The post The RunSafe Security Platform Is Now Available on Iron Bank: Making DoD Embedded Software Compliant and Resilient appeared first on RunSafe Security.
]]>The challenge for defense programs is that meeting these requirements, particularly for embedded systems, often results in increased labor and difficulty in getting tools approved and deployed.
That’s why we’re excited to share that the RunSafe Security Platform is now available on Iron Bank, the DoD’s hardened repository of pre-assessed and approved DevSecOps solutions.
As a verified publisher, RunSafe provides DoD software development teams with access to Software Bills of Materials (SBOM) generation, supply chain risk management (SCRM), and code protection through an ecosystem they already trust.
Why Iron Bank? A More Secure Path
Iron Bank is built to help defense programs quickly deploy new tools without spending months navigating approval processes. Every product listed on Iron Bank goes through rigorous security assessments, container hardening, and compliance validation. Because the containers are scanned daily for vulnerabilities, DoD teams gain access to resilient tools that keep the software supply chain secure and get software to deployment faster.
With RunSafe listed as a verified publisher, DoD teams and integrators can now pull down the platform directly from Iron Bank, making it easier for defense programs to integrate and use.
What RunSafe Brings to Iron Bank
The RunSafe Security Platform addresses some of the toughest challenges in embedded software security. Here’s what you can access through Iron Bank:
C/C++ SBOM Generation
RunSafe provides the authoritative build-time SBOM generator for embedded systems and C/C++ projects. Automating SBOM generation is critical for meeting DoD requirements, especially for unstructured C/C++ code where traditional SBOM tools fall short.
Supply Chain Risk Management
SCRM capabilities enable DoD teams to take action, not just generate a static SBOM. Teams can monitor for new vulnerabilities and check license enforcement and provenance. With a complete, correct SBOM, teams can implement required SCRM practices.
Runtime Code Protection
RunSafe hardens binaries against exploitation through moving target defense (e.g. Runtime Application Self Protection (RASP)), defending weapons systems at runtime to increase resilience. This resilience applies to future zero days as well, providing fielded weapon systems protection between software upgrade cycles that can be two years apart.
Accessing the RunSafe Security Platform on Iron Bank
If your program is working to modernize DevSecOps practices, automate SBOM generation, or secure embedded systems without code rewrites, RunSafe is now available directly on Iron Bank.
You can find our containers by logging in and accessing the Iron Bank repository here.
Request a consultation to learn more about the RunSafe Security Platform and Iron Bank.
The post The RunSafe Security Platform Is Now Available on Iron Bank: Making DoD Embedded Software Compliant and Resilient appeared first on RunSafe Security.
]]>The post From Black Basta to Mirth Connect: Why Legacy Software Is Healthcare’s Hidden Risk appeared first on RunSafe Security.
]]>Key Takeaways:
- Legacy medical devices running old code create growing cybersecurity and patient safety risks
- Ransomware attacks on hospitals show how downtime directly impacts clinical care
- Security transparency and SBOMs are now key to winning healthcare procurement deals
- Cyber resilience—not just compliance—will define the next era of connected healthcare
Hospitals and medical device manufacturers are facing a quiet crisis rooted not in cutting-edge exploits or nation-state hackers, but in old software.
Across healthcare, legacy code is turning routine cybersecurity weaknesses into real-world patient safety risks. The problem is simple to explain and hard to solve: devices built to last for decades are now connected to modern networks, yet run on outdated and difficult-to-patch code.
As connected devices become the norm, this technical debt has become a liability that extends to patient care.
In a discussion on the business realities of medical device cybersecurity, Shane Fry, CTO of RunSafe Security, Patrick Garrity, Security Researcher at VulnCheck, and Phil Englert, VP of Medical Device Security Health-ISAC, discussed the vulnerability and compliance landscape and where software security comes into play.
Watch the full webinar for more on medical device cybersecurity here.
When “Forever Devices” Become Forever Vulnerable
A medical device can remain in use for 15-20 years. That longevity might make sense for hospitals managing costs, but it means the software inside those devices is often frozen in time. Meanwhile, the threat landscape moves forward.
“These devices can be used for decades,” said Patrick Garrity, Security Researcher at VulnCheck. “That becomes a real challenge. Manufacturers have to be mindful of that.”
Imagine a connected infusion pump or imaging system that still relies on a Windows 7 or even XP base. Patches stop, drivers go unsupported, and over time, the device becomes a soft target on an otherwise modern network.
And because medical systems are tightly integrated—feeding data into hospital EMRs, remote dashboards, and cloud platforms—an outdated component in one corner of the network can expose an entire healthcare operation.
When Cyber Weaknesses Become a Patient Safety Risk
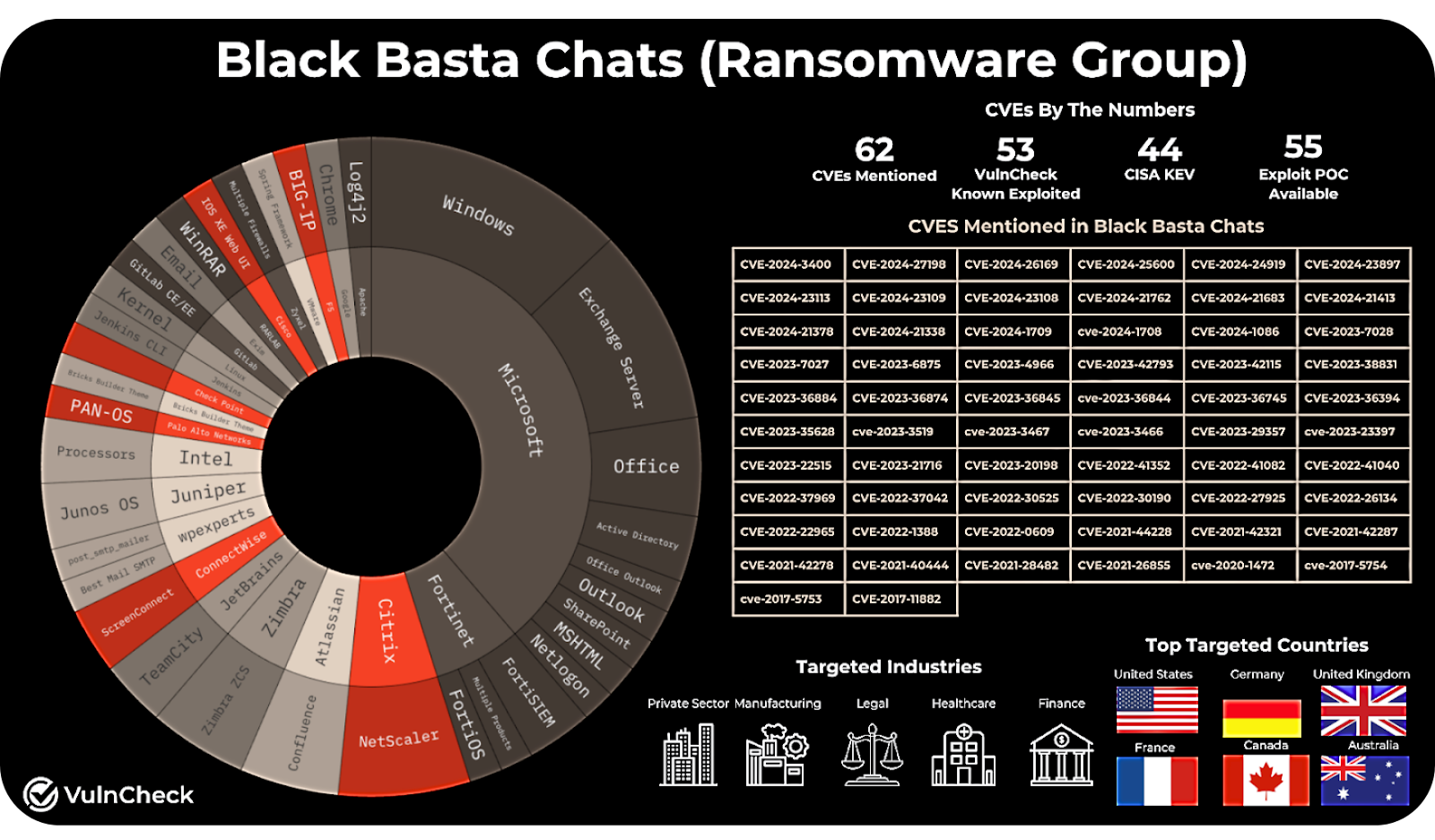
The stakes became clear during the Black Basta ransomware attack on Ascension Health earlier this year. Hospitals were forced to revert to paper-based systems. Electronic medical records, scheduling systems, and digital imaging were suddenly inaccessible.
RunSafe Security CTO Shane Fry summed up the real-world impact: “If your network’s down, you can’t do surgery.”
Beyond the immediate operational disruption, the consequences for patients were serious. Doctors faced delays accessing treatment histories. Pharmacists couldn’t verify prescriptions electronically. In some facilities, even infusion pumps and lab equipment had to be taken offline as a precaution.
Ransomware may be the headline, but the underlying vulnerability is the same—cybersecurity weaknesses left unaddressed.
