety.
Ways to Defend Against Zero-Day Vulnerabilities
While it’s impossible to eliminate all vulnerabilities, organizations can take proactive steps to reduce their exposure to zero-day exploits. Below are actionable recommendations for enterprises and developers:
1. Adopt a Zero Trust Architecture
Zero trust assumes no implicit trust between systems. By applying strict access controls and continuously verifying users and devices, enterprises can minimize the impact of zero-day breaches.
2. Perform Dynamic and Static Analysis
Dynamic application security testing (DAST) and static application security testing (SAST) tools can identify vulnerabilities before they’re exploited. Automated testing provides invaluable insights into weak spots.
3. Deploy Runtime Protections
Solutions like runtime exploit prevention can defend applications against zero-day exploitation in live environments. For embedded systems, tools like RunSafe Protect are ideal for neutralizing memory safety vulnerabilities, providing real-time defense against exploits.
4. Strengthen Vulnerability Management Programs
A thorough vulnerability management program helps organizations prioritize high-risk systems, improve patch timelines, and reduce attack surfaces. An important starting point is to generate comprehensive SBOMs that provide visibility into software components.
5. Assess Total Zero-Day Exposure
The Google report found that use-after-free errors, command injection, and cross-site scripting (XSS) were the most frequently exploited vulnerability types. Deploying secure coding practices is one way to address these issues and minimize the number of zero-day vulnerabilities in code.
In the case of memory safety vulnerabilities, understanding potential zero-day exposure through tools like RunSafe’s Risk Reduction Analysis gives organizations unprecedented visibility into their vulnerability landscape. By analyzing return-oriented programming (ROP) chains, the analysis quantifies memory-based zero days and how much organizations can reduce risk when implementing targeted protections where they matter most.
Lessons Learned from Recent Zero-Day Incidents
The continued use of zero days by nation-state actors underscores the importance of adopting a proactive approach to security. Lessons include:
-
-
- Memory safety matters: With many recent exploits stemming from memory flaws, securing codebases in languages like C/C++ is paramount. Runtime protections defend new and legacy code to prevent attackers from taking advantage of these flaws.
- Supply chain hygiene is critical: Minimizing risk in software supply chains requires vetting third-party code carefully and implementing Software Bills of Materials (SBOMs) to identify and address potential weaknesses.
- No one is immune: Enterprises, operational technology vendors, and critical service providers alike must address their unique attack surfaces to avoid becoming the next victim of a zero-day exploit.
-
Gaining the Upper Hand Against Zero-Day Attacks
Nation-state actors and sophisticated criminal groups continue to leverage zero-day vulnerabilities because they consistently deliver results. The Ivanti exploits and other critical vulnerabilities throughout 2024 reinforce the need for secure coding practices and security solutions that take away attackers’ ability to exploit software flaws.
Visibility is also an important way to level the playing field. We know that memory safety flaws remain a predominant source of zero-day exploits. Tools like RunSafe’s Risk Reduction Analysis give organizations the ability to quantify their exposure to CVEs and memory-based zero days.
By analyzing an SBOM or binary, the tool gives organizations visibility into weak spots in their software and the ability to apply remediations before attackers exploit them, transforming their security posture from reactive to proactive. When it comes to zero-day vulnerabilities, knowledge isn’t just power. It’s protection.
The post Zero-Day Vulnerabilities: Exploitation Trends and Lessons Learned appeared first on RunSafe Security.
]]>The post Rethinking Open Source Vulnerability Management: 5 Strategies to Build Resilience in Embedded Systems appeared first on RunSafe Security.
]]>RunSafe Security and Lynx are partners in securing embedded software platforms.
For too long, open source vulnerability management has been treated as a reactive game of whack-a-mole: identify vulnerabilities, patch them, and repeat. This approach often leaves teams overwhelmed and constantly playing catch-up.
What if we flipped the script? Vulnerabilities aren’t just problems—they’re signals. They reveal weaknesses, highlight opportunities, and guide better decisions. By treating vulnerabilities as feedback rather than failures, you can rethink how embedded systems in industries like aerospace, automotive, industrial automation, and medical devices are designed and secured.
In this article, we explore five transformative strategies for addressing open source vulnerabilities that go beyond traditional practices, helping you move from firefighting to future-proofing your systems.
1. Redefine Your Relationship with Vulnerabilities
Most teams view vulnerabilities as failures, reacting only when an issue is discovered. But vulnerabilities are more than just bugs—they’re data points. When properly analyzed, they offer insight into design choices, team processes, and system architecture, providing an opportunity for improvement.
How to Leverage Vulnerabilities as Feedback
- Refine your software architecture: Use your SBOM (Software Bill of Materials) as a diagnostic tool. Are recurring vulnerabilities tied to a particular library or dependency? Consider switching to better-maintained or less vulnerable alternatives.
- Understand system dynamics: Track patterns across projects and teams to identify development blind spots.
Real-World Application:
Imagine an automotive team that regularly identified vulnerabilities in a third-party diagnostic library. By switching to an open-source alternative with a more active community, they reduced vulnerabilities by 40% and enhanced system reliability.
This proactive approach fosters confidence in your processes, ensuring continuous improvement.
What is an SBOM (Software Bill of Materials)? SBOMs are a list of all components in a software build, including libraries and dependencies, which helps teams identify and track vulnerabilities systematically.
Understanding the full scope of an SBOM enables more informed decisions about system modifications and vulnerability management strategies, leading to more secure software architectures.
2. Embed Resilience Instead of Chasing Compliance
Compliance frameworks like DO-326A (aerospace cybersecurity), ISO/SAE 21434 (automotive cybersecurity), and NIST Cybersecurity Framework provide a baseline for secure systems. But achieving compliance shouldn’t be the end goal—it’s the beginning. Resilience is about building systems that remain secure even as threats evolve, ensuring compliance is naturally met as a byproduct.
How to Build Resilience That Meets Compliance
- Design with failure scenarios in mind: Use threat modeling to identify potential attack vectors early during development.
- Automate compliance reporting: Tools like Lynx Vigiles simplify audit preparation, allowing teams to focus more on security instead of documentation.
Pro Tip:
Treat compliance as a checkpoint, not a destination. Teams that embed cybersecurity into their workflows achieve compliance faster and with fewer reworks.
Threat modeling: Identifying potential security threats to the system and developing countermeasures to prevent or mitigate these threats.
