The post How Aviation Cybersecurity Strategy Became the Industry’s Biggest Blind Spot appeared first on RunSafe Security.
]]>Key Takeaways:
- Aviation cybersecurity strategy is now as critical as traditional flight safety measures.
- The FAA is introducing new cybersecurity requirements that elevate security to a core part of aircraft airworthiness.
- Legacy systems like the F-35 face challenges adapting to today’s cybersecurity landscape without costly overhauls.
- Solutions such as SBOMs, runtime code protection, and security certifiability are key to protecting aviation’s future.
For decades, aviation has operated under a simple but powerful principle: safety first. The industry’s rigorous certification standards have created some of the world’s most reliable systems, with aircraft designed to account for every conceivable mechanical failure, weather condition, and human error.
But that very mindset—safety above all—has created a blind spot. While the aviation industry perfected aviation flight safety, it overlooked an equally urgent priority: cybersecurity. Modern aircraft are hyper-connected flying computers, connected to ground networks, satellite systems, and the internet itself.
In their 2025 report, the Cyberspace Solarium Commission offered a warning. The aviation industry is facing escalating threats from ransomware attacks, GPS spoofing, and sophisticated cyber intrusions.
A new aviation cybersecurity strategy is now mission-critical for protecting passengers, operations, and national security.
Listen to the Audio Overview
Safety vs. Security: What DO-356 Tells Us
The aviation industry relies on DO-178C and similar safety standards, which focus on ensuring that flights land safely despite system failures, hardware malfunctions, or software bugs. These standards have been remarkably successful, as commercial aviation remains one of the safest forms of transportation.
However, these safety protocols were designed for an era when the primary threats were mechanical failures and human error, not malicious attacks. DO-178C accounts for everything that should be on an aircraft, but it doesn’t address threats from sources that shouldn’t be there, like hackers infiltrating flight systems through network connections.
As DO-356, the aviation industry’s newer security standard, explicitly states: “Safety and security are not the same thing; however, there is a strong overlap.” The document acknowledges what many industry professionals are only now realizing: a security breach can quickly become a safety issue. If flight systems are designed with safety in mind, but not security, they are not truly safe. A breach of security will cause a violation of safety.
Building a Modern Aviation Cybersecurity Strategy
Recognition of the problem is the first step toward solving it. The Federal Aviation Administration proposed new cybersecurity requirements in August 2024 that would make cyber protection a standard part of airworthiness for newly built airplanes and equipment.
Additionally, one of the recommendations stemming from the CSC report is that “The FAA and TSA should harmonize cybersecurity regulatory requirements for the aviation subsector.” This includes referencing existing NIST frameworks and adding guidelines for supply chain security unique to the needs of the aviation industry.
The Challenge of Legacy Aircraft and Flight Systems
Compliance with regulations, however, is far from simple and comes at a significant cost, particularly for legacy or long-lived systems. Take the F-35, for example. Its prototype and design work began in the 1990s, well before today’s cybersecurity threats had taken shape. While it incorporates cutting-edge technology, much of its foundational architecture was conceived in a pre-cyber era. These systems must now be retrofitted or augmented to meet security measures within the constraints of rigid defense budgets that often make comprehensive overhauls impossible.
Steps to Strengthen Aviation Flight Safety Through Cybersecurity
Where should the aviation industry invest its time and dollars? The first step is elevating software security to the same level of importance as flight safety. A July 2024 study by SecurityScorecard, a cybersecurity firm, found that the aviation industry overall scores a “B” on cybersecurity and that aviation-specific software and IT vendors scored the lowest in cybersecurity readiness across industries.
1. The Role of SBOMs and Embedded Software Security
Improving this score requires implementing Software Bills of Materials (SBOMs) to track every software component in aviation systems and prioritizing vulnerability management with the same rigor as mechanical maintenance.
2. Securing Legacy Aircraft with Runtime Protections
For older systems, runtime code protection technologies can strengthen cybersecurity without requiring full code rewrites, bridging the gap between legacy architecture and modern security standards.
3. Toward Safety-Certifiable Cybersecurity
Also on the horizon are security solutions that attain safety of flight certifiability, making security a much easier and obvious piece of highly-regulated aircraft.
From Blind Spot to Cybersecurity Strategy
Aviation’s cybersecurity blind spot didn’t develop overnight, and isn’t easily resolved. However, the industry’s legendary commitment to safety provides a strong foundation for building equivalent security standards. The same methodical, evidence-based approach that made flying safer than driving can be applied to making it more secure.