As Phil Englert, VP of Medical Device Security at Health-ISAC, noted: “Cyber is a failure mode. It’s a way for things not to work or not to work as intended when you want them to.”
When software failures and weak security controls ripple into care delivery, cybersecurity is a patient safety imperative.
Where Exploitation Starts
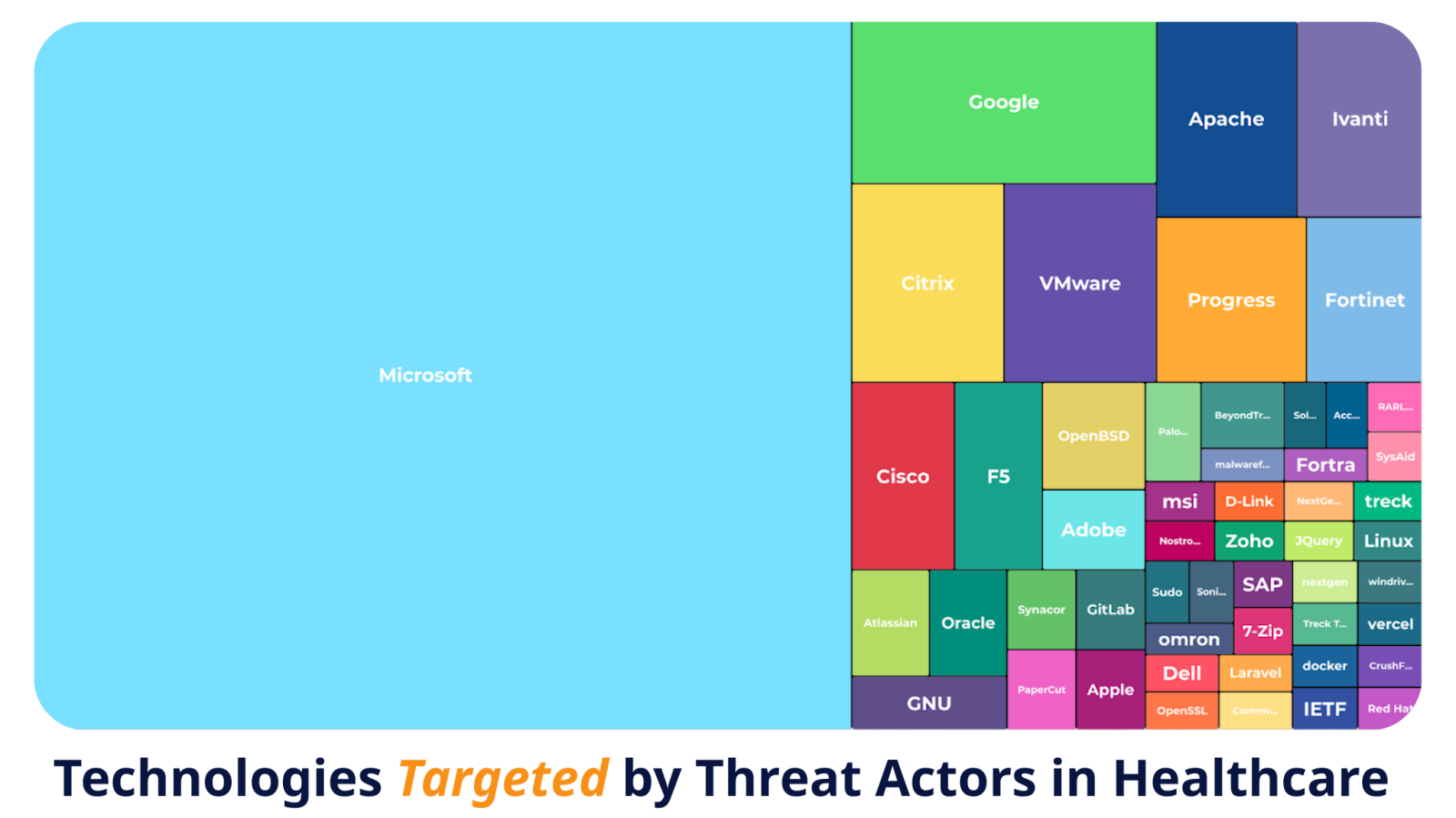
Most healthcare breaches don’t start with exotic zero-days. They start with vulnerabilities everyone already knows about.
Attackers target what’s common: outdated Microsoft servers, unpatched remote access tools, misconfigured network gateways, and open-source components left to age quietly inside medical devices.
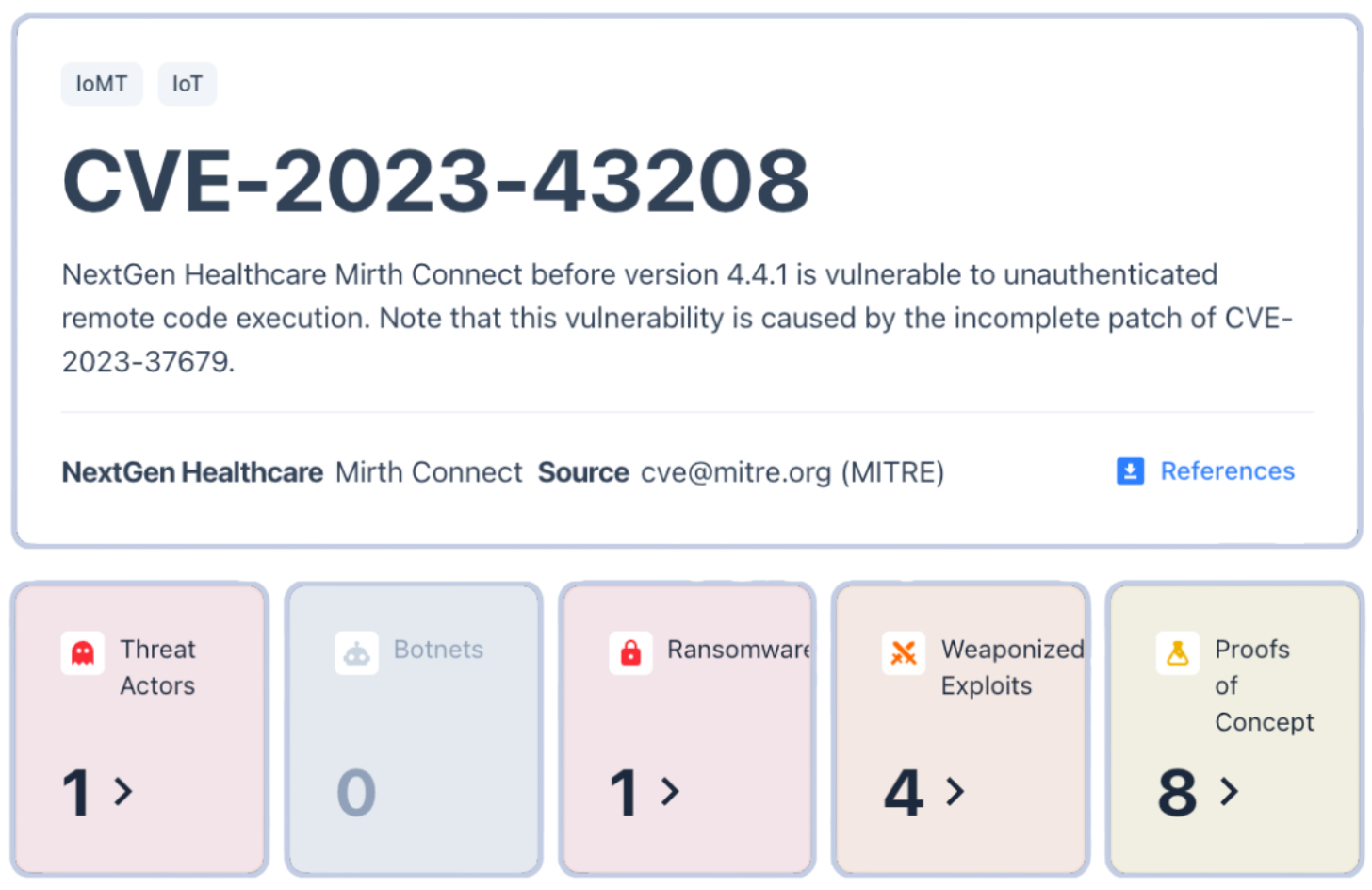
Garrity pointed to examples such as NextGen Healthcare’s Mirth Connect, a popular data exchange system exploited in ransomware campaigns. The flaw wasn’t obscure, as it had been publicly documented and patched. Yet more than a year later, vulnerable systems remained exposed online, still running unpatched versions.
“Threat actors are going to opportunistically target anything and everything. And… they’re just using what’s already published and off-the-shelf,” Garrity said. “Even outdated remote management tools or cloud connectors can become attack surfaces.”
Legacy software turns these well-known weaknesses into long-term liabilities. Once a system goes unpatched, every new connection—every piece of cloud integration or remote monitoring—adds to the risk.
The Business Risk of Standing Still
The consequences of cybersecurity weaknesses aren’t limited to downtime or headlines—they directly affect revenue and market access.
