The post Meeting ICS Cybersecurity Standards With RunSafe appeared first on RunSafe Security.
]]>As software supply chains grow in complexity and ICS devices take on more digital functionality, operators face risk from vulnerabilities buried deep within firmware, dependencies, and proprietary code. Strengthening security and demonstrating compliance begins with improving the integrity, transparency, and resilience of that software.
RunSafe helps industrial organizations achieve this by hardening code against exploitation, increasing visibility into software components through build-time Software Bill of Materials (SBOM) generation, and extending protection to systems that can’t easily be patched or rebuilt.
These capabilities align directly with the technical controls required across major ICS cybersecurity standards, helping operators close gaps in their security posture.
Listen to the Audio Overview
Key ICS Cybersecurity Standards RunSafe Supports
| ICS Standard / Regulation | Relevant Requirements | RunSafe Capability That Supports It |
|---|---|---|
| IEC 62443 (including SR 3.4: Software & Information Integrity) | Software integrity, tamper prevention, secure component management | Protect: Runtime exploit prevention stops unauthorized code execution even when vulnerabilities exist. Identify: Build-time SBOMs document components for integrity verification. |
| NIST 800-82 (Guide to ICS Security) | System integrity (SI), configuration management (CM), continuous monitoring (RA/CA), incident response | Identify: SBOMs support configuration management and vulnerability assessment. Protect: Runtime exploit mitigation enhances system integrity. Monitor: Crash analytics & exploit detection support continuous monitoring. |
| NIST Risk Management Framework (RMF) | Ongoing assessment, vulnerability management, security controls validation | Identify: SBOMs accelerate risk assessment and control verification. Monitor: Evidence and telemetry support ongoing authorization and assessment. |
| NERC CIP | Software integrity, vulnerability assessments, incident reporting, BES Cyber System security | Identify: SBOMs shorten vulnerability assessment cycles. Protect: Hardens embedded systems to maintain operational integrity. Monitor: Provides supporting data for CIP-008 incident response. |
| EU Cyber Resilience Act (CRA) | Mandatory SBOMs, secure-by-design software, vulnerability handling, lifecycle security | Identify: Build-time SBOM generation identifying all components, including for C/C++ builds. Protect: Code hardening reduces exploitability for both known and unknown vulnerabilities. |
| U.S. Federal SBOM Mandates (NTIA, DHS, DoD, FDA) | Accurate, complete, machine-readable SBOMs; traceability; vulnerability identification | Identify: Comprehensive CycloneDX SBOMs generated at build-time that support all mandatory NTIA fields. |
| UK Cybersecurity and Resilience Bill | Supply chain assurance, software integrity, rapid incident reporting | Identify: SBOMs enable supply chain verification and vulnerability tracking. Protect: Code hardening reduces exploitability for both known and unknown vulnerabilities. |
| ISA/IEC 62443-4-1 (Secure Development Lifecycle) | Component inventory, secure build processes, threat mitigation | Identify: SBOM visibility integrated into SDLC and build processes. Protect: Mitigates memory-based vulnerabilities for devices in the field even before patches are available. |
IEC 62443 Security Requirements
IEC 62443 defines security levels (SL-1 to SL-4) to counter cyber threats to ICS systems. Security Requirement 3.4 requires mechanisms to ensure software and information integrity by detecting and preventing unauthorized modifications, which is essential for defending against zero-day exploits.
RunSafe Security supports this with runtime code protection and automated defenses that maintain software trustworthiness in ICS devices, aligning with these IEC 62443 integrity requirements.
NIST 800-82 Control Families
NIST SP 800-82 is a specialized guidance document focused on Industrial Control Systems (ICS) and Operational Technology (OT) environments. It defines 19 control families tailored to these unique contexts, addressing operational, technical, and management controls relevant to ICS security.
RunSafe’s Protect solution assists in meeting NIST standards by hardening software across firmware, applications, and operating systems to reduce vulnerabilities, especially memory-based and zero-day threats. This aligns with minimizing risks outlined in NIST 800-82, such as unauthorized modifications, malware infections, and system exploitation.
NERC CIP standards
NERC CIP applies to bulk electric systems and mandates stringent access control, security monitoring, and incident response to protect critical grid infrastructure.
RunSafe’s automated software hardening strengthens embedded software against vulnerabilities, including zero-day attacks, helping to meet NERC CIP mandates for cybersecurity system management and reducing the attack surface of BES Cyber Systems.
EU Cyber Resilience Act
The EU Cyber Resilience Act imposes mandatory cybersecurity requirements on manufacturers placing products with digital elements into the European market. The regulation requires comprehensive SBOM documentation, vulnerability disclosure processes, and Security by Design principles throughout the product lifecycle.
RunSafe empowers organizations to meet EU CRA requirements through automated build-time SBOM generation, embedded software hardening, and proactive vulnerability identification.
UK’s Cybersecurity and Resilience Bill
The UK’s proposed legislation extends cybersecurity obligations across critical national infrastructure sectors. The bill emphasizes supply chain security and mandates incident reporting within strict timeframes, creating accountability for operators and vendors.
RunSafe Security supports compliance with the UK Cybersecurity and Resilience Bill by providing embedded software security designed specifically for ICS systems and software supply chain transparency through build-time SBOM generation.
How RunSafe Hardens Code & Strengthens the Software Supply Chain to Meet ICS Security Standards
RunSafe improves ICS security posture by providing:
- Build-Time SBOM Generation: Provides complete visibility into software components and software supply chain risk, especially for C/C++ and embedded toolchains.
- Runtime Code Protection: Protects ICS devices in the field, even before patches are available, by preventing the exploitation of memory-based vulnerabilities, including zero-day exploits.
Together, these capabilities directly support key ICS cybersecurity requirements.
The Industrial Control System Software Risk Landscape

ICS cybersecurity risks increasingly stem from software complexity. PLCs, HMIs, sensors, gateways, and controllers rely on layered stacks of compiled code, RTOS kernels, communication libraries, protocol implementations, and third-party components. As this software ecosystem expands, several categories of risk emerge:
1. Vulnerabilities in Proprietary and Third-Party Components
Industrial devices often incorporate dozens or hundreds of software elements, both internally developed and externally sourced. Many of these components lack update mechanisms or clear lifecycle management. When vulnerabilities are disclosed, asset owners frequently lack the visibility needed to determine whether their systems are exposed.
2. Memory Safety Issues as a Persistent ICS Threat
Memory safety remains one of the most common contributors to ICS vulnerabilities. Buffer overflows, use-after-free flaws, and out-of-bounds writes still account for a significant portion of CVEs in industrial and embedded software. These weaknesses persist in critical infrastructure because:
- Many devices use older programming languages (e.g., C/C++)
- Patching may be infeasible due to uptime requirements
- Legacy firmware often cannot be rebuilt or re-verified
- Third-party components introduce memory safety risks through the software supply chain.
Andy Kling, VP of Cybersecurity at Schneider Electric, a major player in the ICS/OT space, found that “memory safety was easily the largest percentage of recorded security issues that we had.” 94% of these weaknesses come from third-party components.
While memory safety is not the only category of ICS risk, it remains one of the most damaging, often enabling remote code execution or multi-stage exploit chains.
3. Software Supply Chain Blind Spots
Software supply chain cyberattacks frequently target the software dependencies and build environments behind industrial products. Without reliable SBOMs, operators cannot:
- Determine which libraries exist in a given binary
- Rapidly assess exposure to new vulnerabilities
- Confidently evaluate vendor-supplied code or firmware
The lack of software transparency turns compliance into guesswork and slows incident response.
4. Operational Constraints That Block Traditional Security Measures
Industrial environments face major deployment challenges:
- Air-gapped or intermittently connected networks
- Decades-old firmware with no vendor support
- Real-time performance requirements that limit scanning or patching
- Multi-vendor PLC fleets with inconsistent update workflows
These realities make it difficult to rely solely on patch management, network segmentation, or perimeter defenses.
5. Physical and Operational Consequences
Because ICS software interacts directly with physical equipment, software vulnerabilities can lead to:
- Manipulation of process parameters
- Shutdown of production lines
- Damage to equipment or the environment
- Safety incidents impacting human operators
Software risk in ICS is therefore both digital and physical, with potentially severe outcomes.
Three Steps to Deploy RunSafe in Existing ICS Security Programs
Given the depth of software risk in modern ICS environments, organizations need solutions that both reduce exploitability and produce the evidence required for rising compliance standards.
RunSafe delivers this by integrating directly into existing development and maintenance workflows, making it possible to improve security posture without operational disruption.
1. Integrate & Automate SBOM Generation at Build Time
Begin by embedding RunSafe’s SBOM generation directly into your CI/CD pipeline or offline build environment. Whether you’re working with embedded Linux, Yocto/Buildroot builds, or legacy RTOS toolchains, RunSafe’s Identify capability produces CycloneDX-compliant SBOMs and supports all mandatory NTIA fields.
You’ll gain full component visibility—down to libraries, files, and versions, including proprietary components—so you can quickly assess exposure, audit supplier code, enforce license policy, and meet SBOM-mandate requirements for ICS environments.
2. Apply Binary Hardening and Runtime Protection
Protecting your software with RunSafe Protect is as easy as installing the packages from our repositories and making a one-line change to your build environment. Once installed, you can automatically integrate Protect into your existing build process.
RunSafe Protect hardens compiled binaries against memory-based exploits and zero-day attacks by applying Load-time Function Randomization (LFR). Even legacy PLC firmware, vendor-supplied binaries, or devices in air-gapped networks can benefit from exploit mitigation. Because the protection works independently of patch status, you’re reducing risk proactively while maintaining operational continuity.
3. Monitor Protected Devices
Deploy RunSafe’s Monitor capability across your hardened device fleet to capture crash indicators, detect unusual behavior patterns, and differentiate between benign failures and potential exploit attempts.