3. Focus on Vulnerability Paths, Not Just Individual Flaws
Attackers don’t exploit single vulnerabilities in isolation; they look for exploit paths—chains of vulnerabilities that can lead to system failure. Addressing how open source vulnerabilities interact within your system can stop attacks before they start.
How to Identify and Break Exploit Paths
- Map dependencies: Visualize how different components interact and assess how vulnerabilities in one might expose others.
- Prioritize by context: What may be a low-severity issue in an industrial control system could be critical if it enables lateral movement to safety-critical functions.
Example:
In an industrial automation system, a minor flaw in a third-party networking library allowed attackers to bypass authentication. Fixing this vulnerability preemptively protected safety-critical systems. While the flaw might not have drawn much attention in isolation, its potential impact within a chain of vulnerabilities highlighted its true risk.
Power Move:
Integrate RunSafe Security’s memory address randomization to protect against memory-based attacks, common in exploit paths. This technique, applied during the software compilation process, randomizes the layout of memory addresses within a program. By making the memory structure unpredictable, it significantly impedes attackers’ ability to craft exploits that rely on known memory locations, thereby neutralizing a substantial portion of memory corruption vulnerabilities.
Mapping dependencies and breaking exploit paths: This strategy involves visualizing the interconnections between software components to identify and disrupt sequences of vulnerabilities that could be chained together by an attacker, thereby preventing a single weakness from compromising the entire system.
4. Shift Vulnerability Ownership Across the Organization
Vulnerability management is often confined within security or DevSecOps teams. However, for a system to be secure, everyone—developers, product managers, and leadership—must share responsibility. Security is a business-critical priority, not just a technical concern.
How to Foster Organizational Ownership
- Set team-level goals: Include vulnerability remediation and time-to-resolution as part of team OKRs and KPIs.
- Invest in security training: Equip all team members with the knowledge to identify and mitigate vulnerabilities early. Think of it as the equivalent of educating your team not to plug in random USB sticks found in the wild, except for open source vulnerabilities.
Pro Tip:
Make vulnerability metrics visible across the organization to encourage collaboration. Teams that understand their impact on overall security are more motivated to act. This shared responsibility leads to a quicker resolution of vulnerabilities, reducing the window of exposure and enhancing overall system security.
5. Use Automation to Do the Heavy Lifting, but Keep Humans in the Loop
Automation is essential for managing the sheer volume of vulnerabilities in modern embedded systems. But tools alone aren’t enough. Strategic oversight ensures that fixes align with business goals, technical feasibility, and long-term resilience.
How to Combine Automation with Expertise
- Automate triage: Use tools like Vigiles to filter out non-applicable vulnerabilities, focusing your team on critical issues.
- Enable smarter decisions: Human judgment is critical for balancing security with operational needs, especially in safety-critical industries.
Example:
An aerospace company used automated scanning with basic filters and faced over 1,000 vulnerabilities. Enhancing these filters with additional context and capabilities, such as with Vigiles, they saw half automatically marked as non-applicable. This effective triage cut their potential workload in half and allowed them to thoroughly assess high and critical severity vulnerabilities impacting system safety, saving weeks of manual effort and unnecessary remediation.
Including RunSafe Security’s runtime memory protection during the compilation process drastically lowers the risks associated with common memory vulnerabilities, allowing security teams to focus on more complex threats.
These approaches not only optimize resource allocation but also enhance the accuracy and relevance of vulnerability management efforts, leading to a more resilient system.
The Cost of Inaction: Addressing Open Source Vulnerabilities
Neglecting to adopt proactive strategies for open source vulnerability management comes at a high cost:
- Missed deadlines: Vulnerabilities discovered late disrupt production schedules.
- Compliance failures: Inadequate processes expose teams to regulatory penalties.
- System compromises: Unchecked exploit paths can lead to catastrophic consequences.
Every delay in addressing vulnerabilities isn’t just a technical risk—it’s a threat to your mission, your reputation, and your bottom line.
Conclusion: Security as a System
Rethinking open-source vulnerability management is about more than fixing issues—it’s about designing systems that are secure by default. By redefining your relationship with vulnerabilities, embedding resilience, focusing on exploit paths, fostering organizational ownership, and leveraging automation, you can move from firefighting to future-proofing your embedded systems.
Take the next step today:
- Don’t wait for open source vulnerabilities to disrupt your operations. Cut through the noise with Lynx Vigiles and focus on the vulnerabilities that matter most.
- Discover RunSafe Security’s runtime protection to neutralize vulnerabilities before attackers can take root.
The post Rethinking Open Source Vulnerability Management: 5 Strategies to Build Resilience in Embedded Systems appeared first on RunSafe Security.
]]>The post Smooth Out Your Patch Management: How to Reduce Vulnerability Severity appeared first on RunSafe Security.
]]>Despite these challenges, applying patches quickly remains an industry-best practice for keeping software and embedded devices secure. However, relying solely on scanning and patching is proving inadequate for modern security needs. The challenge now for software manufacturers is finding ways to improve the patching process to proactively and strategically defend embedded systems.
This blog will explore:
- When organizations should prioritize patching
- How reachability analysis is evolving but remains limited
- The role of runtime protection solutions in reducing vulnerability severity
- The tangible benefits of runtime security for developers and software manufacturers
When Should You Apply a Patch?
Severity remains a top qualifier when deciding which vulnerabilities to patch. Most organizations focus on critical and high vulnerabilities first, moving on to medium and low severities only when practical. For publicly released software, external-facing systems take precedence, but it’s important to remember that internal tools with access to sensitive data or proprietary information shouldn’t be ignored either.
For example:
- Critical vulnerabilities affecting widespread functionality or enabling remote code execution often warrant immediate action.
- Medium or low vulnerabilities might be deprioritized but can still pose risks depending on their reachability or the systems they impact.
Reachability Analysis as a Future Tool
One potential solution to this prioritization problem is reachability analysis, which assesses whether a specific vulnerability is exploitable in a given system. While some tools already provide reachability analysis for languages like JavaScript and Python, their accuracy and adoption remain inconsistent. Unfortunately, such solutions are not yet widely available for languages like C and C++, which underpin many embedded and legacy systems.
This is where runtime security solutions come into play.