According to RunSafe Security’s 2025 Medical Device Cybersecurity Index, 83% of healthcare buyers now include cybersecurity standards in their RFPs, and 46% have declined to purchase medical devices due to security concerns. Outdated or insecure software doesn’t just pose a technical problem; it can cost sales.
For device manufacturers, the message from buyers is unmistakable: security maturity equals market readiness. Procurement teams are treating cybersecurity posture as a business criterion alongside clinical performance and cost.
Hospitals, too, are taking notice. Many are implementing procurement checklists requiring vendors to provide Software Bills of Materials (SBOMs), vulnerability response plans, and clear lifecycle support documentation. Without those, even innovative technologies struggle to clear the contracting stage.
Modernizing Security for Long Device Lifespans
Managing legacy code in a regulated, high-stakes industry isn’t easy, but it’s not impossible. The most resilient organizations are taking pragmatic, layered steps to reduce risk without overhauling every device.
1. Build-Time SBOMs
Create and maintain Software Bills of Materials (SBOMs) during the build process, not after. This ensures visibility into every dependency and allows for continuous monitoring of vulnerabilities over time.
2. Exploit-Based Prioritization
Focus patching on vulnerabilities with known exploitation in the wild, not just those with high CVSS scores.
3. Compensating Controls
Where patches aren’t possible, use segmentation, strict access controls, and runtime protections to reduce exposure.
4. Design for the Next Decade
Reserve processing and storage capacity for future updates and plan for cryptographic agility so devices remain secure over their full lifespan.
5. Transparent End-of-Life Policies
Communicate openly about support timelines and risk mitigation options. Buyers and regulators increasingly view transparency as part of good cybersecurity hygiene.
From Compliance to Resilience
Healthcare is shifting from a “check-the-box” approach to one centered on resilience. Regulators are reinforcing that shift: the FDA’s premarket guidance now requires SBOMs and vulnerability management plans, while the EU’s Cyber Resilience Act pushes similar expectations globally.
The result is a new baseline where cyber hygiene and secure design aren’t just best practices, they’re business necessities.
“If you don’t know what’s in the software you’re deploying to your networks, then how can you know that a vulnerability affects you?” Fry said. “Without that Software Bill of Materials, you’re going to be very limited.”
For manufacturers and healthcare providers alike, addressing legacy code is about security and trust. It’s about maintaining operational continuity. And ultimately, it’s about keeping patients safe in a world where every connected device is part of the care equation.
As Fry put it: “Everything that we should be doing in cybersecurity should be viewed through … the lens of making sure the patient can get the best care they need as quickly as they can.”
For more on medical device challenges and defenses, listen to our panel discussion: From Ransomware to Regulation: The New Business Reality for Medical Device Cybersecurity.
The post From Black Basta to Mirth Connect: Why Legacy Software Is Healthcare’s Hidden Risk appeared first on RunSafe Security.
]]>The post Beyond Patching: How to Secure Medical Devices and Meet FDA Compliance Without Changing Code appeared first on RunSafe Security.
]]>Key Takeaways:
- Legacy devices can’t be patched easily, but compensating controls provide alternatives.
- SBOMs are critical for transparency and accountability.
- The FDA now mandates secure development and life cycle planning.
- Cybersecurity and patient safety are inseparable—breaches harm care.
- Collaboration is the only sustainable path forward.
In healthcare cybersecurity, one of the biggest challenges is protecting medical devices that are difficult to patch and written in memory unsafe languages. Unlike web applications or mobile software, which can be updated overnight, medical devices are often built to last 10–15 years and aredesigned for reliability and patient safety—not constant code revisions.
Yet cyber threats are growing, and FDA regulations are tightening. Manufacturers and healthcare providers are now under pressure to secure legacy systems while keeping patients safe. The question is: how can this be done without rewriting a single line of code?
This was the focus of a recent episode of Exploited: The Cyber Truth, featuring Phil Englert (VP of Medical Device Security at Health-ISAC) and Joseph M. Saunders (Founder & CEO of RunSafe Security). Their insights offer a practical roadmap that blends compensating controls, regulatory awareness, and industry collaboration.
The Reality of Legacy Devices: Built to Last, Hard to Secure
Medical devices weren’t designed with today’s cybersecurity challenges in mind. Hospitals rely on equipment that often stays in service for a decade or more, from MRI machines to pacemakers, because replacing them isn’t financially or operationally feasible. These devices also run on limited computing resources and cannot tolerate downtime, making traditional patching nearly impossible.
As Englert explained, “We’ve painted a target on our back” by connecting these devices to networks for efficiency and data sharing but without always providing the necessary safeguards. That combination of longevity, limited resources, and operational necessity makes securing these devices a unique and ongoing challenge.
Security Without Code Changes: What It Really Means
When patching or rewriting isn’t an option, the focus shifts to compensating controls, or ways to secure devices without touching their software, as well as opportunities for code protection.
- Monitoring: Establishing real-time visibility into device activity to catch anomalies early.
- Segmentation: Isolating devices so that a breach doesn’t cascade across the network.
- Code Protection: Secure embedded devices in real-time to prevent attacks.
These approaches are not one-size-fits-all. The strategy for an implanted pacemaker is very different from that for a helium-filled MRI machine. But the principle remains: if you can’t harden the device itself, you must harden its environment.
SBOMs: Building Trust Through Transparency
Another theme from the discussion was the rise of Software Bills of Materials (SBOMs). Much like a nutrition label on food, SBOMs give visibility into the “ingredients” inside a medical device. This transparency allows healthcare providers to quickly assess whether known vulnerabilities, like Log4j, impact their devices, hold manufacturers accountable, and make smarter, risk-based decisions about deployment.
As Saunders noted, SBOMs are most valuable when generated close to the point of software production, ensuring accuracy and reliability.
FDA Compliance: Guidance Becomes Mandate
For years, FDA cybersecurity guidance was considered “best practice.” That changed in December 2022 when Congress gave the FDA statutory authority over device cybersecurity under the PATCH Act. By March 2023, manufacturers were required to follow a secure software development lifecycle, account for the full environment in which devices operate, and maintain controls and documentation throughout the device’s lifespan.
This represents a major shift. Compliance is now enforceable, and the focus has expanded from protecting data to ensuring patient safety across interconnected healthcare ecosystems.
Why Patient Safety Is the True Bottom Line
Cybersecurity lapses aren’t abstract IT problems—they have real consequences for patient outcomes. Studies show that clinical performance can decline for up to 18 months following a hospital breach, as resources are diverted to recovery efforts. The “blast radius” often extends beyond one hospital, affecting neighboring facilities that absorb overflow patients.
Among organizations that experienced cybersecurity incidents affecting medical devices, 75% said that cyber incidents caused at least a moderate patient care impact. 46% required manual processes to maintain operations and 24% required patient transfers to other facilities.
As Saunders emphasized, “Cybersecurity is an enabler of patient safety.” Even the most advanced medical care can be undermined without strong cybersecurity practices in place.
Collaboration: The Missing Piece
Perhaps the most actionable takeaway is that no single organization can address these challenges alone. Manufacturers, healthcare providers, regulators, and third-party service organizations all have roles to play.
Practical steps include:
- Negotiating stronger controls before adopting new devices.
- Sharing information through groups like Health-ISAC.
- Starting small—building inventories, mapping data flows, and tightening controls incrementally.
Englert summed it up best: “80% of anything is better than 100% of nothing. Start where you can with the resources you have.”
For more insights on medical device cybersecurity, download RunSafe’s 2025 Medical Device Cybersecurity Index.
The post Beyond Patching: How to Secure Medical Devices and Meet FDA Compliance Without Changing Code appeared first on RunSafe Security.
]]>The post The Top 7 Medical Device Vulnerabilities of 2025 appeared first on RunSafe Security.
]]>As reported by healthcare executives across the U.S., UK, and Germany in RunSafe Security’s 2025 Medical Device Cybersecurity Index, the most critical vulnerabilities in medical devices fall into seven categories: malware infections, network intrusions, ransomware targeting device operations, remote access exploitation, supply chain compromises, vendor-identified vulnerabilities, and data exfiltration.
These are the weaknesses shaping the medical device cybersecurity landscape in 2025.