Next Steps to Secure Your ICS Environment
Securing industrial control systems requires more than perimeter defenses or periodic patch cycles. It demands protections that operate inside the software itself—across legacy devices, modern embedded platforms, and complex software supply chains.
RunSafe provides that foundation by hardening binaries against exploitation, generating accurate SBOMs at build time, and delivering operational insight through lightweight monitoring. Together, these capabilities give ICS operators a practical path to strengthen system integrity, reduce exploitability, and demonstrate compliance with the world’s most important cybersecurity standards.
With the right protections applied directly to the software running your critical processes, resilience becomes achievable rather than aspirational.
Request a consultation to get started with RunSafe or to assess your embedded software security and risk reduction opportunities.
FAQs About RunSafe and ICS Compliance
Yes. RunSafe hardens compiled binaries at runtime to let operators secure decades-old PLCs, RTUs, and embedded controllers even when patches are unavailable or unable to be applied.
Does RunSafe impact real-time performance or PLC scan cycles?
RunSafe takes an agentless approach to have very low impact and has been deployed in many resource-constrained environments successfully.
Can RunSafe be deployed in completely air-gapped ICS environments?
Yes. RunSafe supports offline licensing and local-only operations. All analysis, hardening, and SBOM generation can be performed inside secure, disconnected networks. This is particularly valuable for ICS environments with strict isolation requirements or regulatory prohibitions against cloud connectivity.
How does RunSafe help with IEC 62443 SR 3.4 and software integrity requirements?
IEC 62443 SR 3.4 requires mechanisms to prevent unauthorized modification or execution of software components. RunSafe delivers this by making memory-based exploits—including zero days—non-exploitable. Even if a vulnerability exists, exploit attempts fail, helping operators maintain software integrity even on unpatched or legacy systems.
Does RunSafe support NIST 800-82 and NERC CIP incident response and integrity controls?
Yes. RunSafe contributes to several core NIST and NERC CIP requirements:
- System and information integrity: Prevents unauthorized code execution by blocking exploit chains.
- Configuration and vulnerability management: SBOMs accelerate identification of impacted assets.
- Continuous monitoring: Crash analytics and exploit indicators support incident detection and reporting.
This helps operators produce clear, evidence-backed compliance documentation.
How does RunSafe support SBOM requirements in the EU Cyber Resilience Act and U.S. federal mandates?
RunSafe generates build-time SBOMs, capturing every component, including low-level C/C++ libraries and embedded dependencies often missed by scanning tools. RunSafe’s Identify capability produces CycloneDX-compliant SBOMs and supports all mandatory NTIA fields.
Can RunSafe help reduce zero-day exploitability in ICS or embedded software?
Yes. RunSafe’s patented Load-time Function Randomization defends software from memory-based zero days by altering the memory layout of an application each time it runs. This prevents attackers from leveraging memory-based vulnerabilities, such as buffer overflows, to attack a device or gain remote control.
How does RunSafe differ from network-based ICS security tools?
Network tools (IDS, DPI, segmentation) detect or contain attacks, but they cannot prevent exploitation inside the device. RunSafe operates within the software itself, transforming binaries so they cannot be exploited even if the attacker reaches the device or bypasses perimeter defenses. It complements—not replaces—existing ICS security layers by addressing the root of software exploitability.
What types of ICS platforms and RTOS environments does RunSafe support?
RunSafe supports a broad range of ICS platforms, including: VxWorks, QNX, Yocto, Buildroot, Linux, Bare Metal, and more. View a full list of integrations and supported platforms here.
The post Meeting ICS Cybersecurity Standards With RunSafe appeared first on RunSafe Security.
]]>The post Defending the Factory Floor: How to Outsmart Attackers in Smart Manufacturing appeared first on RunSafe Security.
]]>That’s the question host Paul Ducklin explored with Joseph M. Saunders, CEO and Founder of RunSafe Security, in an episode of Exploited: The Cyber Truth.
From the limitations of traditional security models to the growing importance of software quality, this conversation revealed why the cybersecurity playbook for industrial automation needs a re-write for today’s threats.
The Challenge of Smart Manufacturing: Complexity Meets Connectivity
Modern factories are no longer isolated networks of robots and sensors. They’re deeply connected ecosystems, merging OT (Operational Technology) and IT, often with cloud integration and industrial IoT devices.
As Joe put it, “Connected devices bring productivity gains, but also new levels of security consideration.”
That connectivity has blurred the once-clear boundaries between factory floor systems and IT networks. Attackers can now exploit weak spots at every layer—from programmable logic controllers (PLCs) to human-machine interfaces (HMIs), SCADA systems, and even the cloud.
Why the Purdue Model Falls Short
The Purdue Security Model, long a foundation for industrial security, assumes clear segmentation between these layers. But in an era where a single sensor might communicate via Bluetooth, Wi-Fi, or cellular, those boundaries collapse.
Attackers no longer need “write access” to cause harm. Even read-only access—like viewing operational data or production schedules—can provide immense competitive or geopolitical advantage.
Example: Knowing how much of a certain alloy a manufacturer has in stock could reveal supply chain bottlenecks or production delays.
Compliance vs. Security: A Distinction that Matters
Too many organizations still approach cybersecurity as a checkbox exercise. Standards like IEC 62443, developed by the ISA and IEC, help guide secure industrial automation practices—but they’re only as good as the commitment behind them.
Joe cautioned that “checkbox compliance” misses the point. Security should be viewed as an extension of software quality and operational excellence.
Secure by Design Starts in Development
Building security into the software development lifecycle (SDLC)—from coding and testing to patching—is essential. Companies that automate and embed these processes don’t just produce safer software; they create better products, faster.
Extending the Life of Legacy Systems
Many industrial environments still rely on legacy systems with equipment that can’t easily be replaced or updated. These older devices, often running outdated firmware, represent some of the most vulnerable points in a factory’s network.
Memory Safety to the Rescue
Joe explained how memory safety protections can extend the secure life of legacy systems without requiring new software agents or hardware upgrades.
RunSafe’s Load-Time Function Randomization provides runtime protection that prevents exploitation even when patches aren’t available—adding security without disrupting operations.
“You can extend the life of legacy systems by applying memory safety protection in a way that doesn’t add software or slow them down,” Joe said.
That’s not just risk mitigation—it’s cost savings, uptime assurance, and long-term resilience.
Seeing the Whole Picture: From Software Supply Chain to Factory Floor
Securing smart factories also requires a focus on understanding the entire software supply chain. To protect devices, you need to know what software is built into each one.
Manufacturers, suppliers, and customers each play a role in ensuring the integrity of the products they build and deploy.
Joe recommends evaluating partners and suppliers based on:
- Governance and internal security policies
- Compliance with standards like IEC 62443
- Awareness of known threat actors and their tactics
- Transparency in Software Bill of Materials (SBOMs)
- Differentiation through resilient product design
RunSafe’s recent Medical Device Industry Report showed similar trends. Organizations are starting to reject insecure products altogether, even when they meet performance requirements. That mindset shift is now reaching industrial automation.
From “Good Enough” to Resilient by Design
The conversation ultimately returned to a core truth: Security isn’t about perfection—it’s about resilience.
When software is developed securely, vulnerabilities are reduced. When runtime protections are added, attackers are denied an easy path to exploit. And when organizations collaborate across the software supply chain, entire industries become more secure.
“Security isn’t a checkbox—it’s a reflection of quality,” Joe reminded listeners.
Take the Next Step: Secure Your Industrial Systems
RunSafe Security protects embedded software across critical infrastructure, delivering automated vulnerability identification and software hardening to defend the software supply chain and critical industrial systems without compromising performance or requiring code rewrites.
Learn more about how we do it in this case study: “Vertiv Enhances Critical Infrastructure Security for Embedded Systems with RunSafe Integration.”
The post Defending the Factory Floor: How to Outsmart Attackers in Smart Manufacturing appeared first on RunSafe Security.
]]>The post Fixing OT Security: Why Memory Safety and Supply Chain Visibility Matter More Than Ever appeared first on RunSafe Security.
]]>
What Makes OT Security So Hard to Fix?
Unlike traditional IT, OT systems power critical infrastructure like energy grids, water management, manufacturing floors, and more. These devices often run on low-powered hardware with long lifespans and were never designed for modern connectivity. They were secured by locked doors, not firewalls.
Fast forward to today, and these devices are increasingly connected to the internet—and exposed.
Memory Safety: Still the Achilles’ Heel
Many vulnerabilities in common OT products are caused by buffer overflows or memory corruption flaws. While systemic, these vulnerabilities can be proactively addressed with memory safety protections.
“If you can eliminate entire classes of vulnerabilities before software hits the field, you don’t need to play whack-a-mole with patches,” says Saunders.
RunSafe’s approach focuses on preventing exploitation at the binary level, effectively making vulnerabilities non-exploitable without requiring post-deployment patching.
The Growing Complexity of the OT Software Supply Chain
Even the simplest industrial device could include thousands of open-source software components. Without visibility into the Software Bill of Materials (SBOM), organizations are left guessing about what’s inside.
“If a vendor can’t tell you what’s in their product, chances are, they don’t know either,” says Saunders.
Knowing your software’s components—and their vulnerabilities—is critical for compliance. It’s also critical for managing risk across the supply chain, identifying attack surfaces, and making smart, prioritized decisions.
Why Patching Alone Isn’t Enough
Patching in OT isn’t like clicking “update” on your phone. It can require physical access to remote locations and months of planning. Worse, many vulnerabilities go unpatched for 180+ days, leaving critical infrastructure exposed for far too long.
This makes proactive protection methods—like RunSafe’s memory randomization techniques and runtime protection—essential tools in a modern OT defense strategy.
What Should Product Manufacturers and Asset Owners Do Now?
Joe Saunders outlines a simple yet powerful framework:
For OT Product Manufacturers:
- Generate a complete SBOM for each product.
- Identify known vulnerabilities.
- Prioritize fixes based on impact and exploitability.