The industry that taught the world how to fly safely now has the opportunity to show how to fly securely as well.
Read more about how RunSafe supports an overall aviation cybersecurity strategy in our white paper: “RunSafe Security Safety of Flight Approach.”
The post How Aviation Cybersecurity Strategy Became the Industry’s Biggest Blind Spot appeared first on RunSafe Security.
]]>The post Reducing Your Exposure to the Next Zero Day: A New Path Forward appeared first on RunSafe Security.
]]>Our goal at RunSafe is to give defenders a leg up against attackers, so we wondered: What if we could quantify this seemingly unquantifiable risk? What if we could take meaningful action to implement zero-day protection for systems before vulnerabilities are even discovered?
To dig into these questions, we partnered with Ulf Kargén, Assistant Professor at Linköping University, who developed the CReASE (Code Reuse Attack Surface Estimation) tool, which underpins RunSafe’s Risk Reduction Analysis.
Quantifying the Unquantifiable: A New Approach to Zero-Day Risk
VulnCheck, in their “2024 Trends in Vulnerability Exploitation” report, found that 23.6% of all actively exploited vulnerabilities in 2024 were zero-day flaws. We’re seeing nation-state actors like Volt Typhoon and Salt Typhoon specifically target these unknown vulnerabilities to achieve their objectives, as noted in research from Google Threat Intelligence Group, which tracked 75 zero-day vulnerabilities exploited in the wild in 2024.
Most of the industry’s response to zero days has been trying to detect and prevent threats by looking for indicators of attack, suspicious behavior, and patterns that might tip us off. But attackers have gotten really good at hiding and masking their activity. What’s been left wide open is the underlying risks in software itself. Instead of securing the foundation, we’ve built bigger walls around our systems.
That might work in a data center where systems live behind firewalls and racks of gear. But in the world of IoT and embedded devices, there are no walls. These systems are deployed far from the protection of the network where they are alone, exposed, and vulnerable. They need to be self-reliant. They need to be like samurai—able to defend themselves without backup.
Because of this, we saw the need for a method to quantify the risk of zero days and a way to make devices intrinsically more robust against exploitation, regardless of what vulnerabilities might exist within them. If you can quantify risk with real technical rigor, you can make smart decisions to reduce your attack surface and make a compelling argument to leadership on where to focus resources.
Return-Oriented Programming: Understanding the Threat
Modern cyberattacks frequently use a technique called Return-Oriented Programming (ROP). When traditional code injection attacks became difficult due to improved security measures, attackers evolved to use “code reuse” attacks instead.
Modern exploits repurpose a program’s own code, using existing code snippets (called “gadgets”) within a program and chaining them together to create malicious functionality. The program’s own code is weaponized against itself.
This insight gives us a way to measure memory-based zero-day risk specifically. While it’s impossible to predict all potential vulnerabilities in code, we can analyze whether useful ROP chains exist in a binary that could lead to the successful exploitation of a vulnerability.

Quantifying Zero-Day Risk with CReASE
We worked alongside researcher Ulf Kargén at Linköping University who developed the Code Reuse Attack Surface Estimation (CReASE) tool to quantify previously unmeasurable risk. You can listen to Ulf discuss the tool and how it works in this webinar.
CReASE scans binaries to identify potential ROP gadgets and determines whether they could be chained together to perform dangerous system calls. It doesn’t try to predict where specific vulnerabilities might exist but instead analyzes whether the code structure would allow successful exploitation if a vulnerability were discovered.
It answers the question: Are any useful ROP chains available to an attacker?
Unlike existing tools that focus on guaranteeing working exploit chains (often sacrificing scalability or completeness), CReASE uses novel data flow analysis to achieve both scalability and completeness comparable to a human attacker.
The result is a risk scoring system that quantifies the probability that the next memory-based zero-day vulnerability could be exploited to achieve specific dangerous outcomes like remote code execution, file system manipulation, or privilege escalation.
The CReASE tool underlies RunSafe’s Risk Reduction Analysis, which you can use to analyze your exposure to CVEs and memory-based zero days.
The Memory Safety Challenge
To understand why this approach is so powerful, we need to recognize two critical facts:
- 70% of vulnerabilities in compiled code are memory safety vulnerabilities
- 75% of vulnerabilities used in zero-day exploits are also memory safety vulnerabilities
These numbers tell us that memory safety vulnerabilities constitute a significant risk in our codebases. When a memory vulnerability is exploited, attackers can execute arbitrary code, take control of devices, crash systems, exfiltrate data, or deploy ransomware.