Listen to the Audio Overview
The 7 Most Critical Medical Device Cybersecurity Risks
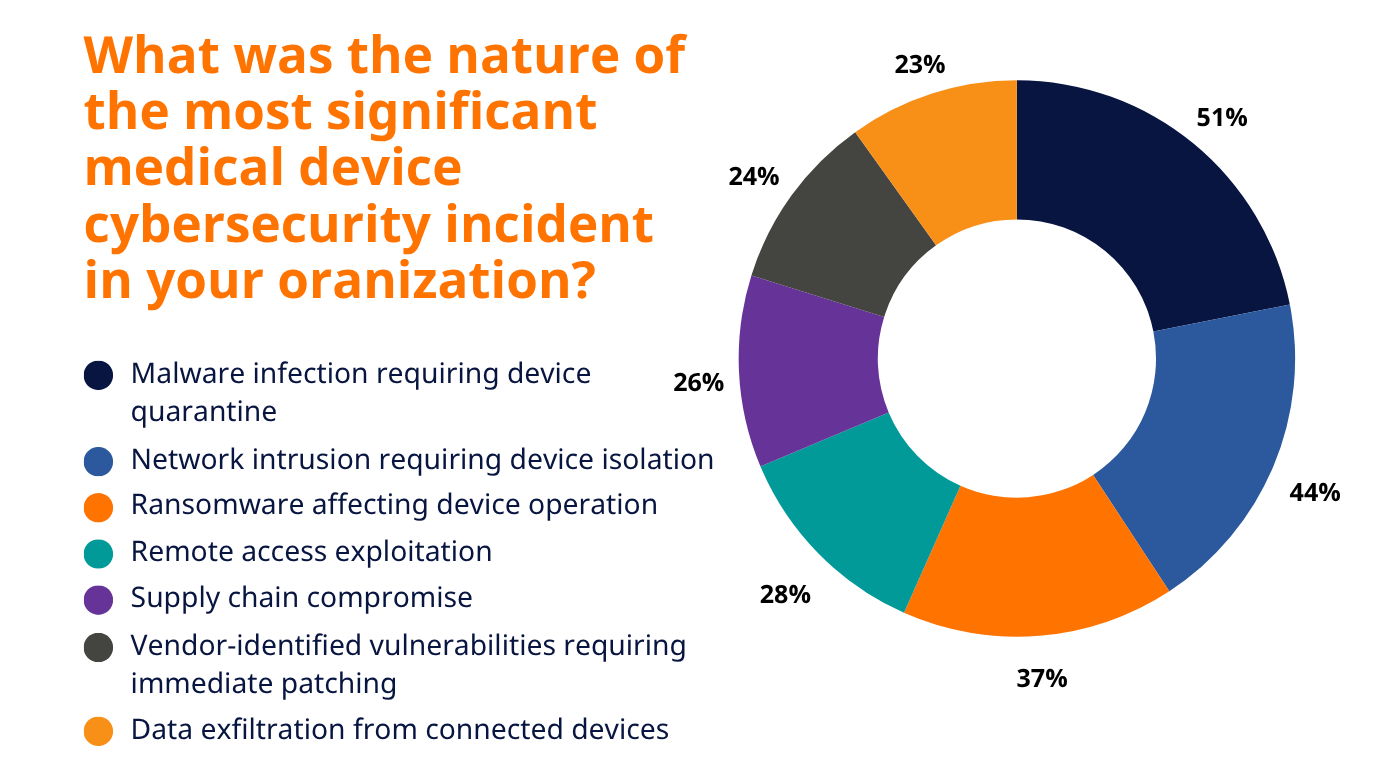
1. Malware Infections (51% of Organizations Affected)
Malware remains the most widespread vulnerability in medical devices, as reported by healthcare leaders. 51% listed malware infections requiring device quarantine as the most significant medical device cybersecurity incident at their organization.
Often, malware infections are targeted campaigns that force organizations to quarantine devices and disconnect systems. For example, malware can force radiology departments to take entire imaging systems offline to prevent spread, leading to delays in diagnostics. In some cases, malware has been used to wipe device firmware or corrupt system files, requiring full reinstallation before devices can be put back into service.
The consequence is not just about downtime, but also about cascading disruption—if a key device type, such as ventilators or pumps, is quarantined, entire treatment processes can be delayed.
2. Network Intrusions (44% of Organizations Affected)
Nearly half of organizations experienced intrusions into networks hosting medical devices. Network intrusions targeting medical devices are among the most severe forms of attack, as they often remain undetected for extended periods. Attackers can gain unauthorized access through poorly segmented networks, default credentials, or outdated communication protocols.
An example is when adversaries pivot from compromised IT systems into clinical device networks, gaining visibility into—and sometimes control over—networked equipment such as monitoring systems or infusion pumps. Intruders may then install backdoors, capture sensitive data in transit, or manipulate device functions.
Unlike IT breaches focused on stealing files, network intrusions into medical devices often create silent footholds that persist until they are specifically identified and removed.
3. Ransomware Targeting Device Operations (37% of Organizations Affected)
More than one-third of organizations reported ransomware specifically disrupting device operations. Unlike traditional ransomware, these campaigns target availability rather than just data.
For example, ransomware designed to target imaging systems can lock operators out of MRI or CT machines, effectively halting diagnostic capabilities until ransom demands are met. Similarly, ransomware targeting infusion pumps or surgical robots can force organizations to suspend treatment procedures.
The distinguishing factor here is intent: attackers understand that the availability of these devices is essential, making disruption itself the pressure point rather than data encryption alone.
4. Remote Access Exploitation (28% of Organizations Affected)
Remote access is vital for servicing, diagnostics, and software updates—but it has also become a primary entry point for attackers. Nearly three in ten organizations reported that remote access was exploited to compromise devices.
This typically occurs when attackers identify unsecured remote desktop sessions, weak VPN configurations, or vendor accounts with excessive privileges. Once inside, adversaries can move laterally across device networks or alter system settings.
A common scenario is the exploitation of default or reused credentials for remote maintenance tools, which grants attackers the same level of control as authorized technicians.
5. Supply Chain Compromises (26% of Organizations Affected)
Software supply chain attacks introduce vulnerabilities long before devices are deployed in hospitals. One in four organizations experienced compromises traced back to third-party software, libraries, or hardware components embedded in their devices.
A well-known example outside healthcare is the SolarWinds compromise, but similar attacks in the medical sector can introduce malicious code into firmware or software updates distributed by a trusted vendor. When those updates are applied, every customer organization inherits the vulnerability.
Due to their scale, software supply chain compromises can impact thousands of devices across multiple healthcare systems simultaneously, making them particularly challenging to contain.
6. Vendor-Identified Vulnerabilities Requiring Updates (24% of Organizations Affected)
Nearly a quarter of organizations faced critical vulnerabilities identified and disclosed by their device vendors. While transparency is essential, patching medical devices poses unique challenges compared to traditional IT.
Devices often require downtime for testing and validation before updates can be applied, and in regulated environments, some patches may trigger re-certification processes. For example, if an imaging device firmware update conflicts with existing calibration protocols, the device must be retested before it can be returned to service.
This means that even when fixes are available, the process of applying them can be slow and disruptive, leaving exploitable windows open for attackers.
7. Data Exfiltration from Devices (23% of Organizations Affected)
Data theft remains a significant issue, with nearly one in four organizations reporting exfiltration from medical devices. These devices often process highly sensitive patient information, including imaging results, diagnostic data, and treatment histories.
For example, compromised cardiology devices can leak continuous heart monitoring data, or imaging systems can be used to extract thousands of patient scans. In some attacks, stolen data is packaged and sold on underground markets, where medical records often fetch higher prices than financial information.
As devices become more interconnected and data-rich, they expand the potential attack surface for adversaries seeking to capture and monetize sensitive healthcare information.
Download our guide to securing medical device software throughout its lifecycle, from development through deployment.
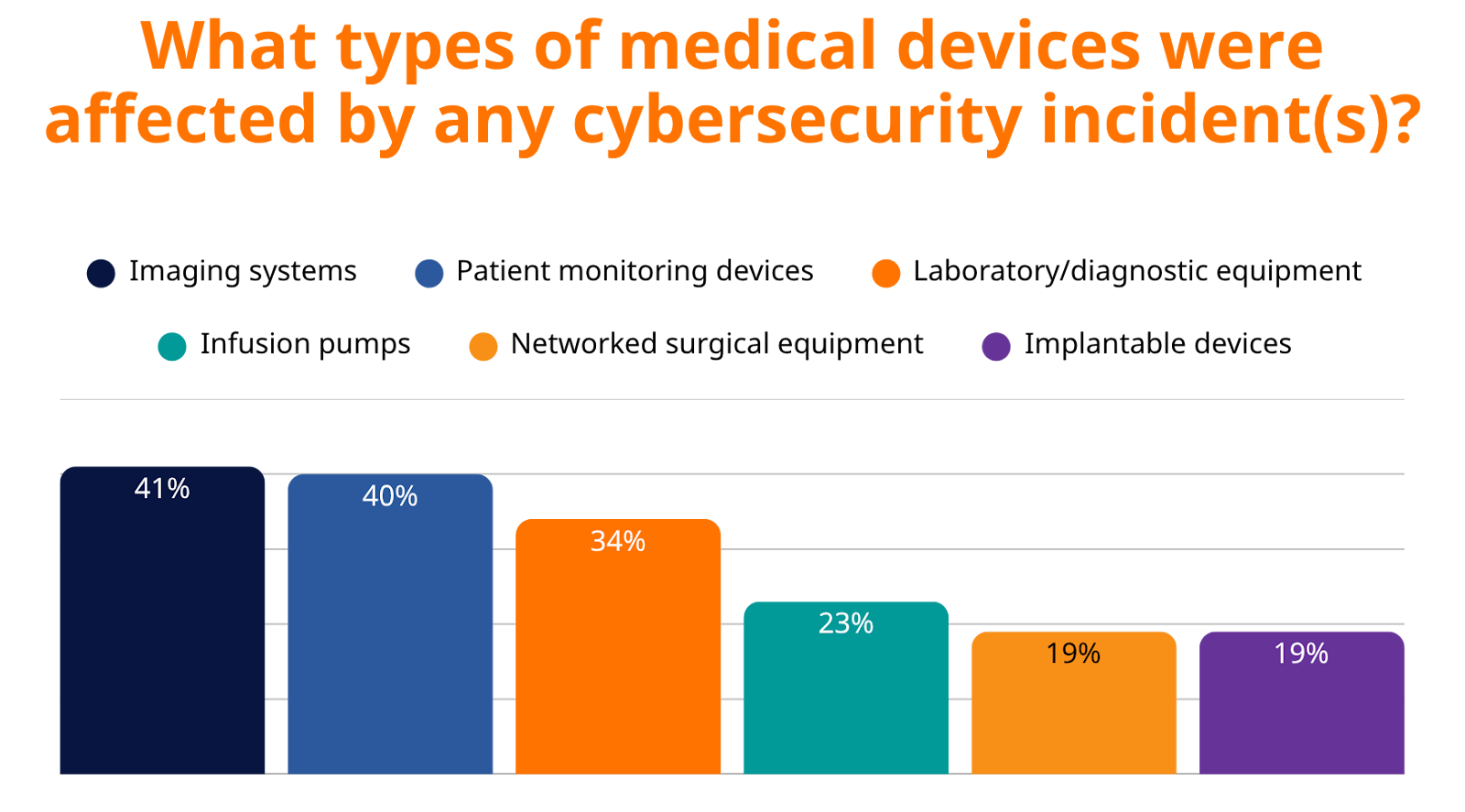
What Medical Devices Are Being Targeted in 2025?