- Adopt Secure by Design tools that eliminate entire classes of vulnerabilities at build time.
For Asset Owners:
- Request SBOMs from all vendors.
- Analyze vulnerabilities across all systems—from HVAC to power to physical access.
- Demand security transparency and memory safety protections from suppliers.
This shift toward accountability and visibility reduces operational costs and futureproofs infrastructure.
Regulation, Risk, and the Path Forward
Fixing OT security won’t happen with checklists and wishful thinking. It’ll take:
- Regulation that incentivizes change, like the Cyber Resilience Act
- Automation that scales patchless security
- Shared responsibility across the ecosystem
“The real question isn’t whether we can fix OT security,” Saunders concludes. “It’s whether we want to—and who’s willing to lead the charge.”
The post Fixing OT Security: Why Memory Safety and Supply Chain Visibility Matter More Than Ever appeared first on RunSafe Security.
]]>The post Ransomware in OT Environments: A 2025 Perspective appeared first on RunSafe Security.
]]>The numbers reflect a growing and dangerous trend of attackers shifting their focus from data-rich IT systems to mission-critical OT environments where the consequences of downtime can be catastrophic.
“Ransomware attacks are on the rise, and most discussion revolves around recovering from ransomware—either paying the ransom or hiring a recovery firm,” said Shane Fry, CTO at RunSafe Security. “Unfortunately, those approaches are just band-aids addressing the symptoms. The better approach is prevention. If an attacker can’t gain code execution on a system, they can’t run their ransomware in the first place.”
A prevention mindset is urgently needed to defend OT systems.
Ransomware’s OT Evolution
A report from Dragos found an 87% increase in ransomware attacks against industrial organizations over the past year and a 60% rise in ransomware groups affecting OT/ICS (operational technology/industrial control systems) in 2024.
OT networks were historically “air-gapped” or isolated, but the rise of Industrial IoT (IIoT) and convergence with IT systems has opened the floodgates to cyber threats. Legacy systems, outdated firmware, insecure protocols, and unpatched vulnerabilities make OT a soft target that attackers are paying more attention to.
Not only that, but changes in the geopolitical landscape are likely attributable to the rise in attacks. “With the changing geopolitical landscape and the changes in cyber priorities, it is no surprise to see an increase in attacks and reports of ransomware,” said Joe Saunders, Founder and CEO of RunSafe Security. “Attackers are testing the fault lines and seeking ransom payouts.”

Additionally, OT systems aren’t designed to be restored overnight like cloud servers and require manual resets, specialized hardware, and physical technician access. Downtime from an ICS/OT ransomware attack costs an average of $4.73 million per incident and results in public safety risks. Because of the costs and risk involved, OT organizations may be more inclined to pay a ransom to restore operations, and bad actors and threat groups are taking notice.
“We must implement straight solutions now to make critical infrastructure safe in an efficient way,” Joe said. “Otherwise, China and other adversaries will, at a time of their choosing, disrupt operations.”
Where OT Ransomware Attacks Originate
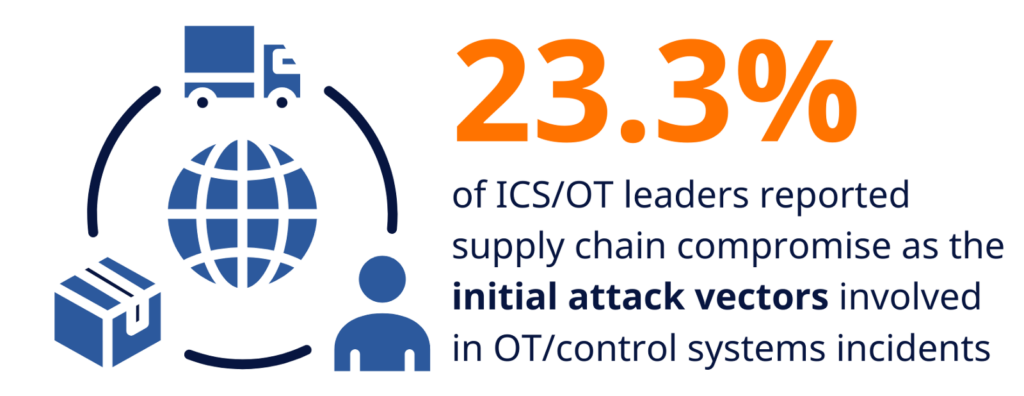
Ransomware doesn’t need to originate in OT to impact OT. If your supply chain includes IT/OT integration, third-party maintenance tools, or remote access services, your OT is exposed.
The SANS 2024 State of ICS/OT Cybersecurity report found that 20.3% of ICS/OT leaders reported supply chain compromise as the initial attack vector involved in OT/control systems incidents.
We can see this growth in a few notable ransomware incidents involving OT.
Kaseya Ransomware Attack (2021) – IT/OT Convergence Breach
In 2021, the REvil ransomware gang compromised Kaseya’s VSA remote management tool used by MSPs, which had clients across various sectors, including manufacturing and industrial facilities. It’s estimated that 200+ companies were compromised as a result. The attack is an example of how software supply chain attacks can create a domino effect for companies further down the chain, including how IT-focused supply chain tools can cascade into OT disruption through shared access.
The Colonial Pipeline Incident (2021) – Indirect OT Disruption via Ransomware
The Colonial Pipeline incident in 2021 is a good reminder to take ransomware seriously. DarkSide ransomware hit Colonial Pipeline’s IT systems. Although the OT environment wasn’t directly compromised, operations were proactively shut down due to uncertainty and risk. The incident revealed how ransomware can indirectly cripple OT via compromised IT systems that manage or monitor critical infrastructure.
Strategies for OT Ransomware Defense
The best defense against ransomware is a proactive approach that prevents attackers from ever gaining code execution on a system. Below are several measures to defend OT software.
- Network Segmentation: Isolate critical OT systems from IT networks to limit lateral movement.
- Strong Credential and Access Management: Enforce multi-factor authentication, rotate credentials, and use allowlist-based access controls.
- Regular, Offline Backups: Maintain encrypted, offline backups and test them regularly to ensure rapid recovery without paying ransoms.
- Incident Response Planning: Develop and rehearse OT-specific incident response plans, including procedures for isolation and recovery.
- Continuous Monitoring: Stay updated on indicators of compromise and integrate threat intelligence into monitoring practices.
- SBOMs and Supply Chain Security: Generating and maintaining a Software Bill of Materials (SBOM) enhances transparency, helps identify vulnerable components, and is rapidly becoming a regulatory requirement.
- OT-Specific EDR: Deploy endpoint detection and response solutions tailored for OT, minimizing operational impact while detecting malicious behaviors.
- Memory Safety and Software Hardening: Tools like RunSafe Security’s Protect proactively defends against memory-based vulnerabilities and zero-day exploits by hardening software at build time, reducing the risk of code execution by attackers.
Prevention Is the Only Real Cure
The surge in ransomware attacks on OT environments is a wake-up call for critical infrastructure operators. Relying solely on reactive measures is no longer sufficient. As Shane Fry notes, preventing initial access and code execution is the most effective way to stop ransomware before it can cause harm.
By adopting proactive, OT-specific security measures, such as memory safety hardening, software supply chain transparency, and robust incident response, organizations can build resilience and protect the systems that keep our world running.
Learn how an industrial automation leader automated software hardening and vulnerability identification for their products.
FAQs:
Why are ransomware attacks on OT environments increasing?
The convergence of IT and OT networks, reliance on legacy systems, and recent geopolitical tensions have made OT environments prime targets.
Are ransomware attacks against OT systems increasing?
Yes. In 2025, the FBI reported that ransomware attacks on US infrastructure rose 9% and that ransomware attacks on critical infrastructure accounted for almost half of all ransomware complaints received in 2024.
How do attackers typically infiltrate OT systems?
Through phishing, exploiting unpatched vulnerabilities, abusing trusted tools, and moving laterally from IT to OT networks.
What is the most effective ransomware protection for OT?
Proactive prevention, such as memory safety hardening, virtual patching, OT-specific EDR, and supply chain transparency, offers the best defense against modern ransomware threats.
The post Ransomware in OT Environments: A 2025 Perspective appeared first on RunSafe Security.
]]>The post Securing the ICS/OT Software Supply Chain: What Schneider Electric’s Discovery Means for Industrial Systems appeared first on RunSafe Security.
]]>Recently, Andy joined us for a discussion on defending against software supply chain risks and how Schneider Electric is tackling a hidden crisis in ICS/OT security. What he shared confirmed what many in the industrial security space have suspected but lacked the data to prove. While organizations focus heavily on perimeter security, the most dangerous threats are often already embedded within their systems.
Memory Safety: The Root of Industrial Software Supply Chain Attacks
Memory safety is a topic Andy has been interested in for awhile, but it came time to prove just how significant—or not—the issue really was. Looking at all of the publicly disclosed vulnerabilities Schneider Electric had across project lines, Andy found that “memory safety was easily the largest percentage of recorded security issues that we had.”
94% of these weaknesses come from third-party components. Though that number is eye-opening, it’s not as surprising as you might think. Products today contain a significant amount of third-party or open source code.

Now, it’s important to note that this isn’t just an isolated case. We know that motivated threat actors, like Volt Typhoon and Salt Typhoon, are targeting critical infrastructure. We also know that they are using both known memory-based vulnerabilities and zero days to do so.
Consider the infamous Urgent 11 vulnerabilities that affected countless industrial control systems. Six of those eleven vulnerabilities were memory-based, and they provided attackers with significant leverage to compromise devices across multiple industries and vendors.
Memory safety vulnerabilities are widespread in software, and they are in your software supply chain too.
The Asymptotic Security Problem
Andy Kling brilliantly articulated what I consider the fundamental challenge in securing industrial systems: “We have to shift left and find out where we can improve in our own processes. But it’s also asymptotic, meaning more and more effort is going to go in to find fewer and fewer of these things.”