Reducing Vulnerability Severity with Runtime Security Solutions
Runtime security solutions provide an innovative approach to mitigating vulnerabilities without waiting for patch cycles. By securing software in real-time, these tools reduce the operational urgency to patch, buying teams valuable time while still maintaining protection against exploits.
A key benefit of runtime solutions is it allows organizations to reduce the severity score of common vulnerabilities found across embedded software. For example, a significant number of embedded systems are written in memory-unsafe languages such as C and C++. These systems are uniquely vulnerable to memory-based vulnerabilities, including buffer overflows and use-after-free errors. Alarmingly, 70% of zero-day exploits stem from memory corruption vulnerabilities, leading to severe repercussions like remote code execution.
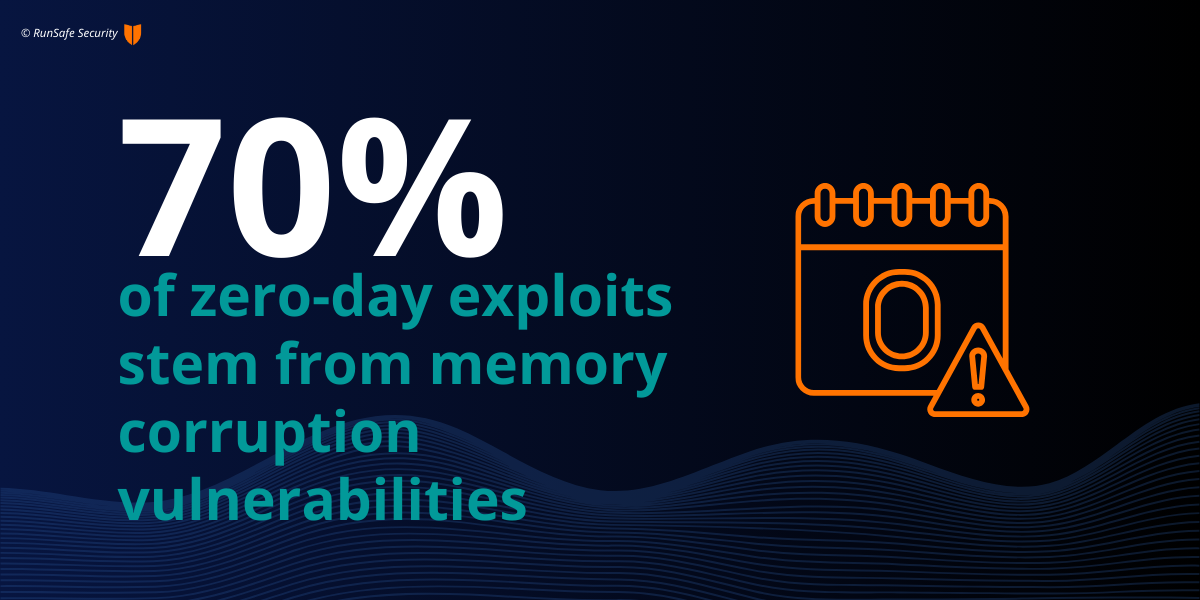
By eliminating memory-based vulnerability exploitability, runtime solutions offer immediate security benefits to embedded systems, including the ability to lower vulnerability severity and reduce the need to patch.
How RunSafe Protect Reduces Vulnerability Severity
Solutions like RunSafe Protect directly mitigate memory-based vulnerabilities at runtime. By doing so, developers can reduce the severity of vulnerabilities based on their Common Vulnerability Scoring System (CVSS) rating. For instance:
- Using the CVSS v4.0 calculator, developers can adjust parameters such as availability and integrity to “none” for memory-based CVEs mitigated by RunSafe Protect.
- This adjustment effectively reduces the CVSS score to zero, making the vulnerability non-exploitable.
Critically, this mitigation doesn’t replace patching—it complements it. Teams should continue to scan for vulnerabilities, adjust severity scores based on runtime mitigations, and follow existing risk management guidelines. However, runtime security minimizes the urgency associated with patching, ensuring systems remain defended while developers work on longer-term fixes.
The Broader Benefits of Runtime Security Solutions
Implementing runtime security doesn’t just enhance protection—it also delivers measurable benefits to both development teams and overall organizational efficiency. Here’s how:
Improved Operations and Smoother Patch Schedules
With runtime protections in place, patching schedules can be aligned with planned updates, reducing the need for emergency patches that disrupt workflows. Developers gain more time to properly develop, test, and deploy patches without compromising security.
Saving Developer Resources
Patching is a time-intensive process. By ensuring vulnerabilities are mitigated at runtime, runtime solutions free up developers to focus on their core tasks—writing new code and shipping innovative products. This operational efficiency directly enhances the organization’s productivity.
Enhanced Customer and Stakeholder Confidence
When vulnerabilities are mitigated at runtime, organizations can issue security advisories that reassure customers and partners. The ability to state that systems are already protected thanks to runtime protections strengthens confidence in your processes and builds trust with stakeholders.
Economic Advantages
The financial benefits are clear:
- Lower risk of costly breaches or operational downtime
- Smoother allocation of development and security resources
- Greater ability to prioritize business growth over firefighting vulnerabilities
By reducing workload, mitigating risk, and streamlining operations, runtime security ensures organizations achieve both technical and business goals.
Practical Steps for Smooth Patch Management
Runtime security solutions like RunSafe Protect offer organizations breathing room. But patching remains an essential element of your cybersecurity strategy. Here are recommended next steps for improving your patch management workflow:
- Adopt a Comprehensive Vulnerability Management Plan: Use tools that perform regular scans, prioritize vulnerabilities by severity, and integrate runtime protections to reduce urgent patches.
- Leverage Runtime Security Solutions: Introduce tools that can instantly mitigate known vulnerability types, especially memory-based vulnerabilities common in critical systems.
- Invest in Reachability Analysis Tools: When available, these tools can help you focus patching efforts on the most exploitable vulnerabilities.
- Regularly Align Security Updates with Operational Schedules: Plan patches during downtime or alongside regular updates to minimize disruption.
By adopting a layered approach to vulnerability management, organizations can keep systems secure without overburdening teams or disrupting day-to-day operations.
Take Control of Your Patch Management Strategy
Patching may remain one of the most difficult tasks in embedded systems, but it doesn’t have to drain resources or derail business priorities. By supplementing traditional scanning and patching processes with runtime security solutions, organizations can reduce vulnerability severity, protect critical systems, and empower development teams to focus on the future. Want to simplify vulnerability identification and automate mitigations?