Attackers are going after the backbone of patient care. Cybercriminals are successfully targeting the very systems healthcare providers depend on most for patient diagnosis, treatment, and monitoring, including:
- Imaging Systems (41%) – CT, MRI, X-ray
- Patient Monitoring Devices (40%) – ICU and emergency care essentials
- Laboratory/Diagnostic Equipment (34%) – Core to diagnosis and treatment
- Infusion Pumps (23%) – Life-sustaining medication delivery
- Networked Surgical Equipment (19%) – Operating room systems
- Implantable Devices (19%) – Pacemakers, insulin pumps, and more
Why These Vulnerabilities Matter for Medical Device Manufacturers
The 2025 landscape makes one thing clear: medical devices are now at the center of the cybersecurity conversation. From malware and ransomware to supply chain compromises, attackers are finding multiple pathways to exploit weaknesses that directly affect device reliability and trust.
For manufacturers, the implications are significant. Healthcare providers, regulators, and procurement teams are scrutinizing device cybersecurity more closely than ever. Vulnerabilities are no longer viewed as isolated technical flaws but are seen as risks to adoption, compliance, and long-term market success.
Understanding these seven critical vulnerabilities provides a roadmap for where design choices, testing protocols, and security investments will have the greatest impact. Manufacturers that take these threats seriously will not only strengthen their products but also differentiate themselves in a market where resilience is becoming a baseline requirement.
The insights in this post are based on RunSafe Security’s 2025 Medical Device Cybersecurity Index, a comprehensive survey of healthcare decision-makers on medical device cybersecurity. For manufacturers, it’s a clear signal of where to focus security efforts and how to meet the expectations of regulators and healthcare buyers.
Explore the full report to see the data, trends, and guidance shaping the future of secure medical devices.
The post The Top 7 Medical Device Vulnerabilities of 2025 appeared first on RunSafe Security.
]]>The post What Product Leaders Need to Know About EU CRA, FDA, and Cyber Regulations appeared first on RunSafe Security.
]]>The regulatory landscape for product security has fundamentally shifted. What was once a “nice-to-have” consideration has become mandatory compliance across industries, with cybersecurity now sitting at the center of product development, risk management, and go-to-market strategies.
Product leaders today face mounting pressure from multiple regulations—the EU Cyber Resilience Act (CRA), FDA cybersecurity requirements, and a growing list of industry-specific mandates—while still needing to maintain innovation speed and profitability. The stakes couldn’t be higher: non-compliance risks include fines up to €15 million or 2.5% of global turnover under the CRA, market access restrictions, and potentially devastating reputational damage.
But here’s the critical insight that forward-thinking product leaders are discovering: these regulations don’t have to be a burden. When approached strategically, regulatory compliance can become a competitive differentiator that strengthens products, builds customer trust, and creates sustainable business advantages.
Listen to the Audio Overview
The Product Compliance Tidal Wave: Understanding the Forces at Play
The 2024-2025 period has seen new cybersecurity regulations appear across sectors, representing a fundamental shift in how responsibility for product security is assigned and enforced.
The most significant change is the shift in liability. Under traditional models, end users often bore responsibility for securing the products they purchased. Today’s regulations flip this dynamic, making manufacturers the primary guardians of product security throughout the entire lifecycle. The CRA rebalances responsibility toward manufacturers and sets new standards across product lifecycles, fundamentally changing how companies must approach product development and support.
Supply chain transparency has become another critical factor. New requirements for Software Bills of Materials (SBOMs) and vulnerability disclosure mean that product leaders can no longer treat their supply chains as black boxes. Every component, every dependency, and every potential vulnerability must be catalogued, monitored, and managed.
As RunSafe Founder and CEO Joe Saunders has emphasized, “If a vendor can’t tell you what’s in their product, chances are, they don’t know either.” This lack of knowledge will no longer fly with consumers, regulators, or internal risk management teams.

Perhaps most importantly, these regulations demand a cultural transformation within organizations. As noted by cybersecurity experts at IMD Business School in a June 2025 Qt Group analysis, “the EU Cyber Resilience Act demands a fundamental cultural and leadership shift in organizations,” moving away from security as a bolt-on feature to security as a foundational element of product design.
The EU Cyber Resilience Act: A New Paradigm for Product Security
The CRA represents the most comprehensive product security regulation to date, with implications that extend far beyond European borders. Understanding its requirements isn’t just about compliance, it’s about understanding where the entire industry is heading.
Timeline and Strategic Implications
The CRA entered into force on December 10, 2024, but the most critical date for product leaders is December 11, 2027, when most obligations become enforceable. This timeline creates both urgency and opportunity: companies that start preparing now will have significant advantages over competitors who wait until the last minute.
The regulation’s scope is deliberately broad, covering all connected products and software sold in the EU, regardless of where the manufacturer is located. This means that any company selling digital products globally needs to consider CRA compliance as a baseline requirement.
Core Requirements That Change Everything
The CRA’s “Secure-by-Design” mandate isn’t just regulatory language but a complete shift in how products must be conceived, developed, and maintained. Security can no longer be retrofitted; it must be integral from the earliest design phases.
Vulnerability management under the CRA requires manufacturers to report vulnerabilities within 24 hours of discovery and implement coordinated disclosure processes. This creates new operational requirements but also opportunities for companies that excel at rapid response and transparent communication.
The documentation requirements are extensive, covering security documentation, risk assessments, and conformity declarations. While this creates an administrative burden, it also forces companies to develop more rigorous security practices that typically result in higher-quality, more resilient products.
Post-market obligations represent perhaps the biggest shift, requiring ongoing security updates for a minimum of five years or the expected product lifetime. This transforms the economics of product development, making long-term security support a core business consideration rather than an afterthought.
FDA Cybersecurity Requirements: Medical Devices Lead the Way
The FDA’s 2025 cybersecurity guidance updates represent a maturation of medical device security requirements, but their implications extend beyond healthcare. As one of the most regulated industries, medical devices often preview compliance approaches that eventually spread to other sectors.
The New Enforcement Reality
The FDA’s latest guidance mandates that cybersecurity must be demonstrated from pre-market design through post-market support, with strong documentation on vulnerabilities and supply chain transparency for all device components. This lifecycle approach mirrors the CRA’s philosophy and suggests a convergence toward comprehensive product security requirements across industries.
The emphasis on SBOM requirements for connected medical devices creates new transparency obligations but also opportunities for companies that can demonstrate superior supply chain security. Companies that proactively implement robust component tracking and vulnerability management will find themselves better positioned for both regulatory compliance and customer trust.
Strategic Impact on Product Development
The FDA’s approach changes go-to-market strategies for medical technology companies. Security documentation is now part of the regulatory submission process, meaning that security considerations must be built into product development timelines from the beginning.
This creates new resource allocation challenges, as companies need dedicated cybersecurity expertise within product teams. However, it also creates competitive advantages for companies that develop this expertise early and can demonstrate superior security practices to customers and regulators.
Learn more about navigating vulnerability identification and postmarket cybersecurity for medical devices in this video: On-Demand Webinar: Medical Device Cybersecurity Challenges
Strategic Focus Areas: Maximizing ROI on Security Investments
With limited resources and expanding regulatory requirements, product leaders must prioritize their security investments strategically. The most successful companies focus on areas that provide both regulatory compliance and business value.
Supply Chain Security and SBOM Management
SBOM requirements appear across multiple regulations—the CRA, FDA guidance, and emerging requirements in other sectors. This makes supply chain transparency a high-leverage investment that addresses multiple compliance requirements simultaneously.