This asymptotic security curve means that traditional approaches yield diminishing returns. You can invest millions in better static analysis, more thorough testing, and improved development practices, yet still miss critical vulnerabilities. This isn’t to say these practices aren’t valuable—they absolutely are—but they’re insufficient on their own.
For example, some reports suggest that static analyzers for C/C++ miss 47%–80% of real vulnerabilities. Think about that: the tools we rely on for security validation are missing a significant scope of potential vulnerabilities.
This challenge is compounded by the staggering scale of industrial software. During our panel, Andy revealed that just one Schneider Electric system contained approximately 20 million lines of code—and that doesn’t even include the operating system underneath. Across their entire product portfolio, they estimate half a billion lines of code. In such vast codebases, vulnerabilities are inevitable.
The traditional approach to this problem—finding bugs and patching them—breaks down in industrial environments for several reasons. First, patches take time to develop, test, and deploy. Second, many asset owners can’t afford downtime for updates or are running critical systems that simply can’t be taken offline. Third, equipment can remain in operation for decades, far beyond standard support lifecycles.
The reality is we can’t rewrite all legacy code, and we can’t patch our way out of this problem.
A Strategic Framework for Embedded Security
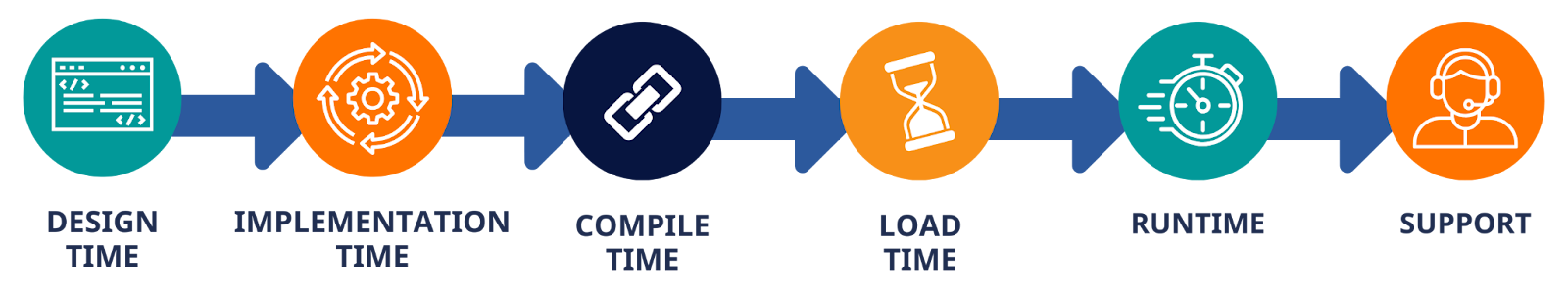
To address these challenges, we need a comprehensive approach that considers the entire lifecycle of embedded systems. Andy proposed a framework organized around “time windows” for security interventions:
- Design time: Making architectural decisions that prioritize security from the start
- Implementation time: Using secure coding practices and memory-safe languages where possible
- Compile time: Leveraging compiler tools and flags that enhance security
- Load time: Implementing protections as programs are loaded into memory
- Runtime: Detecting and preventing exploitation attempts in real-time
- Support time: Analyzing field data to identify and address potential security issues
This multi-layered approach acknowledges that no single intervention is sufficient. By considering security at each phase, organizations can build defense-in-depth strategies that significantly raise the cost and difficulty for attackers.
As Andy put it: “You have a strategy here today that allows you to achieve that vision that you have for 10 years from now. And that’s that’s the seat I’m sitting in right now, and that’s why I’m talking with RunSafe, and why I’m working on it on these other approaches.”
Innovation in Memory Protection
While addressing memory safety in the software supply chain is a challenge, we’re not without options. Several innovative approaches can help address memory safety issues without requiring complete code rewrites:
Memory-safe languages like Rust and Go offer significant security improvements, but adoption in embedded systems remains challenging due to legacy constraints, performance requirements, and the sheer volume of existing C/C++ code.
Hardware-based approaches such as ARM’s Memory Tagging Extension (MTE) and Intel’s Control-flow Enforcement Technology (CET) show promise, but implementation across diverse industrial hardware ecosystems will take time.
Load-time Function Randomization (the technology we’ve developed at RunSafe) moves code around in memory every time a program runs, preventing attackers from reliably exploiting memory vulnerabilities even when they exist in the code.
What’s particularly exciting about these newer approaches is that they change the fundamental economics of cyber warfare. Rather than playing an endless game of vulnerability whack-a-mole, these technologies make exploitation prohibitively difficult and expensive for attackers, even when vulnerabilities exist.
Action Plan for Industrial Organizations
So how should industrial organizations approach this challenge? Based on our work with clients across critical infrastructure sectors, here are key recommendations:
- Conduct a Risk Reduction Analysis to identify your most critical systems and components, focusing particularly on those with memory safety implications. Understand where your key vulnerabilities lie and prioritize protection efforts accordingly.
- Have frank conversations with vendors about their approach to memory safety and supply chain security. Ask specifically how they’re addressing vulnerabilities in third-party components and what runtime protections they provide.
- Implement a defense-in-depth strategy that includes both preventative measures (improved coding practices, memory safety) and runtime protections that can mitigate vulnerabilities even when they exist.
- Make the business case for memory safety investments by focusing on the consequences of compromise. As Andy explained: “You have to understand the likelihood is high, the potential is high. So let’s talk about consequences. And now you have an informed conversation where you can decide how to approach it.”
- Balance security with operational requirements. The best security solutions for industrial environments are those that provide protection without disrupting operations or requiring massive code rewrites.
ICS/OT Security That Gets Ahead of Supply Chain Risk
The security challenges facing industrial control systems and operational technology are significant, but they’re not insurmountable. By addressing memory safety as a root cause rather than just the symptoms, organizations can dramatically improve their security posture against both current and future threats.
As Andy showed, even organizations with massive legacy codebases can make meaningful progress by adopting a strategic, multi-layered approach to security. The key is understanding where your risks lie and implementing protections that work with, rather than against, the realities of industrial environments.
The attackers targeting our critical infrastructure are sophisticated, well-funded, and persistent. But by changing the economics of exploitation through innovations in memory protection, we can ensure that the cost of attacking these systems far exceeds any potential benefit.
That’s a future worth building—one where critical infrastructure is resilient by design, and where attackers seeking to disrupt essential services find themselves facing an insurmountable challenge. Securing embedded systems isn’t just about technology, it’s about protecting the systems that power our world.
The post Securing the ICS/OT Software Supply Chain: What Schneider Electric’s Discovery Means for Industrial Systems appeared first on RunSafe Security.
]]>The post Alternatives to Patching for ICS/OT Software and Devices appeared first on RunSafe Security.
]]>That doesn’t mean you shouldn’t patch, but you should seek out options to protect devices and embedded systems even before a patch is available. For example, runtime protections are a welcome addition to your ICS/OT patch management strategy, particularly with threat actors like Volt Typhoon targeting critical infrastructure.
The Challenges of ICS/OT Patch Management
Patching vulnerabilities in critical systems involves far more complexity than issuing updates for standard IT environments. The stakes are higher, and the constraints are substantial, particularly in OT environments.
Why Is Traditional Patching So Challenging?
1. Downtime Is Expensive and Risky
Critical infrastructure systems in industries like energy, industrial automation, and manufacturing simply cannot afford prolonged downtime. Stopping operations, even briefly, to patch a system could disrupt essential services and impact public safety.
2. Managing Legacy Systems and Compatibility Issues
Many critical infrastructure systems are built on aging or bespoke software that may not support new patches. Applying updates could introduce unintended errors or reduce system functionality.
3. Addressing Lengthy Patch Cycles
For complex OT systems, patch development, testing, and deployment can take months. This leaves systems exposed to vulnerabilities for extended periods and makes them highly attractive targets for attacks.
Why ICS/OT Systems Need More Than Patches
While patching remains an industry-standard practice, patch-only strategies leave businesses at significant risk. Three key shortcomings make traditional patching insufficient for critical infrastructure systems:
1. Delayed Vulnerability Resolution
Even when patches are eventually issued, adversaries exploit the lag between vulnerability discovery and patch deployment. This leaves OT systems particularly vulnerable to attacks, as demonstrated by global ransomware campaigns and nation-state actors that have targeted unpatched critical infrastructure.
2. Incomplete Coverage
While patching resolves known vulnerabilities, it does not protect against future attacks or zero days in software.
3. Excessive Resource Burden
Security teams spend countless hours addressing vulnerabilities rather than focusing on proactive strategies. This creates fatigue among teams and diverts resources from long-term improvements.
An Alternative Strategy for Mitigating Vulnerabilities
Given these challenges, organizations can benefit from proactive solutions that complement patching to provide stronger defenses against vulnerabilities, even before a patch is available.
One solution is runtime exploit prevention, which defends devices by mitigating vulnerabilities at runtime rather than relying on patches. Runtime exploit prevention is specifically effective against various high-risk vulnerabilities, including:
- Memory Corruption Exploits: Prevents buffer overflows, heap overflows, stack-based attacks, and other memory safety vulnerabilities.
- Return-Oriented Programming (ROP): Disrupts attackers’ ability to exploit pre-existing instructions within an application.
- Use-After-Free Exploits: Mitigates common vulnerabilities by randomizing memory layouts, rendering leaked addresses useless.
- Code Injection Attempts: Detects and blocks malicious instructions before execution.
- Zero-Day Vulnerabilities: Provides protection for memory-based zero days even when the vulnerability is unknown at the time of deployment.
A single unpatched vulnerability in SCADA or HMI systems could allow attackers to compromise an entire facility, leading to catastrophic outcomes. With runtime protections applied, many of these exploits can be prevented, significantly reducing risk to critical systems.