Explore how the RunSafe Security Platform can reduce the severity of memory-based vulnerabilities and smooth out your patching process.
The post Smooth Out Your Patch Management: How to Reduce Vulnerability Severity appeared first on RunSafe Security.
]]>The post Cybersecurity Trends to Prepare for in 2022 appeared first on RunSafe Security.
]]>Recap of Cybersecurity and Cyber Attacks in 2021
Recap of Cybersecurity and Cyber Attacks in 2021
Dare I say that the past year has been…drumroll…unprecedented…in the realm of cybersecurity and cyber attacks?
Here are some statistics to showcase what the industry has endured over the past 12 months:
- With the trends over the previous year, ransomware costs are expected to reach $265 Billion by 2031, with a new attack happening every 2 seconds.
- The first half of 2021 amounted to $416 million in ransomware costs, which is more than the entirety of 2020.
- An alarming 97% of businesses have been impacted by a cybersecurity breach in their supply chain this year, and 93% admitted that they have suffered a direct breach because of weaknesses in their supply chain.
- This year, IoT devices suffered an average of 5,200 cyber attacks each month.
- In general, cybercrime is up 600% as a result of the COVID-19 pandemic, representing the greatest transfer of economic wealth in history.
- According to IBM, it currently takes a company 197 days to discover a cybersecurity breach and up to 69 days to contain it.
- Companies that were able to contain a breach in less than 30 days saved more than $1 million compared to those that took more than 30 days.
To supplement our year-in-review, it’s also important to make note of the most impactful cyber attacks experienced to properly pivot our efforts in making improvements for a safer 2022.
The Top 5 Cyber Attacks of 2021
1. CNA Financial
One of the largest insurance companies in the U.S., CNA Financial Corporation, was forced into paying $40 million in March to regain control of its network after a ransomware attack. The cyber criminals used malware called Phoenix Locker, a variant of ransomware called ‘Hades’, originally created by a Russian cybercrime syndicate known as Evil Corp.
2. Colonial Pipeline
Colonial Pipeline had to pay a $5 million ransom after Russian-based bad actors from a group called “DarkSide” breached their IT network, essentially halting fuel deliveries up and down the East Coast.
3. JBS USA
JBS USA, the globe’s largest meat processing corporation, paid nearly $11 million in bitcoin after suffering a cyber attack that hacked their network, shutting down operations in Australia, Canada, and the U.S.
4. Kaseya
Kaseya fell victim to a cyber attack in early July, facing hackers that took advantage of a vulnerability in their software against multiple managed service providers (MSPs) and their customers. It was estimated that nearly 1500 small to medium-sized companies experienced this compromise through their MSP.
5. Brenntag
In April, German chemical distribution company Brenntag suffered the effects of another DarkSide ransomware attack, targeting its North America division and resulting in 150GB of stolen and irretrievable data.
Onward and Upward: What We Can Do Better in 2022
Here’s what our team of cybersecurity experts is predicting to be the top trends in the cybersecurity landscape for next year as we reflect on these past events around the industry.
Security Monitoring
Many cyber attacks over the past 12 months occurred with too long of a time for the breaches to be contained or even identified, leading to an extended service disruption for customers. Reputations, bottom lines, and resources are negatively impacted with each minute that a breach goes undetected.
In 2022, it’s finally time to beat the bad actors to the punch. With software security and vulnerability monitoring, you can get ahead of vulnerabilities that can leave doors wide open for cyber criminals to take advantage of. Software scanning technologies are allowing software to pass tests while 50% of vulnerabilities and weaknesses in code are still present. This ratio should be left behind when the ball drops on New Year’s Eve.
The solution? A way of reliably and accurately monitoring the health and stability of systems while they’re running so that you can flag failures or potential attacks before disruption of service occurs.
RunSafe Security has developed a technology that indicates instability and unreliability that most technologies in 2021 have missed. Alkemist:Flare delivers a bright, real-time indicator of application failures related to cyber attacks and software weaknesses.
Immediately get insight into the events that are causing system reliability issues, performance degradation, service availability risk, and attack vectors that lead to disruption in service. This gives you the opportunity to fix code weaknesses, report vulnerabilities to software vendors, build additional layers of protection, and share telemetry data to security operations for automated responses or detailed research before today’s most talented attackers get the upper hand.
It will be more than essential to ring in the new year with reliable monitoring technologies implemented.
Embedded Device Security
The Internet of Things (IoT) is made up of billions of connected devices, with that number only growing as we move into 2022. 70% of these devices currently contain vulnerabilities. What does this mean for the world’s cyber criminals? An enticing, growing attack surface to infiltrate. DDoS, buffer overflow, memory corruption, and zero-day attacks are just around the corner for critical industrial, commercial, medical, military, and consumer targets alike.
But not with a New Year’s resolution that includes a method of built-in security equipped to significantly reduce this IoT attack surface. RunSafe Security enables complete software immunization for embedded devices, without having to affect source code. For new devices, Alkemist:Code technology can be embedded directly into the build process with native Yocto and RTOS implementations, securing mission-critical components.
Open Source Software Security
Using open source software in today’s world is certainly not uncommon, as it has become an integral part of any software development effort. But there’s a major problem: Even with as long as open source software stacks have been around, many vulnerabilities still exist as we step into 2022, leading many to believe that it’s inherently insecure.
It’s past time to effectively mitigate these risks. Organizations can now fix insecure code directly, while also leaving developer friction and performance degradation in the dust.
Alkemist:Repo, a pre-hardened software file that seamlessly replaces the original open source repo, can be deployed within open source software with security built-in to keep your software secure. The images are functionally identical, but logically unique, requiring no user rework or additional configuration changes outside of changing a file pointer.
Cloud Workload Security
It’s likely no surprise to you that the growth of cloud computing, workloads, and infrastructure only continued to grow over the past year, expanding the levels of complexity in both the number of players and the services they offer. It’s become even more difficult to maintain visibility and control over multiple workloads within a single enterprise. Old-school approaches of scanning and patching on post-deployment timelines are putting an unmanageable amount of pressure on security teams.
RunSafe’s Alkemist technology adds a layer of protection within cloud workload code that proactively protects against both known and unknown vulnerabilities, giving enterprises the ability to experience the full potential of using the cloud—agility, flexibility, and the opportunity to devote more resources to a new product or feature development.