The business case extends beyond compliance. Companies with comprehensive SBOM capabilities can respond faster to supply chain vulnerabilities, reduce incident response costs, and demonstrate superior risk management to customers and partners. The key is implementing automated SBOM generation and continuous component monitoring rather than treating it as a one-time documentation exercise.
Vulnerability Management Excellence
Both the CRA’s 24-hour reporting requirement and the FDA’s lifecycle security obligations demand sophisticated vulnerability management capabilities. Companies that excel in this area gain competitive advantages that extend far beyond compliance.
Proactive vulnerability management reduces breach costs significantly—studies show comprehensive vulnerability management programs can reduce incident costs by millions of dollars. Research indicates that the average cost of a data breach reached $4.88 million in 2024, according to IBM’s Cost of a Data Breach Report. More importantly, companies known for rapid, transparent vulnerability response build trust with customers and partners that translates into business growth.
The implementation challenge is building systems that can automatically detect, assess, and respond to vulnerabilities across complex product portfolios. This requires integration between threat intelligence, asset management, and incident response processes.
Secure Development as Competitive Advantage
The CRA’s Secure-by-Design requirements and the FDA’s lifecycle approach both emphasize building security into products from the ground up. Companies that master secure development practices don’t just achieve compliance—they build products that customers trust and competitors struggle to match.
Key elements include integrated threat modeling, secure coding standards, and security testing throughout the development lifecycle. The goal isn’t just to pass security audits but to build products that are inherently more resilient and trustworthy.
The Benefits of Proactive Product Compliance
The most successful product leaders are discovering that proactive product compliance creates business value that far exceeds the investment required.
Competitive Differentiation Through Security
In increasingly security-conscious markets, products with built-in security capabilities command premium pricing and win more procurement decisions. This trend is particularly pronounced in healthcare, where RunSafe Security’s 2025 Medical Device Cybersecurity Index found that 60% of healthcare organizations prioritize built-in cybersecurity protections when selecting vendors, with 79% willing to pay a premium for devices with advanced runtime protection.
Security-first product positioning also builds long-term customer relationships. Companies that can demonstrate transparent security practices and rapid vulnerability response develop customer loyalty that extends beyond individual product transactions.
Operational Excellence and Risk Reduction
Secure-by-Design development practices reduce technical debt by preventing security issues rather than retrofitting solutions. This approach typically results in lower long-term development and maintenance costs, even accounting for upfront security investments.
Good security practices also streamline regulatory audits and compliance verification. Companies with mature security programs spend less time and resources on compliance activities because their standard practices already meet or exceed regulatory requirements.
Financial Returns and Investment Attraction
The financial benefits of proactive security extend beyond cost reduction. Healthcare organizations demonstrate this market reality clearly, as seen in RunSafe’s 2025 Medical Device Cybersecurity Index. 79% of healthcare buyers are willing to pay a premium for devices with advanced runtime protection, with 41% willing to pay up to 15% more for enhanced security. Additionally, 83% of healthcare organizations now integrate cybersecurity standards directly into their RFPs, while 46% have declined to purchase medical devices due to cybersecurity concerns.

Risk reduction creates additional financial value through lower incident response costs, reduced legal exposure, and improved cyber insurance rates. Companies with strong security programs often achieve significantly lower insurance premiums and better coverage terms. The documented financial impact of attacks like WannaCry, which cost the NHS £92 million, demonstrates that prevention is far more cost-effective than recovery.
What’s Next: Preparing for the Evolving Landscape
The regulatory landscape will continue to evolve, with several emerging trends that product leaders should monitor and prepare for.
- AI and machine learning governance represent the next frontier of product regulation. As AI capabilities become embedded in more products, expect new requirements for AI security, transparency, and accountability.
- Quantum-safe cryptography is another emerging area. As quantum computing capabilities advance, current cryptographic standards will become vulnerable, creating new requirements for post-quantum security measures.
- Cross-border data flow regulations continue to evolve, with new privacy and data localization requirements affecting how products handle and store user data.
Strategic Recommendations for Product Leaders
Based on the regulatory trends and business opportunities outlined above, several strategic recommendations emerge for product leaders navigating this complex landscape:
1. Invest heavily in automation capabilities
Manual compliance processes are unsustainable given the complexity and pace of regulatory change. Companies that build automated compliance capabilities will have significant advantages over competitors still relying on manual processes for monitoring, reporting, and verification.
2. Build strategic security partnerships
Few companies have all the expertise needed to excel across the full spectrum of security and compliance requirements. Strategic partnerships with specialized security vendors can provide access to expertise and capabilities that would be expensive to develop internally while accelerating time-to-market for compliant products.
3. Focus on security solutions that eliminate entire vulnerability classes
Rather than playing defense against individual threats, prioritize technologies that can eliminate broad categories of vulnerabilities. Runtime protection solutions that prevent exploitation at the device level represent this approach—they provide comprehensive protection without requiring constant updates or patches. This strategy significantly reduces risk while simplifying compliance management across product portfolios.
4. Stay informed about regulatory developments through structured processes
The regulatory landscape continues to evolve rapidly, and companies that can anticipate changes rather than just react to them will maintain competitive advantages. Establish dedicated resources for monitoring regulatory trends and translating them into product development requirements.
5. Design for global compliance standards from the start
Rather than building separate compliance programs for different markets, design for the most stringent requirements across all target markets. This approach reduces complexity while ensuring products can be sold in any market without additional compliance engineering.
Product Compliance as a Competitive Advantage
The convergence of the EU Cyber Resilience Act, FDA cybersecurity requirements, and other emerging regulations represents both the greatest challenge and the greatest opportunity facing product leaders today. The companies that view these requirements as innovation drivers rather than compliance burdens will build more secure, resilient, and successful products.
The critical insight is that waiting is not a viable strategy. The December 2027 CRA deadline and evolving FDA requirements create urgency, but companies that start building security capabilities now will discover that the benefits extend far beyond regulatory compliance.
For product leaders ready to turn cybersecurity compliance into a competitive advantage, the path forward is clear: embrace security as a core product differentiator, invest in the capabilities needed to excel at both security and compliance, and build the partnerships needed to stay ahead. The companies that make these investments today will be the market leaders of tomorrow.
Learn more about how to safeguard your code to up your product compliance. Get the white paper: “Safeguarding Code: A Comprehensive Guide to Addressing the Memory Safety Crisis.”
The post What Product Leaders Need to Know About EU CRA, FDA, and Cyber Regulations appeared first on RunSafe Security.
]]>The post What Healthcare Buyers Expect from Medical Device Manufacturers: Security Is No Longer Negotiable appeared first on RunSafe Security.
]]>The consequences reach beyond network disruptions: 75% of these incidents directly compromised patient care, with nearly half compelling organizations to revert to manual processes just to maintain operations. When a cyberattack necessitates transferring patients to other facilities, which occurred in 24% of cases, the situation creates serious medical emergencies.
The convergence of IT and OT security is putting medical devices at the center of cybersecurity strategy, the report shows. Healthcare organizations can no longer protect medical devices in isolation. Securing patient-critical systems now requires defending the entire interconnected ecosystem.
Because of this, we’re seeing a changing relationship between healthcare providers and medical device manufacturers. The findings of the 2025 Index show that for healthcare buyers, cybersecurity is becoming a gatekeeper to market access.
Medical Device Cybersecurity: From Nice-to-Have to Must-Have
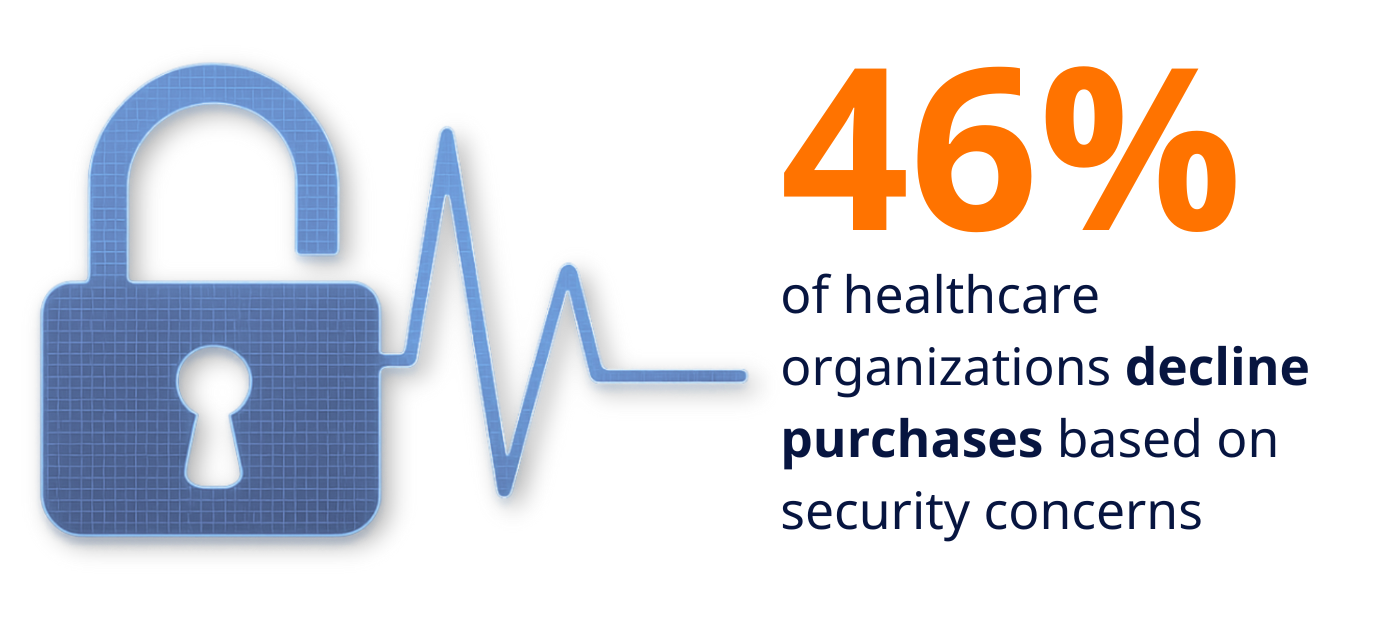
Healthcare buyers have spoken with their wallets and their purchasing decisions. The data reveals a dramatic transformation in how medical devices are evaluated and purchased:
- 83% of healthcare organizations now integrate cybersecurity standards directly into their RFPs
- 46% have declined to purchase medical devices due to cybersecurity concerns
- 79% are willing to pay a premium for devices with advanced runtime protection
When nearly half of potential buyers are prepared to walk away from purchases over security issues, manufacturers can no longer treat cybersecurity as an afterthought. This willingness to reject products represents a fundamental shift from traditional procurement practices where functionality and cost dominated decision-making.