By focusing our risk quantification and mitigation efforts on memory-based vulnerabilities specifically, we’re addressing a common and dangerous attack vector for zero-day exploits.
Memory Randomization: Making Zero-Day Vulnerabilities Inert
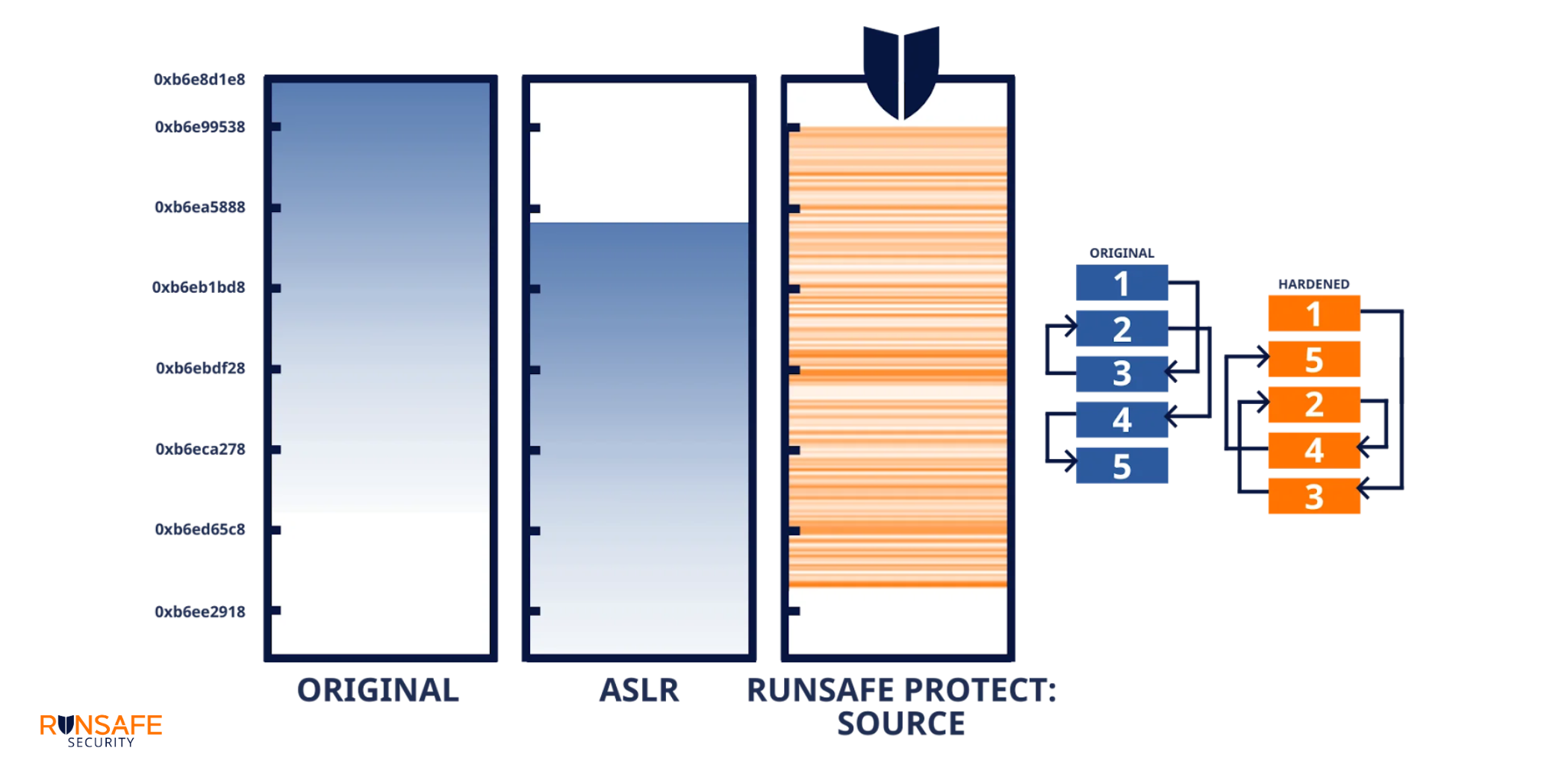
Once we quantify the risk, what can be done about it? Traditional memory protection like Address Space Layout Randomization (ASLR) provides some security by randomizing where blocks of code are loaded in memory. However, ASLR still loads functions contiguously, making it vulnerable to information leak attacks.