Case Studies: Successful Alternatives to Patching
Defending HMIs: HMI products are the most commonly attacked OT network devices, use a variety of operating systems, and are often in very difficult to update facilities within critical infrastructure. One industrial automation leader deployed runtime protection to HMI products built on embedded Linux, significantly reducing the attack surface without altering product functionality. Additionally, with runtime protections applied, the organization now has protection against memory-based zero days, which means devices are protected even before a patch is available and applied.
Embedded Systems Protection: In another example, Vertiv, a leading global provider of digital infrastructure and continuity solutions, integrated RunSafe Security’s runtime protection software as a layer into their Yocto builds to enable self-protection against memory-based attacks. RunSafe’s integration into Vertiv’s GitLab environment automated the identification and mitigation of vulnerabilities, centralizing vulnerability management and protection devices against zero days.
Future-Proofing Critical Infrastructure Security
Securing software and devices deployed across critical infrastructure is a multifaceted challenge, especially as attackers become more sophisticated. While patching remains essential, modern infrastructure operators cannot rely on it as their sole defense strategy.
Complementary solutions, like runtime protections, empower security teams to transition from a reactive stance to proactive, strategic defense planning.
Want to minimize your patching cycles and defend your systems against memory-based vulnerabilities? Explore how RunSafe Protect can strengthen your patch management strategy and safeguard your devices.
The post Alternatives to Patching for ICS/OT Software and Devices appeared first on RunSafe Security.
]]>The post CISA’s 2026 Memory Safety Deadline: What OT Leaders Need to Know Now appeared first on RunSafe Security.
]]>It’s for this reason, among other national security, economic, and public health concerns, that the Cybersecurity and Infrastructure Security Agency (CISA) has made memory safety a key focus of its Secure by Design initiatives.
Now, CISA is urging software manufacturers to publish a memory safety roadmap by January 1, 2026, outlining how they will eliminate memory safety vulnerabilities in code, either by using memory safe languages or implementing hardware capabilities that prevent memory safety vulnerabilities.
Though manufacturers are on the hook for the security of their products, the responsibility doesn’t fall solely on the shoulders of the manufacturers. Buyers of software in the OT sector also have an equally important role to play in addressing memory safety to build the resilience of their mission-critical OT systems against attack.

“The roadmap to memory safety is a great starting point for asset owners to talk to their suppliers, saying this is a big concern of mine, especially for my OT software,” said Joseph M. Saunders, Founder and CEO of RunSafe Security. “Then, what we’re looking for from product manufacturers is that they have a mature process to assess how to achieve memory safety.”
Why Memory Safety Should Be on Your Radar
Why all the fuss about memory safety, and why now? Memory safety vulnerabilities consistently rank among the most dangerous software weaknesses, and they are alarmingly common. Within industrial control systems, memory safety vulnerabilities have been steadily rising, growing from less than 1,000 CVEs in 2014 to nearing 3,000 in 2023 alone.
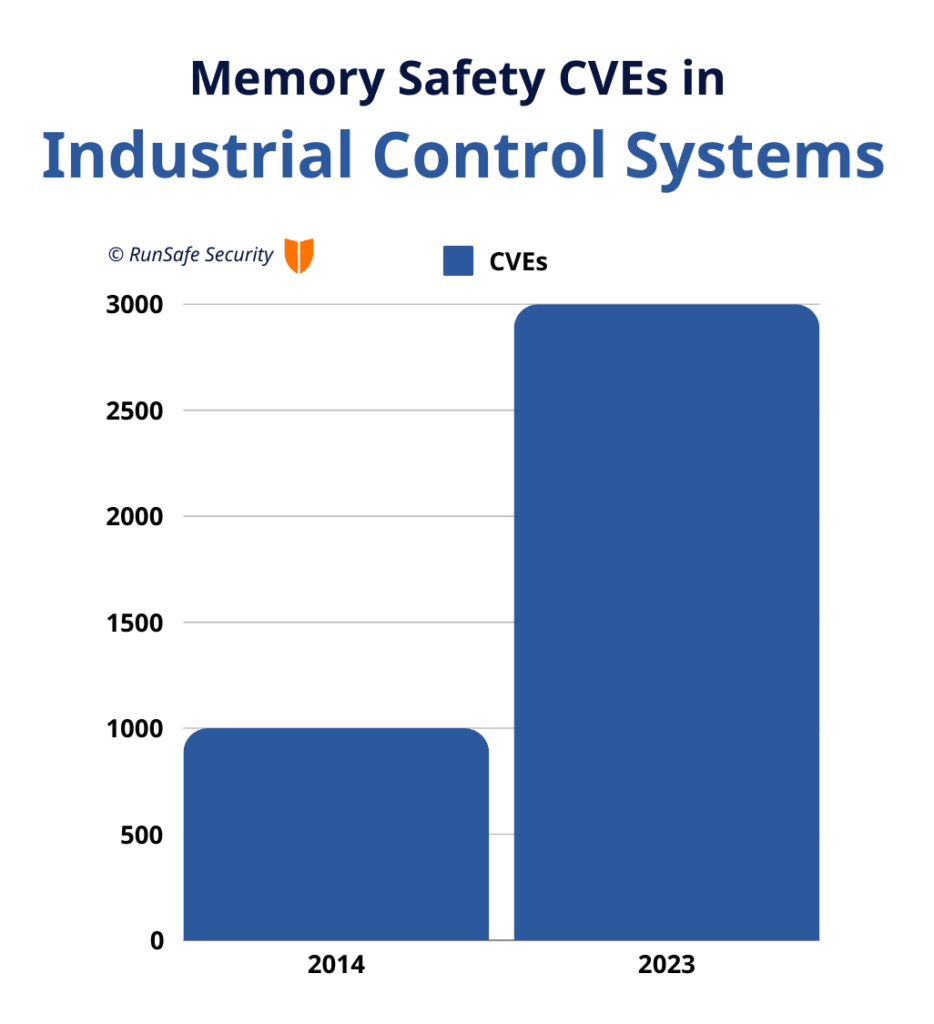
In one example, programmable logic controllers were found vulnerable to memory corruption flaws that could enable remote code execution. In the OT world, where systems control critical industrial processes, such vulnerabilities aren’t just security risks — they’re potential catastrophes waiting to happen.
Building a Memory Safety Strategy: Collaboration Between OT Software Manufacturers and Buyers Is Needed
CISA has set a clear deadline: January 1, 2026. With this date in mind, OT software manufacturers and buyers can begin to have important conversations about addressing memory safety, both for existing products written in memory-unsafe languages and for new products to be released down the line.
What should be on the agenda for discussion when building and evaluating a memory safety roadmap? Here are four key areas to look at.
1. Vulnerability Assessments
Start with a comprehensive Software Bill of Materials (SBOM) to identify and prioritize memory-based vulnerabilities in OT software. Think of it as a detailed inventory that helps you:
- Identify existing vulnerabilities
- Map your software supply chain
- Pinpoint products most at risk from memory-based vulnerabilities
2. Smart Remediation Planning
Once vulnerabilities are identified, manufacturers should take next steps to eliminate them. OT software buyers can discuss with manufacturers about remediation options like:
- Prioritizing addressing systems with high exposure and potential impact
- Evaluating options for rewriting legacy code in memory-safe languages, like Rust
- Considering proactive solutions such as Load-time Function Randomization (LFR) for existing systems when code rewrites are not practical
3. Future-Proofing Your Products
Software buyers should discuss with their suppliers how they are incorporating memory safety into their product lifecycle planning.
Look ahead by:
- Integrating memory safety into your product roadmap
- Taking advantage of major architectural changes to implement memory-safe languages
- Deploying software memory protection for existing code
4. Building Strong Partnerships
A memory safety roadmap is a great opportunity for software manufacturers and buyers to open up conversations about memory safety and collaborate to find a path forward. When considering working with a supplier, evaluate their willingness to
- Establish regular communication channels
- Transparently track progress
- Demonstrate a shared commitment to security goals
Moving Forward with CISA’s Memory Safety Guidance
By working together, software buyers and manufacturers can not only meet CISA’s memory safety mandate but also build more resilient OT systems.
“All asset owners should do a study with their suppliers to understand the extent to which they are exposed to memory safety vulnerabilities,” Saunders said.
From there, software manufacturers can build a roadmap to tackle the memory safety challenge once and for all.
Learn more about how RunSafe Security protects critical infrastructure and OT systems from memory-based vulnerabilities.
The post CISA’s 2026 Memory Safety Deadline: What OT Leaders Need to Know Now appeared first on RunSafe Security.
]]>The post Ensuring Critical Embedded Systems Security: Overcoming Challenges in OT and ICS appeared first on RunSafe Security.
]]>Challenges and Solutions for OT and ICS to Secure Software Development
Challenges in Securing Critical Embedded Systems and Industrial Control Systems
The Importance of Secure by Design Principles
Strategies for Securing Critical Embedded Systems
Future Trends and Emerging Technologies Protecting CES
Tips to Implement Secure Software Development Measures
Ensuring Critical Embedded Systems Security: Overcoming Challenges in OT and ICS
Challenges and Solutions for OT and ICS to Secure Software Development
In today’s digital landscape, securing critical embedded systems (CES) and industrial control systems (ICS) is imperative, especially for organizations whose technology, if compromised, could have severe consequences. CES, like medical devices and nuclear infrastructure, demand 100% uptime and robust security due to their essential nature. ICS, a subset of CES, regulates industrial processes from manufacturing to power generation.
These systems face unique vulnerabilities, including legacy software and limited resources, making them targets for cyberattacks. Memory-based attacks pose significant threats, potentially causing system failures with catastrophic results.
Secure software development requires a proactive approach that addresses vulnerabilities at the root level. Traditional cybersecurity measures often fall short in this regard, necessitating innovative solutions tailored to the unique requirements of critical embedded systems and ICS.
RunSafe Security offers critical embedded systems security that enhances traditional software security without compromising system performance. Through code hardening and memory protection, RunSafe defends against known and unknown vulnerabilities, safeguarding critical infrastructure and providing robust software supply chain security.