Healthcare leaders have moved from asking “What can this device do?” to “How secure is this device?” The organizations that have experienced attacks understand that the most feature-rich device in the world can become a liability if it is not secure.
The Trust Equation Has Changed
The ripple effects extend beyond individual purchasing decisions. Nearly a third (32%) of healthcare organizations report that security incidents have affected their trust in specific vendors, requiring additional security verification from previously trusted partners.
Those manufacturers must now prove their security credentials to maintain existing relationships, not just win new ones. Healthcare organizations are conducting security audits of their entire vendor ecosystem, reassessing partnerships through the lens of cybersecurity risk rather than traditional performance metrics.
What Healthcare Leaders Want: Transparency and Built-In Defense
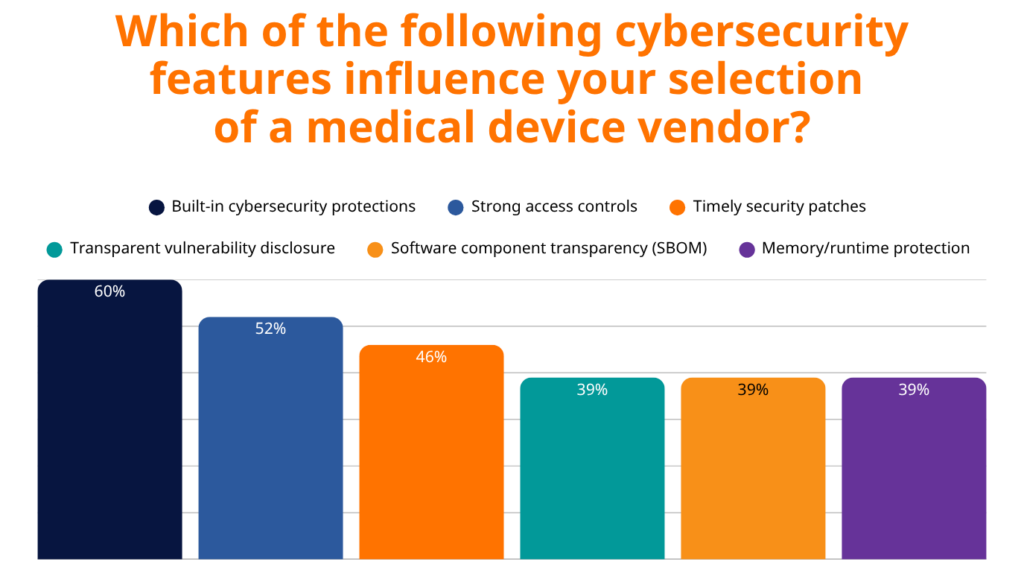
The survey data reveals clear expectations from healthcare buyers. They are not asking for band-aid solutions but want security baked into the device’s DNA from day one.
1. Software Bills of Materials (SBOMs) Are Non-Negotiable
78% of organizations consider SBOMs essential or important in procurement decisions. This extends beyond regulatory compliance to practical vulnerability management. The FDA now requires SBOMs in premarket submissions, and healthcare buyers understand that knowing device components constitutes fundamental ongoing security. Transparency becomes a competitive necessity.
However, generating comprehensive and accurate SBOMs remains challenging for many embedded medical devices written in C/C++. Traditional binary analysis SBOM solutions often produce excessive false positives and overlook critical components, such as static libraries. Healthcare organizations increasingly seek vendors who can provide build-time SBOM solutions that accurately capture only the components present in the final device.
2. Built-In Security Over Bolt-On Solutions
60% of healthcare organizations prioritize built-in cybersecurity protections when selecting vendors. This preference reflects hard-learned lessons where retrofitted security measures proved insufficient against sophisticated attacks.
Runtime protection technologies are gaining traction, with 36% of organizations actively seeking devices with these capabilities, while another 38% are aware of these technologies but don’t yet require them. This suggests the market is evolving rapidly from early adoption to mainstream expectation.
3. Premium Pricing for Premium Protection
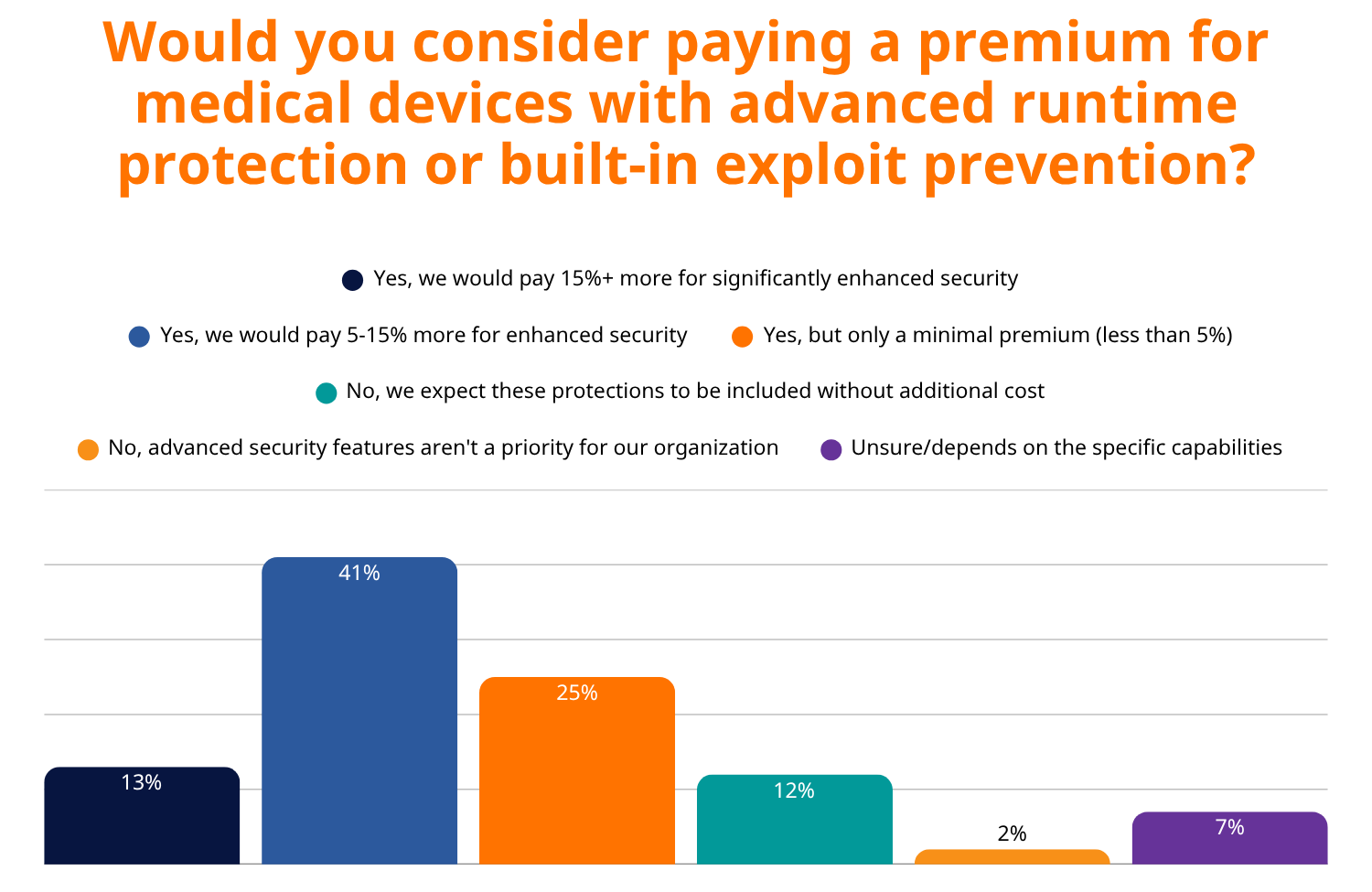
Perhaps most telling is healthcare buyers’ willingness to invest in advanced security. 79% of buyers would pay a premium for devices with advanced runtime protection, with 41% willing to pay up to 15% more for enhanced security.