RunSafe’s approach takes randomization to the function level. Instead of randomizing where the entire binary loads, we randomize each function independently. In a typical binary with 280 functions, this creates 280 factorial possible memory layouts — more than 10^400 combinations.
Even if a memory-based zero-day vulnerability exists, with RunSafe’s Load-time Function Randomization (LFR), attackers can’t reliably construct a working ROP chain because they can’t predict where the necessary gadgets will be located. We’ve effectively made the vulnerability inert.
Taking Action: Zero-Day Vulnerability Protection
The most effective approach to memory-based zero-day risk combines analysis and protection:
- Analyze your binaries to understand your current risk profile
- Apply function-level randomization to neutralize potential exploits
- Measure the risk reduction to quantify your improved security posture
Our customers typically see a risk reduction that changes the odds from “the next zero-day can compromise the system” to “maybe one in the next 10,000 zero-days might succeed.” That’s a dramatic improvement in security posture.
While no solution can eliminate all types of zero-day vulnerabilities, addressing memory-based vulnerabilities targets the most common and dangerous attack vector. In a world where zero-days will always exist, making them ineffective is the next best thing to eliminating them entirely.
Want to try out the Risk Reduction Analysis tool for yourself? All you’ll need to do is create an account and upload a binary to get your results.
Run an analysis here.
The post Reducing Your Exposure to the Next Zero Day: A New Path Forward appeared first on RunSafe Security.
]]>The post Zero-Day Vulnerabilities: Exploitation Trends and Lessons Learned appeared first on RunSafe Security.
]]>In 2024 alone, security researchers at Google tracked 75 zero-day vulnerabilities exploited in the wild. Particularly alarming is that 44% of these targeted enterprise products, highlighting how attractive zero-day vulnerabilities are to cybercriminals and nation-state threat actors. For example, we’ve seen how Volt Typhoon and Salt Typhoon have specifically targeted operational technology (OT) systems through unpatched vulnerabilities.
Whether we’re considering weapons systems, critical service providers, security vendors, or others, nation-states and other malicious actors have their eyes on zero-day flaws as a means to cause widespread damage and disruption.
What Are Zero-Day Vulnerabilities and Why Are They Exploited?
A zero-day vulnerability is a flaw in software that is unknown to the software’s developers or vendors. Because no patch exists to correct the flaw, attackers can exploit it to gain unauthorized access to systems, disrupt operations, or steal sensitive data. Zero-day attacks are especially dangerous because they target unsuspecting systems, leaving defenders without sufficient time to react until after the vulnerability is discovered and addressed.
Attackers exploit zero-day vulnerabilities for several reasons:
- Access to critical systems: Whether targeting enterprise networks or OT environments, attackers can exploit zero-day vulnerabilities to bypass security controls and gain unauthorized entry.
- Widespread impact: Exploiting a zero day in commonly used software or widely deployed systems can lead to mass compromise.
- Advantage in intelligence gathering: Nation-state threat actors frequently use zero days to extract sensitive intelligence, setting the stage for future attacks.
- Disruption: Threat actors utilize zero-day exploits as a weapon to disrupt operations, with the potential for significant financial and operational repercussions.
Recent Trends in Zero-Day Exploitation
The growing risk of zero-day vulnerabilities stems from several key factors, like the rise in interconnected devices and the wider use of open-source software. Here are some important trends to keep in mind.
1. Enterprise Software in the Crosshairs
Of the 75 zero days exploited in 2024, 44% targeted enterprise systems. Specific cases include:
- Ivanti VPN Zero Days: Ivanti’s Connect Secure VPN devices became a notable target for attackers, with seven zero days discovered, including CVE-2025-0282, which allowed remote code execution. Attackers used these vulnerabilities to inject malware into corporate networks.
- Palo Alto Networks PAN-OS: A command-injection exploit allowed attackers to bypass security controls in enterprise firewalls, exposing sensitive environments to intrusions.
Such examples underscore the need for enterprises, as high-value targets, to proactively address vulnerabilities across their technology stacks.
2. Supply Chain Attacks: The Multiplier Effect
Attackers increasingly target software supply chains, exploiting vulnerabilities at the development stage. For instance:
- MOVEit Transfer and Jenkins Vulnerabilities: A critical path traversal flaw (CVE-2024-23897) within Jenkins could result in arbitrary code execution. If exploited, attackers gain opportunities to insert malware into countless downstream applications.