A Final Reflection
2021 was indisputably a whirlwind in the realm of cybersecurity. When this time comes around next year, I’d expect the discussion to be largely focused on how we did to improve security monitoring, as well as security for embedded devices, open source software, and cloud workloads—the trends to be on the lookout for as 2022 approaches.
Start next year with the right foot forward and get a free trial of RunSafe’s Alkemist technology today. It’s easy!
FAQs:
What were the top 5 attacks of 2021?
– CNA Financial
– Colonial Pipeline
– JBS USA
– Kaseya
– Brenntag
What should companies be doing better to secure 2022?
– Security Monitoring
– Embedded Device Security
– Open Source Software Security
– Cloud Workload Security
How can you prepare for security threats in 2022?
RunSafe Security has developed a technology that indicates instability and unreliability that most technologies in 2021 have missed. Alkemist:Flare delivers a bright, real-time indicator of application failures related to cyber attacks and software weaknesses.
Immediately get insight into the events that are causing system reliability issues, performance degradation, service availability risk, and attack vectors that lead to disruption in service. This gives you the opportunity to fix code weaknesses, report vulnerabilities to software vendors, build additional layers of protection, and share telemetry data to security operations for automated responses or detailed research before today’s most talented attackers get the upper hand.
The post Cybersecurity Trends to Prepare for in 2022 appeared first on RunSafe Security.
]]>The post Security Scanning for Software Vulnerabilities appeared first on RunSafe Security.
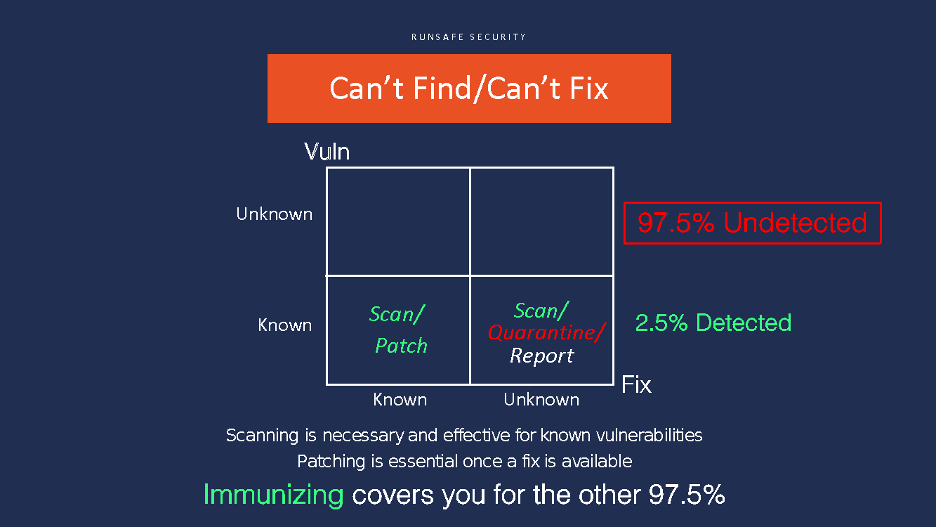
]]>Recent research by RunSafe Security partners show that current strategies of scanning for and patching vulnerabilities in software leave a huge and highly-exploitable security gap. When measured against NIST CVEs (Common Vulnerability Enumerations from the National Vulnerability Database), the researchers found that:
- Memory vulnerabilities are the most frequent CVEs reported in the database, making up 40% of the total, and are ranked as the #1 software weakness in MITRE’s current CVE rankings
- 59% of these memory CVEs have exploits available
- They produce the highest CVSS consequence scores, in the 7.2 to 9.8 out of 10.0 (the High and Critical ranges), in NIST’s Common Vulnerability Scoring System. In layman’s terms these are the vulnerabilities that, if exploited, can cause the most damage to an organization.
- Only 2.5% (15 of 592) of all Linux CVEs are currently detected by scanning tools, leaving a massive 97.5% security gap.
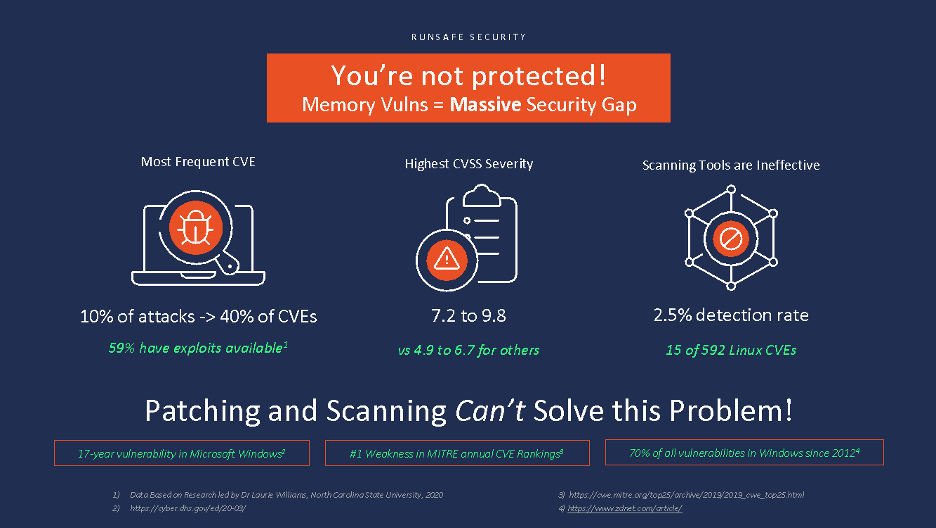
Does this mean scanning and patching are no longer relevant? Obviously they are – they are essential foundation elements for effective cyber security and hygiene.
What it does mean is that other solutions are required to fill the gap, to mitigate vulnerabilities before they are detected, reported, or patched. RunSafe calls this category “software immunization,” by which code can be inoculated against vulnerabilities before deployment. We believe this “third leg of the stool” is an essential new approach that can increase software security by a full order of magnitude, and in many specific use cases completely eliminate the most dangerous weakness in software today, memory-based vulnerabilities.