This demonstrates that healthcare leaders have moved beyond viewing cybersecurity as a checkbox requirement to understanding it as a complex, resource-intensive discipline that requires ongoing investment. They recognize the documented financial impact of attacks like WannaCry, which cost the NHS £92 million, and understand that prevention is far more cost-effective than recovery.
The Regulatory Landscape Is Amplifying Demands
73% of healthcare organizations report that new FDA cybersecurity guidance and EU regulations are already influencing their procurement decisions. The regulatory environment is creating a cascading effect where compliance requirements drive purchasing behavior, making cybersecurity not just a competitive advantage but a regulatory necessity for market access.
Key regulatory drivers include:
- FDA’s Section 524B mandates cybersecurity information in submissions for network-capable devices
- The EU’s Cyber Resilience Act imposes mandatory cybersecurity requirements on connected products
- The NIS2 Directive explicitly targets medical device manufacturers with cybersecurity compliance requirements
The Financial Reality: Budgets Are Rising, Confidence Is Lagging
Healthcare organizations are responding with their wallets—75% increased their medical device and OT security budgets over the past 12 months. However, only 17% feel extremely confident in their ability to detect and contain attacks on medical devices.
This gap between spending and confidence suggests that simply throwing money at the problem isn’t enough. It highlights the critical need for solutions that work within the unique constraints of medical devices that often can’t be easily patched, may run on legacy operating systems, and require 24/7 availability for patient care.
What This Means for Medical Device Manufacturers
The transformation of healthcare cybersecurity expectations presents both opportunities and imperatives for manufacturers:
Opportunities:
- Economic foundation for security innovation: With buyers willing to pay premium prices, manufacturers now have the financial justification to invest heavily in security features
- Competitive differentiation: Manufacturers who embrace transparency and built-in security can capture market share from competitors who lag behind
- Regulatory compliance as market access: Meeting new cybersecurity requirements extends beyond avoiding penalties to gaining access to buyers who will not consider non-compliant products
Imperatives:
- Secure by Design: Retrofitting security is no longer acceptable; it must be integrated from the ground up
- Transparency through SBOMs: Accurate, comprehensive Software Bills of Materials are becoming table stakes
- Runtime protection: Advanced security features like runtime exploit prevention are rapidly moving from nice-to-have to must-have
- Ongoing vulnerability management: Manufacturers must demonstrate proactive approaches to identifying and addressing security issues
The Path Forward: Prevention Over Reaction
The data in the 2025 Index makes it clear that healthcare is moving from reactive cybersecurity to proactive prevention. The organizations that have experienced attacks understand that the most sophisticated incident response plan is no substitute for preventing the attack in the first place.
The healthcare industry is essentially conducting risk-based purchasing decisions, weighing the cost of advanced security features against the potential catastrophic consequences of device vulnerabilities. And increasingly, they’re concluding that the cost of prevention is far lower than the cost of compromise.
For medical device manufacturers, this transformation represents a fundamental shift in market dynamics. Those who embrace security transparency, integrate runtime protections, and demonstrate proactive vulnerability management will find themselves positioned to capture market share in an industry increasingly willing to invest in advanced protection.
Conversely, manufacturers who treat cybersecurity as an afterthought risk not only regulatory rejection but also exclusion from a market that has fundamentally redefined what constitutes an acceptable medical device.
The convergence of IT and OT security, combined with unprecedented regulatory oversight and buyer sophistication, has created a new competitive landscape where cybersecurity excellence serves as the foundation upon which trust, market access, and patient safety are built.
Key Takeaways for Medical Device Manufacturers
- Cybersecurity is now a gatekeeper to market access—nearly half of healthcare buyers will reject products over security concerns
- Built-in security trumps bolt-on solutions—60% of buyers prioritize integrated cybersecurity protections
- Transparency through SBOMs is non-negotiable—78% consider them essential or important in procurement decisions
- Premium pricing is acceptable for premium protection—79% of buyers will pay more for advanced security features
- Regulatory compliance drives purchasing behavior—73% report that new cybersecurity guidance influences procurement decisions
The message from healthcare leaders is clear: security isn’t negotiable anymore. It’s the price of admission to a market.
Download the full 2025 Medical Device Cybersecurity Index for all the key takeaways and findings.
Learn more about how RunSafe Security helps medical device manufacturers integrate security with our Protect solution and unique SBOM generator.
The post What Healthcare Buyers Expect from Medical Device Manufacturers: Security Is No Longer Negotiable appeared first on RunSafe Security.
]]>The post Is Regulatory Harmonization on the Horizon? The Medical Devices Cybersecurity Landscape in the EU and the US appeared first on RunSafe Security.
]]>RunSafe Security and Critical Software are partners in delivering comprehensive safety and security solutions for critical sectors in Europe and the US.
Imagine modern healthcare services without medical devices. You can’t? Neither can we. Medical devices perform a vital role in the patient experience, from diagnosis to treatment to follow-up. Advances in tech have enhanced these devices and, in turn, have improved patient outcomes. Personalized treatment plans using data gathered from wearables; real-time monitoring of patients’ conditions allowing healthcare professionals to intervene in a timely fashion; AI-powered surgical systems assisting surgeons during complex operations – all of these have revolutionized the way patients are treated.
But they have also widened the threat horizon for patients. The ever-increasing range of cyber threats pose serious reputational risks to manufacturers and could mean the difference between life and death for patients. But to combat these threats, different jurisdictions have implemented their own medical device cybersecurity standards, creating friction for manufacturers operating in various markets.
From the European Union’s Medical Devices Regulation (MDR) to the United States’ Foods & Drug Administration (FDA), medical device manufacturers need to ensure their devices comply with cybersecurity standards outlined in each jurisdiction. But is this getting easier or more complex in an ever-more complex threat environment?
Medical Device Cybersecurity in the EU
The EU’s MDR outlines clear rules with which medical device manufacturers must comply in the domain of cybersecurity, particularly with regards to following risk management practices aligned with ISO 31010 and ISO 14971.
Post-market surveillance is critical to this: the manufacturer is responsible for keeping track of any cybersecurity vulnerabilities that present themselves in their devices and must work to rectify these once identified.
Harmonization of Medical Device Standards and Regulations
Yet harmonization is already occurring between the two regulators, reducing friction and making manufacturers’ lives easier. ISO 13485 is adhered to by both the MDR within the EU and the US FDA, aligning quality management system regulations between the two markets. This is in addition to the most recent update of harmonized standards made by the EU in March 2024, this being the next step in the bloc’s efforts to align its standards with those applicable globally.
The International Medical Devices Regulators Forum (IMDRF) plays a role in reducing barriers for manufacturers operating in the EU and US, with shared guidance on clinical evaluation and post-market surveillance making it easier for manufacturers to distribute, monitor, and “sense-check” their devices, ensuring compliance with a harmonized set of standards. This is integral in the cybersecurity domain, ensuring protection against evolving threats in whichever market the devices are placed in.
What Does This Mean for Cybersecurity?
Both the EU’s MDR and the FDA’s regulations require a risk-based approach, ensuring that residual risks are assessed and managed throughout the device’s lifecycle. In terms of cybersecurity, this demands extensive risk management documentation. Similarly, Secure by Design has been implemented in both the EU and the US: the MDR encourages manufacturers to implement cybersecurity measures from the earliest stage of the design process, while the FDA requires Secure Product Development Frameworks (SPDFs) be followed from early design to product release.
There is still much work to do, however. Since 2010, the number of cybersecurity incidents in the EU and the US has increased. From 2021 to 2023, there were over 215 publicly reported cybersecurity incidents relating to medical devices in the EU. In the US, it is estimated that over 53% of devices on the market possess critical cyber vulnerabilities. A 2024 report from Censys found that there are “14,004 unique IP addresses exposing healthcare devices and data systems connected to potentially sensitive medical information on the public internet. These exposures greatly raise the risk of unauthorized access and exploitation.”
The Future of Cybersecurity Regulatory Alignment
Regulatory alignment is heading in the right direction, but as we have seen, there is still more work to be done. While harmonization is progressing, critical vulnerabilities remain in copious amounts of medical devices and healthcare products in the market, which opportunistic hackers and hostile actors can take advantage of.
Want to discover more about the pivotal role of cybersecurity in medical devices? Catch up with Critical Software and RunSafe Security’s recent webinar featuring Afonso Neto from Critical Software and Doug Britton from RunSafe Security, who outlined some of the most pressing cybersecurity aspects underpinning medical device regulations in the EU and USA. Watch the webinar here.
The post Is Regulatory Harmonization on the Horizon? The Medical Devices Cybersecurity Landscape in the EU and the US appeared first on RunSafe Security.
]]>