Supply chains present an ideal target because a single vulnerability in shared components can impact thousands of users across industries.
3. Embedded Software Under Fire
Embedded systems used in everything from medical devices to automotive software share a unique risk in terms of zero-day vulnerabilities due to their reliance on C/C++ code. Research shows that 70% of vulnerabilities in compiled code are memory safety issues, such as buffer overflows and use-after-free errors. Attackers favor these flaws because they are difficult to detect and can cause major disruptions.
Key embedded-system sectors targeted include:
-
- Industrial Control Systems (ICS) and Operational Technology: Attackers compromise OT environments in critical infrastructure, potentially causing large-scale service disruptions.
- Automotive Software: Vulnerabilities found in connected vehicles could allow attackers to take control of core functions or extract user data.
- Medical Devices: Unauthorized access to medical device software can compromise patient treatment and safety.
Ways to Defend Against Zero-Day Vulnerabilities
While it’s impossible to eliminate all vulnerabilities, organizations can take proactive steps to reduce their exposure to zero-day exploits. Below are actionable recommendations for enterprises and developers:
1. Adopt a Zero Trust Architecture
Zero trust assumes no implicit trust between systems. By applying strict access controls and continuously verifying users and devices, enterprises can minimize the impact of zero-day breaches.
2. Perform Dynamic and Static Analysis
Dynamic application security testing (DAST) and static application security testing (SAST) tools can identify vulnerabilities before they’re exploited. Automated testing provides invaluable insights into weak spots.
3. Deploy Runtime Protections
Solutions like runtime exploit prevention can defend applications against zero-day exploitation in live environments. For embedded systems, tools like RunSafe Protect are ideal for neutralizing memory safety vulnerabilities, providing real-time defense against exploits.
4. Strengthen Vulnerability Management Programs
A thorough vulnerability management program helps organizations prioritize high-risk systems, improve patch timelines, and reduce attack surfaces. An important starting point is to generate comprehensive SBOMs that provide visibility into software components.
5. Assess Total Zero-Day Exposure
The Google report found that use-after-free errors, command injection, and cross-site scripting (XSS) were the most frequently exploited vulnerability types. Deploying secure coding practices is one way to address these issues and minimize the number of zero-day vulnerabilities in code.
In the case of memory safety vulnerabilities, understanding potential zero-day exposure through tools like RunSafe’s Risk Reduction Analysis gives organizations unprecedented visibility into their vulnerability landscape. By analyzing return-oriented programming (ROP) chains, the analysis quantifies memory-based zero days and how much organizations can reduce risk when implementing targeted protections where they matter most.
Lessons Learned from Recent Zero-Day Incidents
The continued use of zero days by nation-state actors underscores the importance of adopting a proactive approach to security. Lessons include:
-
-
- Memory safety matters: With many recent exploits stemming from memory flaws, securing codebases in languages like C/C++ is paramount. Runtime protections defend new and legacy code to prevent attackers from taking advantage of these flaws.
- Supply chain hygiene is critical: Minimizing risk in software supply chains requires vetting third-party code carefully and implementing Software Bills of Materials (SBOMs) to identify and address potential weaknesses.
- No one is immune: Enterprises, operational technology vendors, and critical service providers alike must address their unique attack surfaces to avoid becoming the next victim of a zero-day exploit.
-
Gaining the Upper Hand Against Zero-Day Attacks
Nation-state actors and sophisticated criminal groups continue to leverage zero-day vulnerabilities because they consistently deliver results. The Ivanti exploits and other critical vulnerabilities throughout 2024 reinforce the need for secure coding practices and security solutions that take away attackers’ ability to exploit software flaws.
Visibility is also an important way to level the playing field. We know that memory safety flaws remain a predominant source of zero-day exploits. Tools like RunSafe’s Risk Reduction Analysis give organizations the ability to quantify their exposure to CVEs and memory-based zero days.
By analyzing an SBOM or binary, the tool gives organizations visibility into weak spots in their software and the ability to apply remediations before attackers exploit them, transforming their security posture from reactive to proactive. When it comes to zero-day vulnerabilities, knowledge isn’t just power. It’s protection.
The post Zero-Day Vulnerabilities: Exploitation Trends and Lessons Learned appeared first on RunSafe Security.
]]>