Challenges in Securing Critical Embedded Systems and Industrial Control Systems
Ensuring the security of all technology is crucial, but CES and ICS face unique challenges. These systems embed software in physical devices, making updates complex and difficult due to the need for uninterrupted performance. Moreover, CES and ICS are deployed across diverse hardware platforms, requiring tailored security approaches.
CES confronts challenges in updating and patching vulnerabilities, often operating in environments where frequent updates are impractical. Performance constraints further limit traditional security measures. The diverse hardware architectures and operating systems add complexity to security efforts, demanding adaptable solutions.
Security breaches in CES and ICS can have dire consequences, affecting various sectors from medical devices to power plants. Breaches could result in data manipulation, operational disruptions, equipment damage, or threats to human safety. The interconnected nature of modern infrastructure amplifies the impact of vulnerabilities, affecting entire supply chains and critical services. Securing these systems demands a comprehensive approach tailored to their unique requirements, emphasizing innovation and adaptability.
The Importance of Secure by Design Principles
In the realm of software supply chain security, the Secure by Design paradigm ensures that the entire organization is aligned in building software that is impeccably planned, designed, tested, and maintained.
This approach entails proactive threat modeling, multi-layered defense mechanisms, vulnerability scanning, and various other strategies to prioritize security and mitigate threats. When developing software for CES or ICS, organizations must integrate security as a critical priority from the outset. This involves implementing best practices to establish safeguards against potential threats, conducting multiple rounds of security-focused testing during the quality assurance phase, and regularly performing threat modeling and vulnerability exercises on released products.
For developers, utilizing a Software Bill of Materials (SBOM) is a valuable practice. An SBOM generates a comprehensive list of all software components and their versions, aiding in the identification of dependencies that may introduce security vulnerabilities.
RunSafe offers an efficient solution by generating an SBOM and identifying any components that may increase the attack surface of a project. Integrating RunSafe into a developer’s workflow streamlines the process, facilitating proactive security measures and ensuring the resilience of critical systems against cyber threats.
Strategies for Securing Critical Embedded Systems
Critical embedded systems security demands a multifaceted approach to address unique challenges. While human error is inevitable, strategies like automated code hardening and memory corruption prevention mitigate risks. RunSafe’s solution offers memory protection and serves as a Moving Target Defense (MTD), adjusting code structure at runtime to thwart hackers.
Automated code hardening injects unique binary diversification into software builds, protecting against memory-based attacks without system performance impact. Memory corruption prevention disrupts exploitation techniques at runtime, neutralizing threats without impairing functionality.
Supporting diverse platforms streamlines maintenance and updates, while staying updated on evolving threats is crucial. RunSafe’s solutions, compatible with various platforms including LynxOS, VxWorks, and Linux, fortify CES against known and unknown vulnerabilities.
By integrating these strategies and RunSafe’s technologies, organizations enhance CES security, safeguarding critical systems against cyber threats and ensuring uninterrupted operations.
Future Trends and Emerging Technologies Protecting CES
In the realm of cybersecurity, upcoming trends and emerging technologies are poised to revolutionize the protection of CES. One significant trend is the integration of artificial intelligence (AI) into security solutions, enabling real-time threat detection and response through advanced data analysis.
Moreover, the proliferation of Internet of Things (IoT) devices in critical infrastructure introduces both challenges and opportunities. While expanding the attack surface, IoT integration also presents avenues for innovative security measures, including device-level encryption and authentication protocols.
Tips to Implement Secure Software Development Measures
For organizations aiming to bolster their software supply chain security, implementing secure software development measures is paramount. Below are some practical recommendations:
- Adopt a Secure by Design approach: Integrate security considerations into every stage of the software development lifecycle, prioritizing security from design to deployment.
- Implement automated code hardening: Leverage tools like RunSafe’s automated code hardening solution to fortify software against memory-based attacks without compromising performance.
- Conduct regular vulnerability assessments: Perform comprehensive vulnerability scans and audits to identify and address potential weaknesses in CES and ICS environments.
- Ensure diverse platform support: Support a variety of hardware platforms and operating systems to facilitate easier maintenance and updates across environments.
- Stay informed about emerging threats: Keep abreast of evolving cybersecurity threats and trends, and continuously update security measures to adapt to changing landscapes.
- Integrate RunSafe Protect: Utilize RunSafe Protect to streamline software security processes, automate cybersecurity measures, and seamlessly integrate security into developers’ workflows.
By implementing these practical recommendations, organizations can significantly improve the security posture of their critical systems, safeguarding mission-critical infrastructure against cyber threats.
The post Ensuring Critical Embedded Systems Security: Overcoming Challenges in OT and ICS appeared first on RunSafe Security.
]]>The post Securing the Future: Understanding the Unique Challenges of Industrial Control Systems (ICS) Security appeared first on RunSafe Security.
]]>Securing the Future: Understanding the Unique Challenges of Industrial Control Systems (ICS) Security
Why ICS is vulnerable to cyber attacks
The role of cyber hardening in ICS security
Answering the call to secure our future
Picture this: you wake up in the morning, the coffee machine is already brewing your daily cup, the traffic lights are coordinating to ensure you get to work on time, and the power grid is working flawlessly to keep the lights on. These little conveniences are powered by something called Industrial Control Systems (ICS).
But, here’s the catch–these systems are kind of like the behind-the-scenes crew in a play; not always visible, but absolutely crucial.
We’re deeply invested in protecting these hidden heroes. Why? Because we know that ICS is not just about convenience; it’s about safety, productivity, and the very fabric of our day-to-day lives. We’re passionate about shielding these systems.
We’ll take you on a journey to understand why ICS security is critical, what threats lurk in the shadows, and how RunSafe’s code-hardening magic acts like an impenetrable shield for ICS.
The threats to ICS security
In the complex landscape of the cyber domain, ICS serves as the linchpin of modern society’s infrastructure, silently ensuring the seamless operation of critical processes. However, these critical infrastructures, despite their significance, are not unbreakable fortresses. Their susceptibility to intrusion and compromise makes vigilance and a strong line of defense necessary, even in military systems.
Let’s delve into real-world examples that underline the importance of fortifying these vital systems.
- U.S. Natural Gas Ransomware Attack:
-
- In early 2020, a U.S. natural gas compression facility faced a ransomware attack that had a domino effect, halting operations for two full days. The crafty attackers used spear-phishing to infiltrate the facility’s IT network and didn’t stop until they got to the operational technology (OT) network. Although the facility didn’t lose control over operations, they decided to hit the brakes for safety. The cyber incident revealed that while they had an emergency plan for physical threats, cyber-attacks were like uncharted waters.
- Northern Israel Irrigation Sytems
- In April 2023, hackers hit Northern Israel’s irrigation systems and Galil Sewage Corporation’s controls. Despite warnings from the National Cyber Directorate to disable remote connections, some folks didn’t act fast enough. Michael Langer of Radiflow disclosed that the hackers meddled with Unitronics’ programmable logic controllers. This wasn’t random – it was part of OpIsrael, a campaign with a knack for targeting human-machine interfaces. It’s a classic tale of what happens when the essentials, like changing default passwords, take a back seat.
- Stuxnet:
- Consider Stuxnet, discovered in 2010; it was an exploit that targeted Iran’s nuclear program – and more precisely its industrial control systems (ICS).
Once inside the ICS, Stuxnet manipulated the code running on the programmable logic controllers, specifically the ones responsible for controlling the centrifuges used in the uranium enrichment process. By subtly altering the speed and operation of the centrifuges, Stuxnet ultimately crashed the systems in Iran’s facility without prior detection.
Why ICS is vulnerable to cyber attacks
Why is ICS especially vulnerable?
Many of the systems have been around for a while; they’re the grizzled veterans of the industry. While they’re superb at what they do, they weren’t designed with modern cybersecurity in mind. Moreover, the rise of the Industrial Internet of Things (IIoT) means more connectivity and, by extension, more vulnerabilities.
These aren’t just isolated incidents; they’re part of an ongoing cyber onslaught that needs sophisticated defenses. We recognize the value that ICS brings to our day-to-day life, and we’ve committed ourselves to protecting these systems with our technology.
What if a similar type of cyber attack to Stuxnet were to target critical infrastructure systems within the United States? Water systems, gas pipelines, oil rigs, power grids, transportation infrastructure, financial systems, and weapons programs could all be at risk. The disruption caused by such attacks would jeopardize the essential services and mission-critical systems upon which we depend everyday to support a well-functioning society.
The role of cyber hardening in ICS security
Our mission is to harden the code that runs the ICS, turning them into fortresses. But what does code hardening mean? Imagine you could constantly shuffle the inner workings of a system so that attackers can never get a read on how it’s structured. It’s like trying to hit a moving target while blindfolded–nearly impossible!
Besides, there’s a treasure chest of open-source software out there that’s gold for ICS functionality. But guess what? They too, can be exploited. RunSafe has that covered as well.
By hardening code, we’re ensuring that if an attacker somehow makes it through the outer defenses, the castle keep is a maze that changes every time they turn a corner. RunSafe is turning ICS security into a fortress that is not just strong, but also smart.
Answering the call to secure our future
We’ve taken you on quite a journey today, from malicious cyber threats to strong defenses in code hardening. Industrial Control Systems are fundamental to modern civilization, and safeguarding them is not just an option; it’s an imperative.
At RunSafe, we believe in equipping ICS with the best armor technology can offer. With our innovative cyber hardening techniques, we are not just defending; we are outsmarting the enemy.
We ask you, the stakeholders and caretakers of critical infrastructure, to recognize the value and urgency of this mission. Stand with us as guardians at the gate. Together, we can ensure the conveniences we so often take for granted are preserved and protected for generations.
Let’s build a future that’s not just secure, but unassailable. Team up with RunSafe and be the champions of a modern-day fortress. Secure your ICS, and with it, secure the future.