Complement Existing Security Scanning Tools
According to Thomas Scanlon at Carnegie Mellon’s Software Engineering Institute, “84% of software breaches exploit vulnerabilities at the application layer” (https://insights.sei.cmu.edu/sei_blog/2018/07/10-types-of-application-security-testing-tools-when-and-how-to-use-them.html). This has driven an entire domain of application security testing tools and techniques. Identification and remediation of these vulnerabilities has become extremely valuable in the marketplace – the vulnerability scanning software company Snyk raised a $200M round of venture capital in September 2020 that values that company at $2.6B (https://techcrunch.com/2020/09/09/snyk-bags-another-200m-at-2-6b-valuation-9-months-after-last-raise/).
In its definition from CSO magazine, “vulnerability scanning is an automated activity that relies on a database of known vulnerabilities such as CVE/NVD – scanning vendors [such as Snyk, Qualys, Rapid7, and Tenable] maintain more complete databases…”(https://csoonline.com, “What are vulnerability scanners and how do they work?,” Lucian Constantin, April 10, 2020). Despite intense investment in this space, however, the research showed that scanning tools only detect 2.5% of all Linux CVEs. Further, the NVD CVE and public vulnerability databases miss many vulnerabilities, only catching 60% of the vulnerabilities Snyk tracks.
The increasing prevalence of open source components in every area of software and firmware development adds to the scanning gap. According to Snyk’s 2019 open source security report (https://snyk.io/opensourcesecurity-2019/), 37% of open source developers don’t do any sort of security testing during CI, and the median time from when a vulnerability was added to an open source package until it was fixed was over 2 years.
By adding a software immunization step for memory vulnerabilities in CI/CD pipelines before testing, when scanning typically takes place, developers can immediately reduce their vulnerability management workload by 40%. This will, in turn, allow scanning software developers (and pen testers) to refocus 40% of their attention and resources on other, unsolved vulnerability classes.
Make Patching More Effective
Patching, in general, comes in two flavors. Every release of every software product in all time contains bugs and vulnerabilities. Planned patches prioritize fixes to known bugs in the normal update cycle. Emergency patches, however, arise when high-severity bugs or vulnerabilities are identified that must be fixed before the release date of a standard update.
Planned updates are largely automated in CI/CD workflows, but can still have very significant costs, especially when infrastructure, OT, SCADA, or iOT systems are in the mix.
Emergency patching slows down development by redirecting bandwidth away from planned sprints and backlog priorities to fix severe technical debt. Interrupting new feature enhancements and potentially planned bug fixes, emergency patches reduce release velocity, with many associated downstream costs. They also force additional releases outside normal update windows, diverting devops cycles and in some cases requiring significant unplanned costs to actually implement the fixes.
Immunization renders memory vulnerabilities inert, allowing development organizations to contain fixes within planned update cycles, and even enabling teams to avoid some vulnerability fixes altogether, since the chance of their being exploited has been driven to zero.
Summary
Scanning and patching are constantly improving, aided by continuous investment and progress by devops automation companies. They are essential components of cyber security and software hygiene. The attack surface they address, however, is like the literal tip of the iceberg, with 97.5% of known Linux CVEs going undetected and a rising tide of unknown vulnerabilities coming from the “vast sea of potentially vulnerable components” associated with the ascendance of open source.
Complementing scanning and patching with a third discipline, software memory immunization, can reduce exposure dramatically by making an entire class of vulnerabilities unexploitable. Using memory protection techniques like those pioneered by RunSafe, organizations can inoculate compiled code from 40-70% of the most dangerous weaknesses in software today.
The post Security Scanning for Software Vulnerabilities appeared first on RunSafe Security.
]]>The post The Common Vulnerability That Fintech and Bananas Share appeared first on RunSafe Security.
]]>There has been spectacular scaling in the sector of late, and today there are no less than 27 billion-dollar valued Fintech companies. Unfortunately, lapses in cybersecurity have been equally spectacular, with over 1 billion dollars stolen from cryptocurrency exchanges in 2018. The perpetrators run the gamut from those who exploited vulnerabilities in crypto wallet software and servers to state-sponsored actors, including but not limited to, North Korea. The issues arise from a variety of sources: the increased connectivity of systems and the requirement that potentially incompatible interfaces now integrate; the expansion of fintech to previously unbanked populations, which are likely less technologically savvy; and the harvesting of customers’ data footprints, putting a bull’s eye on private information.
Fintech startups share a common issue with the big banks and main street financial institutions – a need for strong cybersecurity, since both are targeted by lone wolf cyber criminals and nation state hacking collectives. The 45-year old Society for Worldwide Interbank Financial Telecommunication (SWIFT) network, which is the backbone of international bank transfers, has itself been the subject of multiple hacks ranging from a few million, to over 1 billion dollars. Even the now 20-year old Paypal system, that generated so much wealth in the original dot com boom, has been breached. The attack on PayPal may have compromised up to 1.6 million customers’ information. TIO Networks, a cloud-based multi-channel bill payment processor and receivables management provider, which was acquired by PayPal in July 2017, was infiltrated.
Cloning is the weakness that is hidden in plain sight
Let’s focus on agribusiness for a moment to explain the analogy. The agriculture industry plants crops that grow most easily and produce the highest yield, while encouraging customers to prefer those. Cavendish bananas are a prime example – they are genetically identica威而鋼
l, and every one of them is a clone of the one next to it. Each is essentially part of the same plant. The inherent risk with Cavendish bananas is that a single malady – a bug or pathogen can wipe out the entire crop.
Now back to technology. Understandably, there is a great deal of attention paid to securing vulnerabilities where hackers are most easily able to penetrate financial systems such as weak Identity and Access Management (IAM), or poorly implemented encryption. However, the common weakness to all of the systems most commonly used in Fintech is actually hidden in plain sight – the solutions are all clones of each other!
Did you know that every SaaS solution, mobile app, or cloud back-end system is the same? It is the accepted practice to develop a standard image and scale it up from source code, along with third party libraries, middleware, frameworks and a supporting container, OS (operating system), or hypervisor infrastructure. Said another way, all the crucial parts of the Fintech ecosystem spring from the same plant.
United Fruit Company (rebranded in 1984 as Chiquita Brands International) used the same DNA crops over and over to achieve economies of scale and a uniform fruit. That worked well for some time, until Panama disease, a pathogen, wiped out banana plantations in the 1890’s. Nothing could preclude the spread of the virus. Instead of just infecting a single plant or field, the disease affected all crops everywhere. Sounds implausible? It already happened with bananas that were grown commercially as clones.