The post Securing the Future: Understanding the Unique Challenges of Industrial Control Systems (ICS) Security appeared first on RunSafe Security.
]]>The post Schneider Electric Chooses RunSafe to Protect HMI Products appeared first on RunSafe Security.
]]>Schneider Electric Chooses RunSafe to Protect HMI Products
What is HMI and Why Is It Important to Industrial Security?
Protect Your Software Against Vulnerabilities
Over the past several years, Hackers Arise has noted that attackers target ICS/SCADA systems in two primary areas:
- Attack the protocols (modbus, DNP3, etc);
- Attack the Human Machine Interface (HMI).
Though both types of attacks can be devastating, attacking the HMI can lead to full compromise of your entire operational technology.
What is HMI and Why Is It Important to Industrial Security?
In most SCADA/ICS installations, there is a dedicated system for managing and monitoring the industrial system. Most people in the industry refer to this as the human machine interface or HMI. This system is crucial to the management of the industrial system but also can be a critical vector for attackers.
A common way to attack the HMI system is through a buffer overflow or similar memory corruption attack. Once an attacker gains control of the HMI system, according to Hackers Arise, he or she owns the industrial network resulting in any number of unknown malicious activities, such as disabling sensors and alarms, increasing temperature and pressure, altering the mix of concentration of chemicals, altering the ladder logic, and disabling controls.
How to Protect HMI Products
This is why RunSafe industrial customers have turned to us to help protect their HMI products. In fact, recently after extensive testing and evaluation, Schneider Electric’s Industrial Automation team has settled on RunSafe Security’s advanced cybersecurity solution to protect its HMI product line.
Now, Schneider and its distributors can offer customers protections against the most common and most devastating exploits without changing system performance or slowing down developers.
“Schneider’s HMI Product is a perfect use case for RunSafe technology. It’s Linux-based software and Schneider’s customers require a high level of cyber resilience to protect critical infrastructure,” said Joe Saunders, Founder & CEO of RunSafe. “We’re excited to support Schneider and its customers in an effort to make the world a safer place by eliminating the exploitability of memory-based vulnerabilities in software code.”
Protect Your Software Against Vulnerabilities
RunSafe’s patented technology, RunSafe Code, protects against known and unknown vulnerabilities – without changing original software functionality and without slowing down software development – even when a patch is not available. RunSafe Code is integrated at build time for protection at run time.
Try Code for free today and stop hackers from exploiting memory-related vulnerabilities lurking within your code.
The post Schneider Electric Chooses RunSafe to Protect HMI Products appeared first on RunSafe Security.
]]>The post ICS Advisory Recap: How to Mitigate Today’s Most Prevalent Cyber Risks appeared first on RunSafe Security.
]]>ICS Advisory Recap: How to Mitigate Today’s Most Prevalent Cyber Risks
How RunSafe Protects Against These Attacks
Prioritize Cybersecurity and Reduce Attack Surface with RunSafe
At RunSafe Security, we appreciate the tremendous work Cybersecurity and Infrastructure Security Agency (CISA) performs to help our nation be more resilient.
In fact, we recently released our Attack Surface Reduction Index™ model to help organizations identify and prioritize which software to protect against exploits targeting critical infrastructure and open-source software. The ASRI model, if you have not seen it yet, is based on the National Vulnerability Database, incorporating recency, frequency, and severity of exploits targeting devastating vulnerabilities in proprietary and open-source software.
It turns out that memory-based attacks are the most common and most severe types of attacks challenging our critical infrastructure. Along the way, our internal RunSafe team has gotten accustomed to the regular ICS-CERT Advisories CISA delivers; we forget to share how we prevent the related attacks. So we thought it would be important to review some advisories and how RunSafe’s advanced security techniques protect against devastating memory-based exploits even when a patch is not available.
Recent ICS-CERT Advisories
These recent ICS-CERT Advisories focus on software vulnerabilities and highlight how important it is to protect your organization from outside threats. Supply chain vulnerabilities are a significant threat and should be addressed quickly and efficiently.
Hitachi Energy e-mesh EMS (ICSA-22-090-02)
Original release date: March 31, 2022
This ICS Advisory was issued for Hitachi Energy’s e-mesh EMS software. The attack had a low attack complexity and was easy to deploy remotely, impacting Node.js vulnerabilities.
Vulnerabilities that were targeted are Improper Restriction of Operations Within the Bounds of a Memory Buffer, Use After Free, and Uncontrolled Resource Consumption. If exploited, attackers could gain control of systems and create denial-of-service conditions.
Mitigations
It is essential to protect internet-enabled devices and open-source software from attacks originating from outside the network. It is possible to reduce the IoT attack surface with embedded device protection software. IoT devices are difficult to patch, and attacks can lead to costly downtime.
Built-in security that doesn’t affect source code is essential. These can be built directly into the build process with CODE. For active open-source software, REPO can provide pre-hardened code to provide additional protection.
DevSecOps tools like Alkemist can provide memory protection prior to deployment and passively block Zero-Day exploits to prevent memory corruption by immunizing software and providing ongoing monitoring.
Siemens SINEC INS (ICSA-22-069-09)
Original release date: March 10, 2022
This ICS Advisory identifies a low complexity, remotely deployable attack made on Siemens SINEC INS. This attack exploited vulnerabilities in the supply chain. 71 third-party components were affected due to vulnerabilities in Node.js, cURL, SQLite, CivetWeb, and DNS(ISC BIND).
Supply chain threats are some of the most common attacks DevSecOps teams deal with. Third-party connections provide a vast attack surface as open-source code from suppliers is often riddled with hidden vulnerabilities that can then be passed into your systems. In fact, supply chain threats are considered the greatest emerging threats to the industry.
Mitigations
Inoculating systems against hardware and software supply chain vulnerabilities is absolutely essential for software security. You cannot rely on third-party cybersecurity measures to protect your systems.
Always verify supply chain protection, but take it further and eliminate security dependence on suppliers. Limit your exposure to open-source vulnerabilities with a security solution that understands the risks that come from outside suppliers.
Alkemist can protect against threats throughout the development lifecycle—even when you don’t have source code.
Wibu-Systems CodeMeter (Update F) (ICSA-20-203-01)
Original release date: March 10, 2022
This ICS Advisory for Wibu-Systems AG CodeMeter again identifies a low complexity, remotely exploitable attack on open-source software. This attack targeted several vulnerabilities, including Buffer Access with Incorrect Length Value, Inadequate Encryption Strength, Origin Validation Error, Improper Input Validation, Improper Verification of Cryptographic Signature, and Improper Resource Shutdown or Release.
The exploitable vulnerabilities would allow attackers to gain access to systems and wreak havoc. Denial-of-service conditions and hindrance of dependent third-party software were just some of the expected outcomes should an attack be successfully deployed.
Mitigations
This advisory once again highlights the importance of supply chain security. There were nearly a dozen additional security advisories tied to the CodeMeter advisory. Vulnerabilities in one third-party supplier negatively impacted multiple other software.
Relying on third-party cybersecurity measures or not adding additional security measures within your own software will lead to an untold number of vulnerabilities to be exploited. More than half of organizations who experienced a breach identified supply chain vulnerabilities as the precursor.
Security solutions like Alkemist can prevent attacks from third-party vulnerabilities, shrinking attack surfaces and limiting the opportunity for damage and interruptions.
Multiple Data Distribution Service (DDS) Implementations (Update A) (ICSA-21-315-02)
Original release date: February 01, 2022
As with the previous advisories, this ICS Advisory identifies a low complexity, remotely exploitable attack. This particular advisory impacts multiple open-source Object Management Group (OMG) Data-Distribution Service (DDS) implementations.
Vendors affected include Eclipse, eProsima, GurumNetworks, Object Computing, Inc. (OCI), Real-Time Innovations (RTI), and TwinOaks Computing. Equipment affected includes CycloneDDS, FastDDS, GurumDDS, OpenDDS, Connext DDS Professional, Connext DDS Secure, Connext DDS Micro, and CoreDX DDS.
The vulnerabilities are Write-what-where Condition, Improper Handling of Syntactically Invalid Structure, Network Amplification, Incorrect Calculation of Buffer Size, Heap-based Buffer Overflow, Improper Handling of Length Parameter Inconsistency, Amplification, and Stack-based Buffer Overflow. If successfully exploited, these vulnerabilities can result in denial-of-service or buffer-overflow conditions.
Mitigations
DDS is the standard for securing Industrial Internet of Things (IIoT) systems in real-time. Unfortunately, even industry standards can have vulnerabilities that can have a significant impact on your systems.
The industries that utilize OMG DDS simply cannot risk vulnerabilities like these being exploited. Employing additional security measures within your own software is absolutely essential.
Reducing the IIoT attack sur犀利士
face with solutions like Alkemist will inoculate systems and IIoT devices against hardware and software supply chain vulnerabilities. Prevent attackers from deploying malware, stealing trade secrets, or threatening national security by closing third-party vulnerabilities.
How RunSafe Protects Against These Attacks
RunSafe Alkemist products immunize software and provide continuous monitoring of your system’s health. Our suite of products allow you to implement protections throughout the software development life cycle without impacting your code.
CODE
CODE is an excellent DevSecOps tool. This technology allows developers to insert protection at build time without disrupting release schedules. Keep developers focused on what needs to get done and leave the security to RunSafe with a cybersecurity solution that provides built-in security from the start.
REPO
Download pre-hardened software and eliminate your exposure to cyber attacks. Add patented runtime cyber protections directly into your open-source software to secure critical infrastructure and prevent vulnerability exploitation. With REPO, you can stay protected and save both time and resources.
FLARE
Don’t expose yourself to damaging attacks and costly service disruptions. Current scanning technology misses 50% of vulnerabilities and runtime app monitoring technology misses many indicators of lurking threats. FLARE doesn’t. Continuously monitor the health of your systems, flag potential threats, and mitigate risk automatically with Flare.