And it is expected to happen again.
As bananas remain vulnerable, cyberhardening immunizes software from malware spread
So, what can be done to combat weaknesses that allow software and hardware vulnerabilities to be exploited? Add as much natural resistance as possible to the code and monitor it as closely as possible. These are already best practices in the financial industry, with code inspections, firewalls, Intrusion Prevention Systems (IPS), and endpoint security.
Unfortunately, the presence of the protections noted above has caused adversaries to evolve newer memory-based, fileless and compromised supply chain zero-day attacks that side-step them entirely. Examples of the volume, variety, and strength of these attacks abound:
- NotPetya supply chain attack – most devasting cyberattack in history
- NSA – ”Adversaries increasingly turning to supply chain exploitation”
- Compromised supply chain attacks – 200% increase over last year
- Virtualization bugs skyrocketed – 275% increase over last year
- Fileless attacks – 10 X more likely than traditional attacks over last year
What is the best way for companies to stay ahead of the evolution? RunSafe Security’s Alkemist™ RASP (Runtime App Self Protection) and MTD (Moving Target Defense) binary transformation is an agentless, easy to use and simple to deploy approach. It keeps financial systems up and running by preventing scaling zero-day attacks in existing or new environments. It works at the binary level, so covers even third-party code – but doesn’t require access to any code. Most significantly, it makes all systems functionally identical, yet logically unique and denies malware the uniformity required to replicate, thereby sidestepping the risk posed by cloned bananas.
Alkemist protects and diversifies financial systems’ DNA. Its proactive protection compliments existing security approaches, reducing the costs and delays associated with reactive detection, alerting, SOC (Security Operations Center) triage, and expensive out-of-band patching. So, while your fruits and vegetables remain vulnerable, our technology ensures that your hardware and software doesn’t have to.
Contact us for more information.
The post The Common Vulnerability That Fintech and Bananas Share appeared first on RunSafe Security.
]]>The post Looking into BugZ’s Crystal Ball: What the Industry’s First Coleopteran Chief Vulnerability Officer Predicts for 2019 appeared first on RunSafe Security.
]]>Shortly after Thanksgiving, Marriott disclosed a breach of 500 million customers’ data, including passport numbers, as well as the fact that the unauthorized party had access for four years prior to the discovery. That’s equivalent to 450 more days than my projected life span. Quora, a question-and-answer website, also recently revealed a hack that exposed 100 million users’ information.
Unfortunately, these are not isolated incidents, but rather a weekly occurrence that should make organizations more vigilant about the magnitude and sophistication of cyber threats. Recently, I’ve spent a lot of time pondering what’s to come in the year ahead, and I’m not sure the news gets any better for my species. After conferring with my team at RunSafe Security, here are our projections for what we expect to see in 2019.
Internet-Connected Healthcare Devices Finally Merit Attention – The medical device supply chain will experience heightened scrutiny. Increases in vulnerabilities, accelerated by the integration of mobile devices, will propel cybersecurity as the top concern for manufacturers, healthcare providers, and regulatory bodies. Patient awareness will drive industry participants to adopt new approaches to mitigating the threats.
While aiming for the goal of improving patient outcomes, the increasing interconnectivity of medical devices introduces potential weaknesses for data security. One reason is that these implements for the diagnosis, prevention, monitoring, treatment or alleviation of disease were not built with security in mind. As such, they are an easy entry point for attackers, who can gain network access through the internet. From there they can move on to a server, which likely has rich patient data, or just cause mayhem by sabotaging a device’s intended use. Abbott and the Chertoff Group recently released a white paper that shares findings from their study of 300 physicians and 100 hospital administrators on cybersecurity challenges. They found that while the professionals interviewed view cybersecurity as a priority, the majority feel underprepared to combat cyber risks.
U.S. Government Gets Serious About Weapon Systems Security – With the publication of reports from the GAO and MITRE, as well as Secretary of Defense Jim Mattis’ launch of the Protecting Critical Technology Task Force, the Department of Defense will begin to address cyber vulnerabilities in legacy weapon systems.
The GAO report concluded that the Department of Defense weapon systems are “more software dependent and networked than ever before,” and therefore are susceptible to cyberattack from software vulnerabilities as well as the increased attack surface caused by their connectivity. Even more alarming is their assessment that between 2012 and 2017, nearly all major acquisition programs that were operationally tested had mission-critical cyber vulnerabilities that adversaries could compromise. The memorandum launching the task force stated that these vulnerabilities are “eroding the lethality and survivability of our forces.” It’s incumbent upon the Pentagon to rethink how to address cybersecurity at every stage of development, acquisition, and deployment. More specifically, the MITRE report recommends that “product integrity, data security, and supply chain assurance should become key contract award criteria.”
International Tensions Promote Cybercrime – As trade wars and tension between the U.S. and other countries escalate, international cybercriminals will utilize both ransomware and the injection of malware into embedded devices to disrupt the operation of critical infrastructure.
Stuxnet, WannaCry, NotPeyta, and Triton are just a few examples of the massive global damage that can be enacted to cripple healthcare, energy, manufacturing, and communications organizations. More than half of the world’s mobile phones, as well as almost all of the printed circuit boards are made in China. That country is suspected of embedding malicious microchips into server motherboards. The positive news is that on November 16, President Trump signed into law the Cybersecurity and Infrastructure Security Agency Act of 2018. This landmark legislation elevates the mission of the former National Protection and Programs Directorate (NPPD) within DHS and establishes the Cybersecurity and Infrastructure Security Agency (CISA). CISA leads the national effort to defend critical infrastructure against the threats of today, while working with partners across all levels of government and in the private sector to secure against the evolving risks of tomorrow. It is good to have additional focus on this issue, but more steps are required to proactively protect critical infrastructure.
The Need for Protection Overtakes Detection – Whether we’re considering threats to the medical supply chain, weapon systems, or critical infrastructure, traditional cybersecurity measures aren’t built to prevent malware from propagating, because they rely primarily on network and perimeter solutions like gateways, firewalls, intrusion monitoring, and anti-virus agents. In other words, these tools identify symptoms rather than address the underlying causes.