Prioritize Cybersecurity and Reduce Attack Surface with RunSafe
Every business is under a constant threat of cyber attack. Prioritizing cybersecurity prevents vulnerabilities from damaging critical infrastructure—as well as your reputation.
DevSecOps tools like embedded device protection software or cloud workloads protection software are necessary in-house. Don’t rely on third-party cybersecurity or simple firewalls when it comes to open-source software and IoT.
Render threats inert with RunSafe’s Alkemist.
No matter where you are in your software’s development life cycle, Alkemist can minimize the attack surface and protect against memory-based attacks that could cripple your organization. Try it for free today and see how RunSafe can keep your open-source software protected against threats from any angle.
FAQs:
What are the most common types of attacks on infrastructure?
It turns out that memory-based attacks are the most common and most severe types of attacks challenging our critical infrastructure.
Why is prioritizing cybersecurity important?
Every business is under a constant threat of cyber attack. Prioritizing cybersecurity prevents vulnerabilities from damaging critical infrastructure—as well as your reputation.
Can RunSafe help me prevent software exploitation and other breaches?
No matter where you are in your software’s development life cycle, Alkemist can minimize the attack surface and protect against memory-based attacks that could cripple your organization.
The post ICS Advisory Recap: How to Mitigate Today’s Most Prevalent Cyber Risks appeared first on RunSafe Security.
]]>The post How Runtime Application Self-Protection (RASP) Can Prevent Cyberattacks in Oil & Gas Environments appeared first on RunSafe Security.
]]>Like all sectors of critical infrastructure, the oil and gas (O&G) industry has emerged as a top target for cyberattack, yet most companies are not doing nearly enough to mitigate the risks.
Demand for business insight and device monitoring has led many O&G companies to merge operational technology (OT), such as their control systems, with enterprise IT systems. While the digitization of operational processes offers cost savings and improved productivity, the convergence of these two disparate business units has opened the door to a variety of risks upstream, downstream, across pipelines and throughout the supply chain.
Traditionally, O&G companies have implemented cybersecurity measures that focus on detecting symptoms of attacks. They use external network and perimeter technologies such as gateways, firewalls, intrusion prevention and anti-virus agents, as well as static and dynamic analysis to try to detect vulnerabilities. But as threats evolve in frequency and sophistication, a more proactive set of defenses, along with an elevated sense of urgency, must prevail.
Legacy Equipment and Systems Vulnerable to Attack
Many O&G companies still operate with legacy equipment and systems that were never designed for connectivity, nor to withstand today’s attacks. While components that manage processes like extraction controls, blowout prevention, and metering systems have been retrofitted with internet-connected features, most retain vulnerabilities and lack effective security controls. Furthermore, because field-level personnel often make decisions about industrial control systems (ICS) software, many O&G companies have multiple solutions, all with varying levels of security. And to make matters worse, many facilities operate on outdated networks. like Windows XP, or even OS systems from the ‘90s.
Additionally, as O&G networks become more dependent on sensor data, they also become more vulnerable to spoofing attacks, denial of service, or social engineering. This can lead to production shutdown if the signal or energy source to an actuator is interrupted during a cyberattack. Attackers can also breach a critical access point to gain control of operations and weaken machinery or cause overheating. Malware attacks can not only result in a loss of data, but also interfere with control system operability, such as interrupting air conditioning or heat, which could put refinery operations out of commission.
The risks are already well-known. The Ponemon Institute surveyed 377 U.S. oil and gas cybersecurity risk managers in 2017, and nearly 70 percent said their operations have had at least one security compromise in the past year.
New Technologies Needed to Protect Against New Threats
Some O&G companies are trying to meet the threats, but their efforts aren’t enough. Roughly 60 percent of those surveyed by Ponemon said they have difficulty managing risks across the supply chain. While there are effective security technologies available, such as user behavior analytics, hardened endpoints and encryption of data in motion, less than half said they would deploy any of these technologies in the next twelve months.
Most importantly, traditional cybersecurity measures aren’t built to prevent malware from propagating because they mainly rely on network and perimeter solutions. In other words, these tools focus on identifying underlying symptoms rather than causes. Detection offers no protection in cases where the supply chain itself is compromised, such as in file-less attacks like memory corruption exploits, stack and heap attacks, zero-day attacks or return oriented programming (ROP) chain attacks.
While detection monitoring is important, it isn’t and end-all solution, and it also requires time, investment and expertise to implement. Re-engineering code can also help enhance security, but to do so requires significant resources, and can trigger compliance risks, especially when the software stack can be hundreds of thousands or millions of lines long.
Hardening Systems with Runtime Application Self-Protection
One of the latest and most effective means to reduce risk is to cyberharden systems using Runtime Application Self-Protection (RASP) technology, which reduces risk by preventing exploits from spreading across multiple devices and networks. RASP hardens software binaries by using techniques such as binary stirring, control flow integrity and a priori optimization.
RASP techniques harden software binaries so that attackers can’t calculate in advance how to successfully execute their code. This can prevent an entire class of malware attacks related to buffer overflows.
There have already been several high-profile incidents in the O&G industry where RASP and randomization could have prevented the attack. In August 2017, Schneider Electric’s Triconex Safety Instrumented Systems (SIS) controllers were infected with Triton malware at a Saudi Aramco facility in the Middle East. Attackers gained access to the SIS engineering workstation to plant first stage malware, then downloaded new malicious code. Some controllers entered a failsafe state which automatically shut down the industrial process and prompted the owner to begin an investigation. In a case like this, cyberhardened SIS controllers could have completely prevented the attack, because the malware would not have been able to replicate.
RASP is easy to implement and requires no new additional investments, software, services or hardware and only a one-time transformation with limited overhead. No access to source code complier, or operating systems is needed. Finally, RASP doesn’t require alerts to monitor, and it is remotely deployable, as binary code can be cyberhardened via API.
Because of all the benefits, RASP adoption is increasing. According to a report by MarketsandMarkets, the RASP market is expected to grow at a compound annual growth rate of 33 percent to $1.24 billion by 2022.
The cyberthreats against the oil and gas industry are more complex than ever before. Moving from traditional security defenses to cyberhardening binaries can reduce risk by stopping attacks before they can execute
The post How Runtime Application Self-Protection (RASP) Can Prevent Cyberattacks in Oil & Gas Environments appeared first on RunSafe Security.
]]>The post Industrial IoT’s Kryptonite: Looming Threats Poised to Disrupt Critical Infrastructure appeared first on RunSafe Security.
]]>Super Strength Precipitates Threatening Weaknesses
Industrial devices are designed to have a long life span, but that means most legacy equipment still in use was not originally built to achieve the automation and connectivity that the Internet of Things (IoT) makes possible. To realize these benefits, manufacturers and OEMs are forcing coding and connectivity on to devices that simply weren’t built for it. The advantages are certainly numerous – the ability to share data and intelligence, communicate with other machines and detect issues before problems occur. But because these machines weren’t constructed for such functionality, and because code is forced at both the machine and parts levels, the industrial IoT landscape is filled with vulnerabilities.
As such, the supply chain is a prime target for cyber criminals. Supply chain cyber attacks increased 200% in 2017. As more and more industrial devices are brought online, this number will increase exponentially. In fact, IDC anticipates that 90% of all IT networks will have an IoT based security breach in the next two years.
This year is certainly set to be another record breaker, most notably with Russia’s targeting of Industrial IoT (IIoT). In April, the FBI, Department of Homeland Security and the U.K.’s National Cyber Security Centre issued a joint warning regarding state-sponsored Russian hackers. The alert noted that critical infrastructure, government agencies, large companies and internet service providers were the most likely targets of such an attack.
The fallout from cyber attacks on the supply chain and critical infrastructure can be enormous. A single exploited vulnerability can bring operations to a halt, resulting in costly delays. In the worst cases, critical devices can shut down access to electricity or safe water, putting municipalities in panic mode. Loss of significant revenue, impediments to power, transit and banking, and even loss of life aren’t unexpected consequences of a carefully targeted cyber attack.
The Antidote to IIoT’s Kryptonite
The convergence of operational technology (OT) and information technology (IT) brings efficiency, scalability and cost savings to industrial infrastructure via IoT. But these previously disparate machines now communicate across unsecured networks, and the connectivity of these legacy systems has spawned thousands of complex vulnerabilities.
The challenges and risks are two fold:
- Online configurations of machines not meant for such code leave vulnerabilities at the machine level.
- Each digitized, connected piece and part is also an attack target.
Traditional cybersecurity techniques only identify potential problems and anomalies, but don’t provide solutions. OEMs issue patches for known vulnerabilities and attack vectors, but those don’t account for the wide array of unknown vulnerabilities. Couple these technological challenges with the fact that most organizations don’t have anyone solely dedicated to device, facility level cybersecurity, and the risks of a breach are high. On-site operational managers are responsible for keeping everything running on-time and safely. They typically only have time to get involved in cybersecurity when an anomaly is detected. Corporate digital security teams don’t have full focus or visibility into facility level operations, leaving a gaping hole in industrial Internet of Things security.
To combat these challenges, manufacturers and critical infrastructure operators must move beyond attack identification and detection to prevention-based measures. With risks soaring, the focus should be on stopping attacks before they can occur, thereby protecting industrial control systems. Cyberhardening devices operating Runtime Application Self Protection (RASP) is the best way to proactively increase industrial Internet of Things security. Built-in security and protecting apps via randomization prevents attacks from succeeding and from scaling across an organization.
Preventing attacks is the only way to maintain uptime and minimize risks – simply detecting issues is not enough to maintain critical infrastructure amid increase cyber attacks.
For a deeper look at the strengths and weaknesses of conventional cybersecurity tools and the necessity of cyberharding industrial IoT devices, download our whitepaper.
The post Industrial IoT’s Kryptonite: Looming Threats Poised to Disrupt Critical Infrastructure appeared first on RunSafe Security.
]]>