While established tools have worked for decades on known attack types, their effectiveness continues to diminish against motivated adversaries skilled in designing new types of exploits. Detection offers no protection in cases where the supply chain itself is compromised, such as in file-less attacks like memory corruption exploits, stack and heap attacks, zero-day attacks or return-oriented programming (ROP) chain attacks
One of the most effective means to reduce risk is to cyberharden systems using Runtime Application Self-Protection (RASP) technology. RunSafe Security’s Alkemist hardens software binaries by using RASP techniques such as binary stirring, control flow integrity, and stack frame randomization, processes that ensure that attackers can’t calculate in advance how to successfully execute their code. This can prevent an entire class of malware attacks from executing and spreading across multiple systems and devices. Remember, no matter what happens in cybersecurity in 2019, it’s not always the bug’s fault. So, before you blame us, ask yourself whether or not cyberhardening your ICS, embedded systems and devices would have helped you reduce the risk. And then contact us today to get the process of hardening your binaries started before we turn the page on 2018.
The post Looking into BugZ’s Crystal Ball: What the Industry’s First Coleopteran Chief Vulnerability Officer Predicts for 2019 appeared first on RunSafe Security.
]]>The post Chronicles of the Cyber-Newtonian Wormhole: A Cautionary Tale of an Exploited Vulnerability appeared first on RunSafe Security.
]]>The Cyber-Newtonian Wormhole bridges the perspectives between people who use systems to do a legitimate thing (Newtonian side of the wormhole) and the attackers that know how to hijack the system to perform something insidious and devastating (Cyber side of the wormhole). The capabilities of nation-state level hackers might appear as magical as a wormhole – popping in from thousands of miles away, months or years in the past, to change the course of our systems in very subtle, seemingly unimportant ways.
Modern cyber criminals are able to compromise victim systems with unfettered impunity. One possible explanation is that an undetectable wormhole opens up into our Newtonian-physics based lives and our computer systems just start behaving in unintended, quasi-magical ways. Another more likely explanation is that hackers have unlimited time and resources to pursue their goals.
But stay with me on the theme. This article will attempt to document the incursions by travelers from the cyber side of the wormhole into our neat, Newtonian lives. Then I’ll suggest a way to keep things rational and Newtonian.
The CANOPY WING Vulnerability
At the height of the Cold War, U.S. and Soviet governments were trying to answer the question of how to “win” a global nuclear war. While the public discourse on both sides of The Wall focused on how to fight and win World War III, a highly classified, dedicated group of Americans perfected a capability to make sure that war never happened.
CANOPY WING was a series of tactics that could disrupt Soviet military and missile communications. While the details of the vulnerability remain beyond the reach of this author, we do have insights into ways it could be exploited. NATO forces would be able to both block legitimate orders from Soviet leadership to launch Soviet nuclear weapons, and also generate fake orders to the Soviet Air and Ground forces that could “take them out of the fight” for 10-15 minutes.
Strategies around the utilization of this capability remain classified, but well sourced analysis by Benjamin B. Fischer suggests that CANOPY WING would be part of a pre-emptive decapitation strike against Soviet forces, in the face of an imminent Soviet first strike.
Weaponizing the Weakness
The capability of CANOPY WING shifted the balance of power in the Cold War. It’s also a jaw dropping example of exploiting a system vulnerability. (I’ll get back to the analogy in a bit.)
Using techniques that presage current information warfare, U.S. analysts were able to transform an isolated system weakness into a strategic capability that could change the course of life on Earth.
CANOPY WING was a program “designed to exploit a Soviet communications vulnerability uncovered in the late 1970’s.” The electronic warfare capabilities were able to crack a single communications vulnerability into an entire infrastructure, “for a nuclear first strike.” The complete CANOPY WING capability was able to:
- Precisely identify Soviet and Warsaw Pact command centers, evacuation sites, military installations, armed forces, and communications facilities;
- Identify methods for short-circuiting communications and weapons systems using carbon-fiber particles;
- Block communications electronically immediately prior to an attack, thereby rendering a counterattack impossible;
- Target precision weapons to destroy command-and-control centers while communications were blocked; and
- Generate false commands to aircraft and submarines, using computer-simulated voices (one of the most audacious nuances in this capability).
Analysis of the Architecture and Protocol
The list of CANOPY WING capabilities assembled allows us to infer a few things about the actual vulnerability and the overall system architecture. A few points of conjecture:
- The vulnerability allowed for unauthorized sources. Anyone can generate an RF signal, but some weakness in the system did not filter out RF that came from unauthorized sources.
- The architecture allowed for system wide denial. Certain network architectures, such as Ethernet (802.3) and walkie-talkies allow for a malicious party to disrupt all communications from one single point by just flooding packets or holding down the push-to-talk button, respectively.
- The architecture had no apparent ability to detect that it was being probed. Years’ worth of unauthorized system interrogation went undetected and occurred from inside U.S. and NATO facilities.
- The communications protocol allowed extensive interrogation about location and system information.
- Message authentication procedures seemed incomplete. For a well-formatted message to be accepted, the sender must self-identify, usually with some type of “sender ID” that is separately verifiable.
The Takeaway – Assume All Vulnerabilities are Compromised
The Cyber-Newtonian Wormhole – and likewise exploits of software vulnerabilities – can’t be kept at bay with a silver bullet. To keep your company’s assets from becoming an unwitting part of another country’s foreign policy objectives, you must contemplate how every part of your system can be misused. The analysis of how something can be exploited can’t be faithfully done by Newtonians but must come from the other side of the wormhole. It is too easy in a risk matrix to say, “no one could do that.”
Get the perspectives of professional hackers in weighing the risks of each potential point of vulnerability. Crack the wormhole open and understand how the magicians on the other side work. Come to understand the mentality and methods behind perturbing legitimate system behavior. A major obstacle that leaves companies unaware of the wormhole’s capabilities is reluctance to accept that one’s own system could be “the weakness” or have “the flaw.”
RunSafe Security’s assumption is that your system has likely already been compromised. Thankfully, our runtime application self-protection (RASP) transformation product Alkemist can mitigate the work of the magicians by randomizing software binaries. That process prevents malware from executing and replicating. Cloud architecture providers, telecommunications companies, automotive OEMs, and other critical infrastructure organizations which can’t afford to have a disruption in operations are using Alkemist as a proactive layer of defense.
To learn more about how Alkemist works, click here.
The post Chronicles of the Cyber-Newtonian Wormhole: A Cautionary Tale of an Exploited Vulnerability appeared first on RunSafe Security.
]]>



